
Introduction Xehook Stealer is a sophisticated malware targeting Windows operating systems, first discovered in January 2024. Within a year, Xehook has rapidly gained notoriety for its advanced data collection capabilities and support for over 110 cryptocurrencies and 2FA extensions.
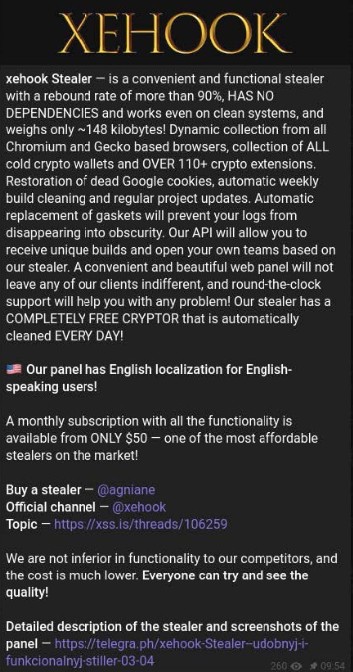
Starting today, the future of the project may undergo a significant change, as two sales announcements have been found for the project, one on the well-known forum xss.is and the other on its own Telegram channel.
Technical Features Xehook Stealer is written in .NET and stands out for its dynamic data collection capabilities from Chromium and Gecko-based browsers. Key features include:
Distribution Methods Xehook Stealer is distributed through various vectors, including:
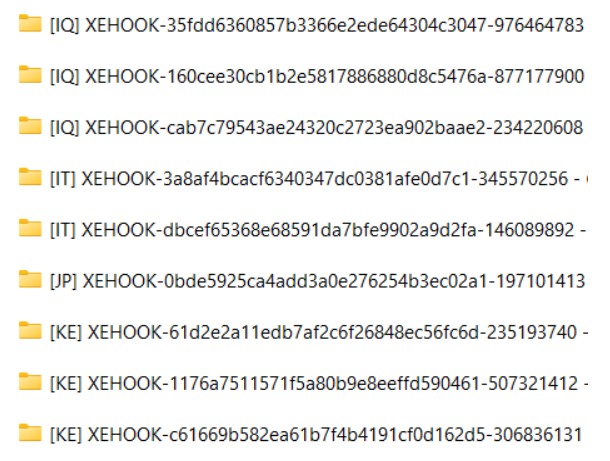
Dump of Several Malware Stealer Samples by Country
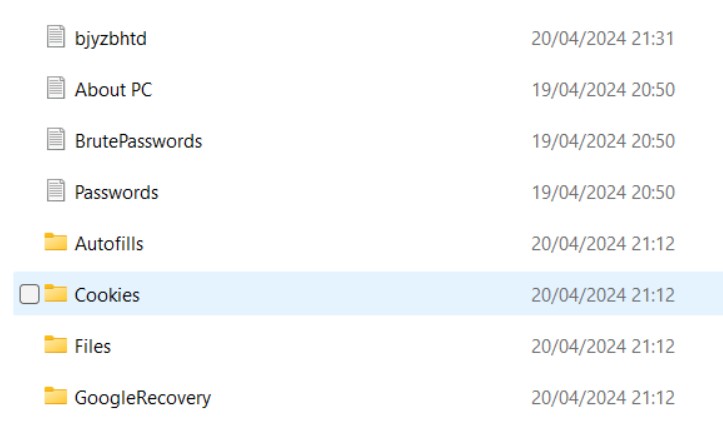
Content of Data Captured by the Malware
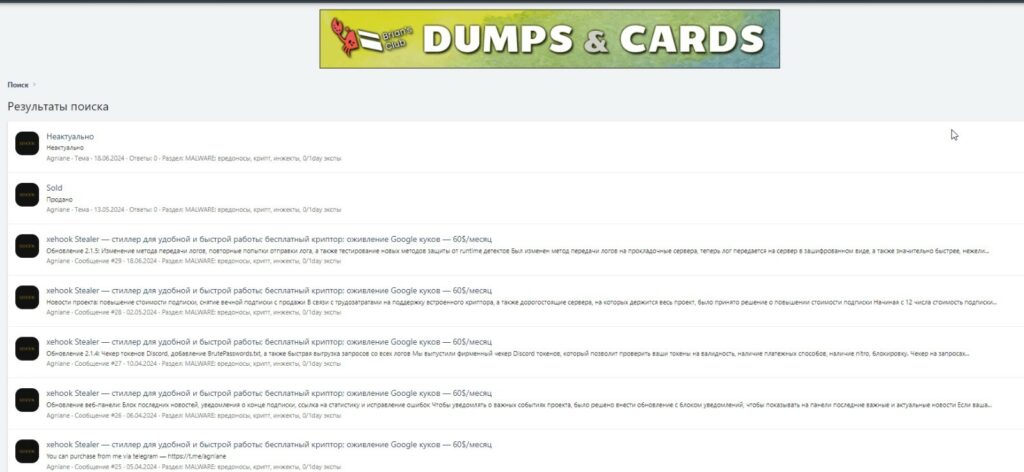
Announcement on XSS.is Forum The Xehook project sale post also appeared on the well-known forum xss.is.
