Lots of people Often want to understand what “ransomware” is, scrambling to find information, writing on Google “what is ransomware?”. This article wants to answer all these questions, providing a complete guide, that can be both seen as simple but exhaustive, to let you understand the RaaS phenomenon as a whole.
Authors: Massimiliano Brolli & Serena Carlini
Publication date: 6/19/2021
Translation by: Antonio Piovesan
On all newspapers pages, we hear about huge cyber breaches, millionaire ransoms, cyber-gangs, RaaS and cyber warfare. All of these words can be greatly misunderstood by people who are not specialized in computer science security or even being take people to a big mess. By writing this article, we want to explain what ransomware is, how this highly profitable business of organized cybercrime works, focusing on analyzing the phenomenon all-around, firstly understanding what “affiliation” means, up to the TTPs (techniques, tactics and procedures of attack) and the later extortion.
In common imaginary, cybercrime is thought to be linked to individuals with exceptional cyber skills, but if you want to extort millions of dollars from a large company, you can’t do it all by yourself, you need a “team”, that is:
A group of criminal hackers with several different, advanced and vertical cyber skills, who play in the Dark Web mud and most likely live in Russia.
As a matter of fact, vast majority of cybercriminals do NOT have all the technical skills needed to go it alone and therefore create malware, extort money, penetrate companies. That’s why RaaS come into play: Ransowmare as a Service, cybercriminals who collaborate in a “managed” way, for a single main purpose: extort as much money as possible from a targeted company.
Cybercrime has exploded in recent years because criminals have “specialized” and “under-specialized” so that everyone could focus on specific target on a single stage of hacking and extortion process. All of that is working scarily (sadly) well. In present article, we will explore ransomware as a whole, according to the following index/structure:
RaaS, as previously said, means “Ransomware as a Service”, therefore software and procedures created and sold as a “service” to gain money, a criminal business model where violations are carried out by groups of militarily organized cybercriminals. We will now take a look at this three-tiered pyramid to better understand how it works and the division of duties among cybercriminals.
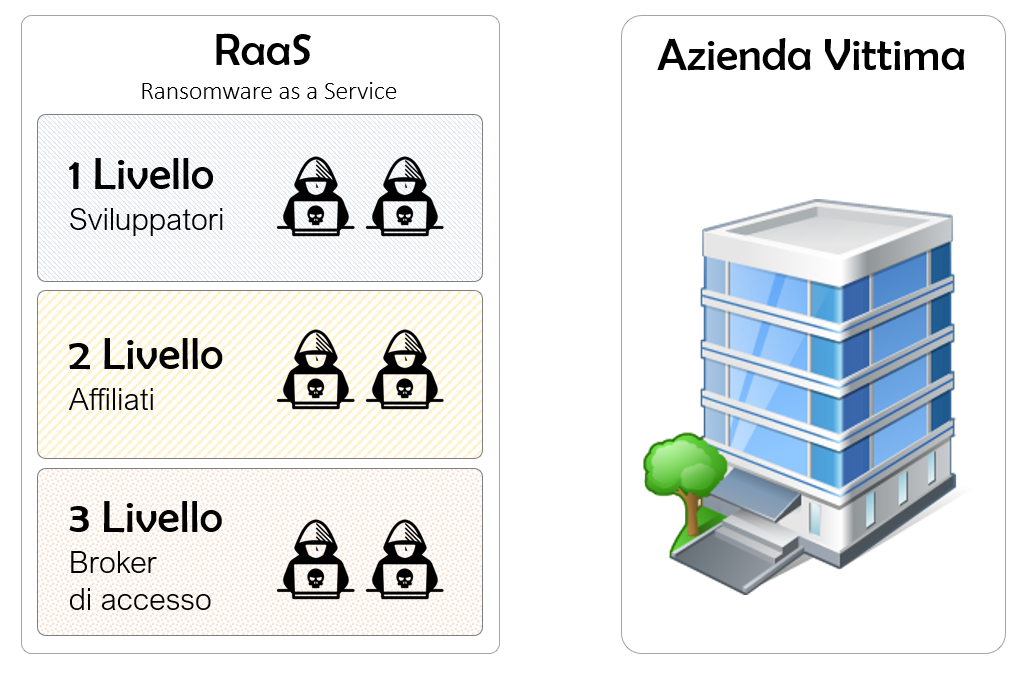
At the very first level we find the “Developers”. They are experts in writing malware, cryptography. They create software and they update them continuously, create tools to be able to provide powerful dashboards and command and control (CC) systems to “affiliates”. These powerful software tools let affiliates manage the entire infection phase that, as we will see, it is the last “active” phase of a ransomware attack, before moving on to extortion. The developers also provide technical support tools to affiliates, so that they can have immediate answers from developers on technical issues.
