
ESET researchers have discovered a zero-day exploit targeting Telegram for Android. An exploit called EvilVideo appeared for sale on an underground forum on June 6, 2024. Attackers exploited this vulnerability to distribute malicious files through Telegram channels, groups, and chats, disguising them as media files.
Specialists managed to obtain an example of the exploit, which allowed them to analyze it and report the problem on Telegram on June 26. An update fixing the vulnerability was released on July 11, 2024 in Telegram versions 10.14.5 and later.
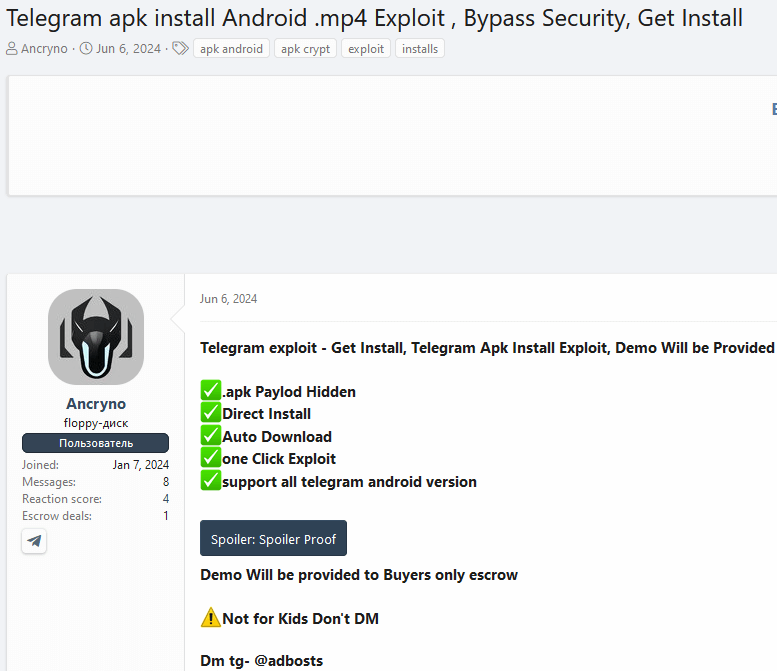
The vulnerability allowed attackers to send malicious files that looked like videos in unprotected versions of Telegram for Android (10.14.4 and earlier). The exploit was found on an underground forum, where the vendor demonstrated its work in a public Telegram channel.
This allowed researchers to obtain the malicious file and test it.
The analysis showed that the exploit exploited the ability to create malicious files that were displayed as media previews. While attempting to play such a “video,” Telegram reported that the file could not be played and suggested using an external player.
By clicking the “Open” button, the user was asked to install a malicious application disguised as a player.
Telegram has fixed the vulnerability in version 10.14.5. Media file previews now correctly indicate that the file is an application and not a video.
The exploit was tested on the web and desktop versions of Telegram for Windows, but it did not work. In both cases, the file was recognized as multimedia and posed no threat.
It was also discovered that the exploit vendor offered an encryption service for Android, making malicious files invisible to antiviruses. This service has been advertised on the same underground forum since January 2024.
After discovering the vulnerability and reporting it to Telegram, the problem was fixed. Users are advised to update the application to the latest version to protect themselves from potential threats.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…