
On November 5th, 2024, the next President and Vice President of the United States of America will be elected, as well as 1/3 of the U.S. Senators and all 435 Members of the U.S. House of Representatives will be chosen. In this context, influence operations through digital echo chambers – such as digital platforms and social media – can play a critical role, shaping narratives that can influence people’s opinions, who are exposed to different types of political, scientific, cultural, conspiracy or extremist content.
We already put the spotlight on a 2024 marked by provocations in the great march to the polls in some 76 countries.
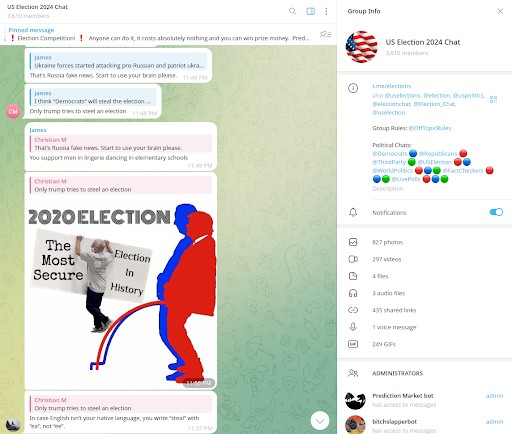
Social media, instant messaging (IM) services and digital media channels play a crucial role: as traditional media consumption declines, many voters turn to social media for news and updates, where active accounts produce ad hoc content to influence public perception – which lacks the keys to critical thinking and informed decisions – and ultimately election results. Such content, which at first glance may seem naive, reveals instead that there is an organizational effort behind it to produce it and make it available online or easily sharable via mobile or email. It is important to highlight how an echo chamber represents an environment where a person only encounters information or opinions that reflect and reinforce their own ideas and confirmation bias.
Another critical threat is the erosion of trust in democratic institutions and processes: this facilitates the amplification of narratives whose sole intent is to produce chaos.
In order to create chaos, psy-ops and cyber operations are used in combination with traditional espionage tools. This includes:
As we see, threats take on various forms, followed by disinformation, content manipulation, hacking and hybrid warfare, involving a wide range of entities, also thanks to the numerous digital tools available today and used to amplify the message.
Added to this are non-traditional forms of espionage aimed at acquiring information or gaining access to critical infrastructure and supply chains or to new surveillance technologies, systems, networks and even foreign investments. This also highlights the need for an approach to improve public awareness and rebuild their trust in democratic institutions.
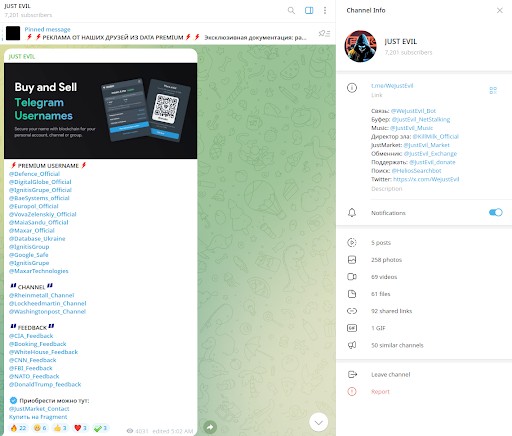
In this regard, Resecurity – an American cybersecurity and threat intelligence company with headquarters in Los Angeles, California and of which we mention Gene Yoo CEO and Shawn Loveland COO – has detected a substantial increase in the distribution of political content related to the 2024 US elections through social media networks, particularly from foreign jurisdictions. On October 5, 2024, Resecurity identified multiple accounts for sale on Telegram that were impersonating government entities, including the White House, the FBI and the CIA, as well as popular media outlets such as CNN and the Washington Post.
In the report “Digital Echo Chambers and Erosion of Trust – Key Threats to the US Elections” Resecurity” discusses the significant threats posed by the erosion of trust in the coming US elections caused by digital echo chambers.
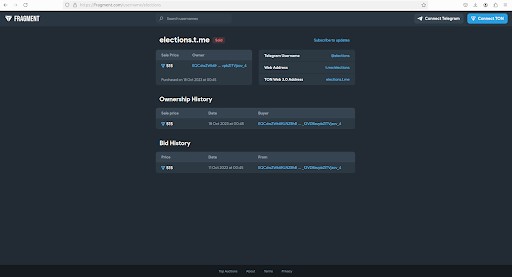
Multiple Telegram accounts with the U.S. elections narrative have also been registered and offered for sale between 10 TON ($51) and 2028 TON ($2290) on the marketplace Fragment that can attract interest from political consultancies and foreign adversaries aiming to target a specific segment of the audience. One such account (@elections) was sold on October 18, 2023 – almost a year before the elections.
Influence operations are not limited just to foreign entities but include domestic organizations and actors as well. In recent weeks, there has been a proliferation of fake pictures, videos, and narratives including targeted cyber attacks “under false flag to induce sentiment”.
The scenario at a global level seems to become even more complex if we look for example at Moldova – divided between East and West – where the yes vote has just passed in the referendum for its integration into the European Union. Analysts had already warned of a “large-scale hybrid war” originating from the social network Vkontakte (VK) regarding the presidential election and the discredit to Maia Sandu, who for now has won the first round with 42.45 percent of the votes and who is preparing for the runoff on November 3 with Alexandr Stoianoglo of the Partidul Socialiștilor din Republica Moldova.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