At the second level “Affiliates” lie. They are other cybercriminals who rent the “ransomware product” from creator developers and conduct the actual attack and extortion activity, accessing victim’ networks and even staying within it for a long time, exfiltrating as much sensitive data as possible in order to allow them an “extra layer of persuasion”, in case when the victim company does not want to pay the ransom note. A second article will go further on that kind of scenario.
So, Affiliates rent ransomware from Developers, accepting or agreeing commission fees within closed underground forums (such as darknet forums on presentation), but also on accessible forums present in the clearweb, such as the well-known XSS.is .
Affiliates, in many cases, in order to access a network of a large company, can buy access from the third and final entity/layer in the RaaS pyramid, namely the Access brokers.
The latter are groups of cybercriminals who violate company networks to gain persistence. They are well versed/trained in penetration testing techniques, and once they gain access to a large organization’s network, they put it up for sale on underground forums for a few thousand dollars. Affiliates are often customers of access brokers, as they allow them to speed up their criminal workflow by providing them with already verified available, low cost, illegal access.
Of course, RaaS exists when there is an organization to be violated. This organization typically has endpoints exposed on the internet that are not properly configured or updated, which allow access brokers to access within their networks.
These companies are often identified through search engines such as Shodan, Zoomeye, Censys, IVRE that allow you to easily point out the resources exposed on the internet by an organization and the exposed related vulnerabilities. As often said, RaaS does not target a specific company, it often affects a large company, only because it leaves a not-fading signature on the web of its intrinsic vulnerabilities. Signature dues to a wrong cyber security posture within it.
We just discovered the whole group of actors in the great RaaS game so, we will delve into the attack model and then we will keep on discovering the ways of iteration between the three levels of RaaS pyramid. But first let’s start showing you the numbered graphic of the attack path to make it easier for you to read.
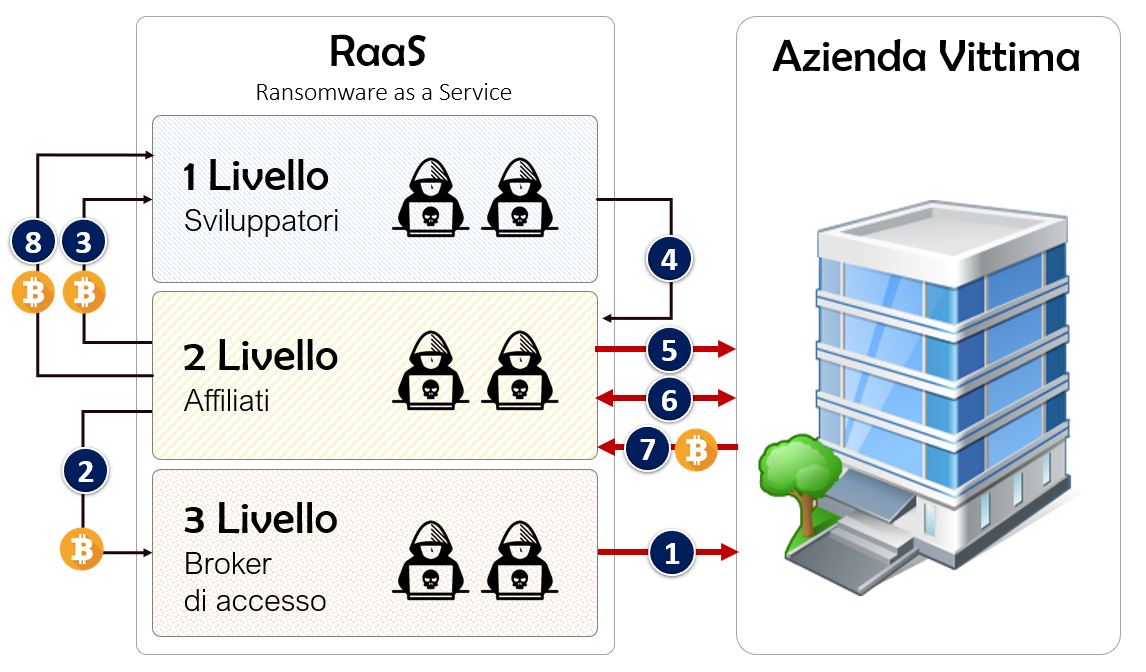
Now we will understand precisely all the steps that are carried out in this perfect criminal “military” organization that will allow, if everything works well as needed, to extort huge amounts of money.