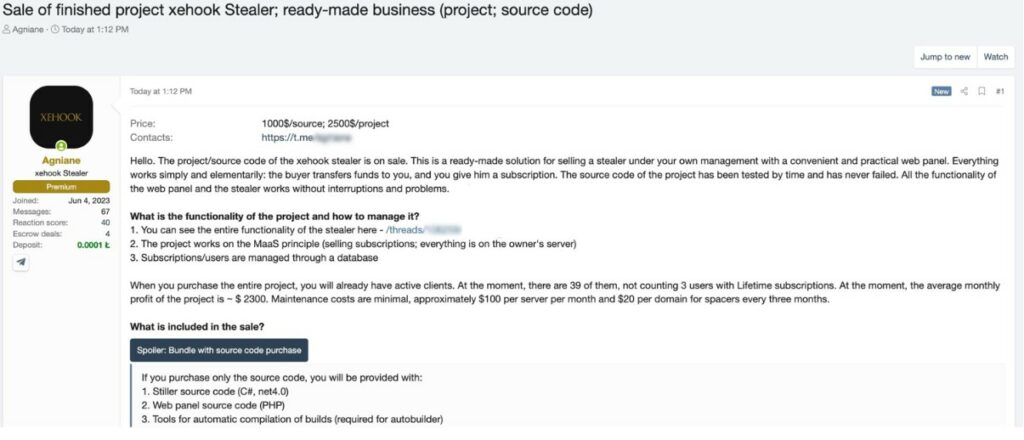
After a few hours, the post was removed, likely because the project was sold. This rapid change indicates strong interest and the possible transition to a new owner, which could lead to further developments in the threat landscape.
In a recent post on their Telegram channel, written in Russian, the Xehook developers announced the sale of the project.
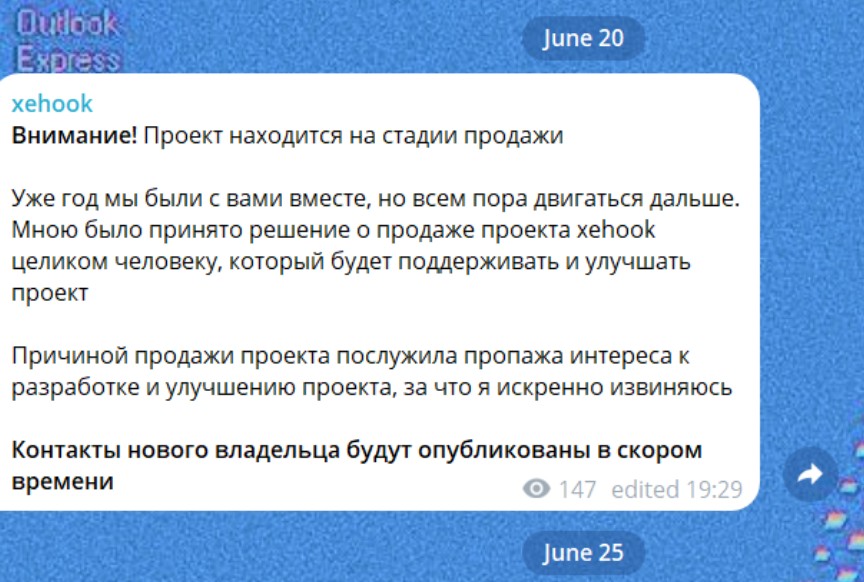
The message reads: “Attention! The project is in the process of being sold. We have been together with you for a year, but it’s time to move on. I decided to sell the Xehook project entirely to a person who will support and improve it. The reason for the sale is the loss of interest in developing and improving the project, for which I sincerely apologize. The new owner’s contact details will be published shortly.”
“Attention! The project is in the process of being sold. We have been together with you for a year, but it’s time to move on. I have decided to sell the Xehook project entirely to a person who will support and improve it. The reason for the sale is the loss of interest in developing and improving the project, for which I sincerely apologize. The new owner’s contact details will be published shortly.”
The Infostealer Phenomenon Infostealers like Xehook represent a particularly dangerous category of malware designed to steal sensitive information from infected users. In 2023, infostealer attacks increased significantly, with a 40% rise compared to the previous year. This type of malware is responsible for compromising millions of accounts and exfiltrating a wide range of personal and financial data. The figures related to infostealers highlight the extent of the problem:
These numbers underscore the need for strengthened security measures and increased awareness of the threats posed by infostealers.
Implications of the Announcement This announcement marks a significant turning point for the future of Xehook. The sale of the project could lead to changes in the management and development of the malware. Users and potential victims need to be aware of any new developments or variants of the malware that may emerge under new management.
Conclusion Xehook Stealer represents an advanced threat in the cybercrime landscape, with sophisticated capabilities that facilitate its spread and effectiveness. The recent announcement of the project’s sale adds another layer of uncertainty regarding its future. It is essential to remain vigilant and adopt adequate security measures to protect against this type of threat.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