All ransom payments made by victims are split between an affiliate and the ransomware developer. In the DarkSide case (DarkSide is the ransomware that locked Colonial Pipeline pipelines), malware developer took 25% for ransoms under $ 500,000 threshold, but those fees dropped to 10% for ransoms greater than $ 5 million.
All of this rules are defined as policies described in the “developers” blogs or in underground forums such as XSS, a forum we talked about earlier.
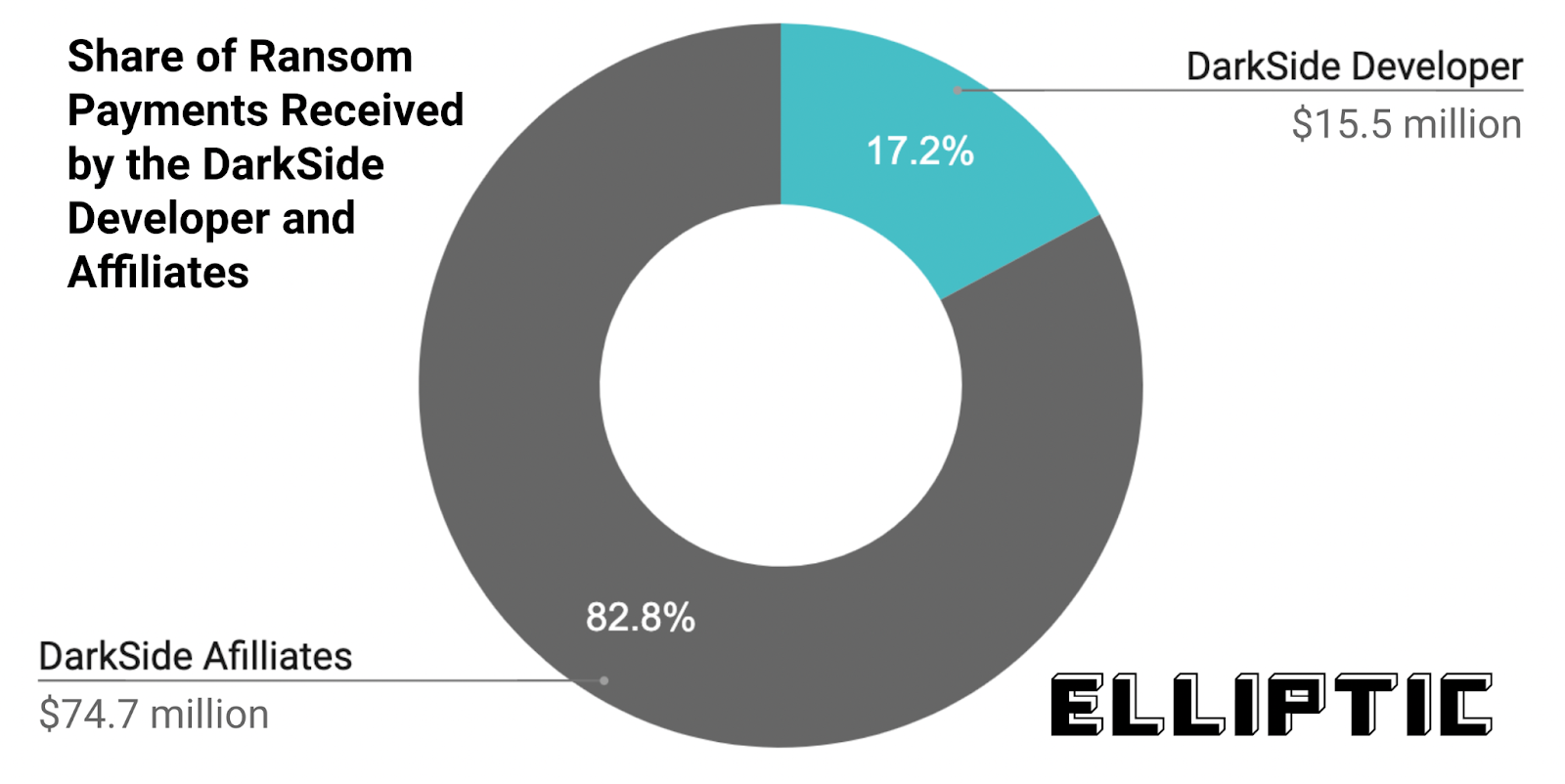
This ransom payments division can be seen very clearly on blockchains, with the different actions separating Bitcoin wallets controlled by Affiliates from Developers ones. If we talk about DarkSide, Developers have received Bitcoin for a value of 15.5 million dollars (17%), remaining 74.7 million dollars (83%) being gained by various Affiliates.
Totally, just over $ 90 million Bitcoin ransom payments were payed to DarkSide gang from 47 separate wallets.
This is an index that clearly shows what was the number of violated victims who paid a ransom. For instance, according to DarkTracer, 99 organizations were infected by DarkSide malware, suggesting that around 47% victims paid a ransom with an average payment of $ 1.9 million.
As said, RaaS mainly revolves around “Developers” and “Affiliates”, but there are also other figures who are starting to take shape making RaaS model a real business organization, with diversified roles and multiple outsourcing activities.
Cybercriminals who develop infrastructure that are sold back to Ransomware developers to speed up their software development cycle, such as cryptocurrency payment systems, blogs, and so on.
These are full-fledged criminal software components, purchased by Ransomware Developers. They use these components within their software solutions, just as if Developers were designing legitimate software and components were third-party software.
In order to maximize profit in when companies DO NOT WANT to pay ransoms and to maximize the efforts made to hack illegally, and encrypt a particular company, RaaS model can rely on people who specialize in managing “negotiations” between victim companies and RaaS groups.
Several actors are using actors who manage negotiation aspects, as well as building pressure on victim companies, e.g., through calls, DDoS (Distributed Denial-of-Service) attacks and threats including the loss of stolen information. During a ransomware attack, in short, people specialized in pure “extortion”, who can facilitate payment activity by the company.
Ransomware, starting from Joseph Popp’s Trojan AIDS considered the first ransomware in history, we talked about in an past old article, up to Wanna Cry and the sophisticated Maze, REvil, Darkside ransomwares, have undergone many changes and innovations, both technically and in ways of extortion.
First we need to do some history to understand the three extortion tactics used to date. They are:
As previously stated, “Access brokers” have great offensive technical skills: they actually manage in violating an organization, so it is up to them to penetrate the company system and resell the access points to “Affiliates”, who will stay within victim networks until they found sensitive data, useful for blackmailing victim through double or three-tiered extortion. Double extortion is a method introduced by Maze (a no longer active today cyber-gang) at the end of 2019.
Everyone seems to agree that tactics, techniques and procedures used by “Affiliates” and “Access brokers” reflect a common mode of action that incorporates a mix of native Windows functionality, commodity malware and red-team tools ready to use like Cobalt Strike, Mimikatz, powershell and .NET backdoor.
“Access brokers” have good skills in penetration-testing activities while “Affiliates” move sideways to access infrastructures containing most valuable data, such as research and development departments projects, finance and control data, up to Human Resource office. The will is obtaining as much “sensitive” information as possible from the victim organization.
Once persistence is established, criminal gangs can stay within an organization up to 45 days, but it is known that the number of days can reach up to 90 (3 months, as a matter of fact we can compare this crime scene to an APT attack, APT meaning Advanced persistent threat). They do start the ransomware payload only after having collected as much information as possible useful for a second extortion.
So we have to understand that, when the cyber attack is perceived by the users (if no access has been detected previously), that stage is the end of the “technical” work, carried out by cybercriminals.
Ransomware now enters the scene, encrypts data present on the servers and displays a program screen that states the computer has been infected, proceeding with the price to decrypt data and the time by when it will be necessary to pay the ransom. In Ransomware like REvil (Sodinokibi) case, after that period, the cyber-gang doubles ransom cost.
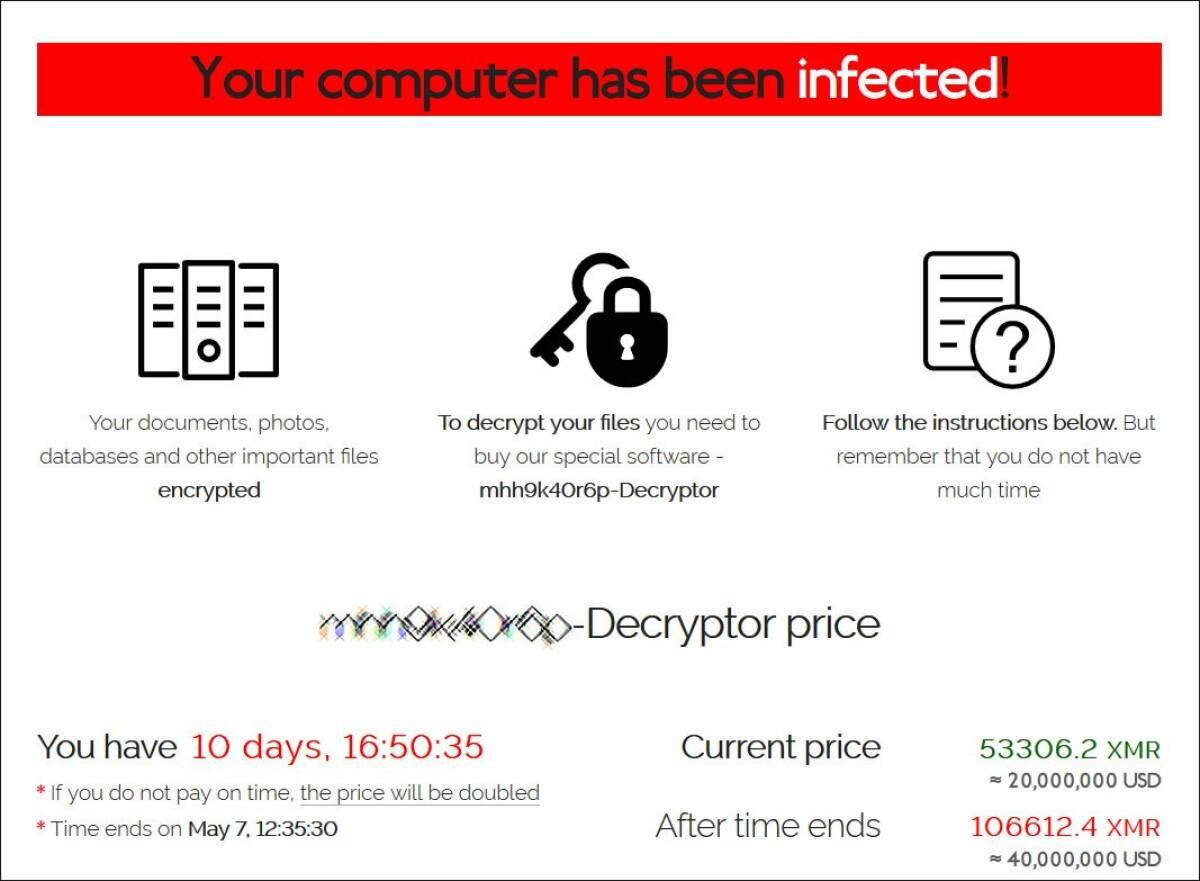
Schermata di blocco del ransomware REvil (Sodinokibi)
Moreover, a file is produced (even if there are many forms of action); the file states/orders what the organization will have to do to obtain encryption keys that will allow to decrypt data. Specifically, it is reported that “Companies HAVE NOT to waste their time”.
It also contains instructions for accessing the site in the onion network safely, specifying that the usage of VPNs and TOR browser is recommended. Once you have accessed the .onion site with TOR browser, you will need to specify a code generally displayed by the program screen on your computer screen and then proceed with ransom payment.
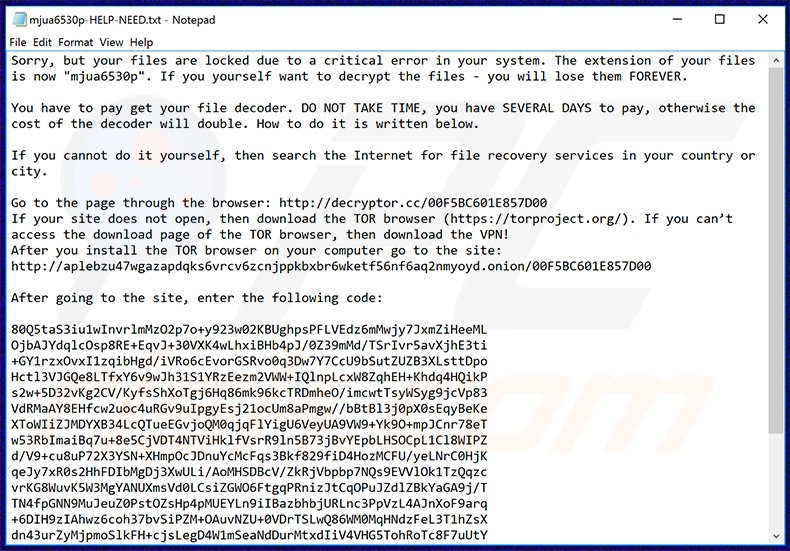
File di testo che riporta le istruzione di recupero.
Recently, a multitude of new extortion techniques have been observed, meant to increase pressure on the organization and so forcing it to pay the ransom.
E.g., in the Vastaamo (a Finnish psychiatric clinic) accident, after encrypting data, Affiliates proceeded to inform Vastaamo customers that their medical records would have been made public. As a matter of fact, 300 medical records were published on darweb and the company went bankrupt.
In other cases, there have been phone calls from affiliates to journalists to inform them that a particular organization has been hit by ransomware, effectively increasing news circulation and implying pressure on the organization.
In other cases, there was also pressure on companies’ top managers by threatening them to publish sensitive information taken from their own PCs, this while the company was evaluating the payment of the ransomware ransom.
Another truly insane example reported by Mandiant relates to a DarkSide affiliate who was able to exfiltrate the company’s IT insurance policy. This information was obviously exploited by the cyber-gang during the ransom negotiation process, refusing to reduce the amount, given its knowledge of the policy limits.
The art of deception has always been the basis of cybercrime activities at all levels, so much so that many books have been written on spoofing and deception techniques, and therefore on how to fool others into believing that you’ve been attacked by a different subject.
Determining what country or government cyber-gangs can work for has become very difficult to be understood in recent years, as many groups specifically try to “leave traces” to frame other countries or governments.
Codes alone are not enough to identify attackers’ nationality, as cybercriminals can deliberately leave false traces, what are called “false flags” in military jargon.
By saying “false flag”, we mean a secret tactic pursued in military operations, intelligence and/or espionage activities, generally conducted by governments, secret services, designed to appear as being pursued by other entities and organizations, including through infiltration or espionage within the latter.
This can be read on Wikipedia as a “military concept”, and this obviously was acquired and implemented in cyber warfare and ransomware operations by inserting specific “traces” within the malware, capable of influencing an analyst in making telling, incorrectly, ransomware attack origin.
Russian is a language used in many countries of the former USSR, especially in the field of information technology, so today it could be quite difficult drawing conclusions about a malware footprint through comments, error messages, language / country based restrictions, CC (command and control systems) IP Addresses and more.
Many groups working for governments in various countries are specifically trying to leave specially crafted artifacts in the code to sidetrack analysts from their true identities and origin countries.
They are techniques of imitation to make believe that the attack has been launched by a group of another state, or to simulate and impersonate precisely a known threat actor, to mislead their traces. Many groups have analyzed the malware of other competitors to report artifacts within their binary files that could lead to them.
As we have seen in these two articles, RaaS is a highly specialized and organized criminal phenomenon, where information bargaining power has an impressive value today.

The geopolitical landscape of this last period makes these cyber attacks – especially if directed towards countries critical systems – a national security problem and this leads governments to manage them with the utmost attention: attention that is not appreciated by cyber criminals.
Furthermore, given the difficulty in identifying the origin of a ransomware attack (it could be Russia, China or North Korea, just for instance), that can lead to a destabilization of the geopolitical balances built previously and the triggering of potential escalation.
Ransomware phenomenon is on the rise, this is because it is extremely profitable and low cost. We therefore expect that extortion tactics used by cyber-gangs will keep on evolving in the coming years in a way that is not foreseeable today: newspapers front pages will begin to talk about ransomware.
For this reason it is essential (as often reported on Red Hot Cyber pages) to regulate cyber warfare by freeing the mind from what “was” the Tallin Manual, trying to write a truly international treaty and not just written for NATO and FiveEyes alliance benefit.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…