
The legendary Jeans retailer Levi Strauss & Co. identified a significant data breach that affected over 72,000 customers. The incident was discovered on June 13th, 2024 and it was the result of a credential stuffing attack, where attackers used combination of e-mails and passwords found from third parties sources to gain unauthorized access to victim accounts. The compromised data included names, order history, emails and addresses, exposing potential additional security risks. The breach involved exactly 72.231 unique costumers. Currently, there’s no evidence of the attackers’ presence on the Dark Web. The company’s statement is the only confirmation of the credential stuffing attack.
In addition to personal data, the breach may have exposed (partial) payment information for costumer who saved their payment methods. This includes the last four digits of the card number, card type and expiration date. Levi Strauss stated that “fraudulent orders do not appear to have been made with the exposed data. Our systems do not authorize the use of saved payment methods without a secondary authentication mechanism”. The investigations have been made by the Office of the Maine Attorney General (OAG) : “13th June we have identified a unusual traffic peak on our website. Our investigation showed characteristic related to credential stuffing attack where bad actors obtained credentials from external sources, using bots to test these credentials on another website, in this case www.levi.com“
Credential stuffing is a type of brute-force attack where attackers use previously breached credentials from one service to attempt unauthorized access to accounts on a different, unrelated service
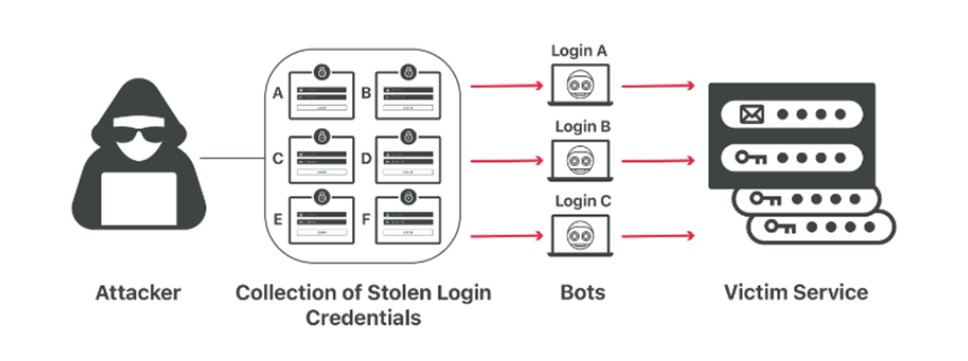
Such attacks are not uncommon, many users tends to re-use same credentials on different services. This is why attackers commonly purchase compromised credentials and try them on different websites. The results is tipically a new wave of compromised accounts that can be exploited by bad actors for extortion accounts or reselling into dark web marketplaces. To mitigate this breach, Levi Strauss disabled all credential potentially affected by unauthorized access and subsequently forced the password reset for costumers. Levi Strauss also recommends that costumers choose unique passwords to prevent future credential stuffing attacks.
Levi Strauss & Co. highlighted the importance of unique complex passwords for each online service account to stop unauthorized access and brute force attacks. Customers were also advised to do the same for their accounts on services unrelated to Levi Strauss. The company also recommended that costumers monitor their bank accounts for unusual activities and consult the Federal Trade Commission’s Guide on passwords policies.
Levi Strauss & Co. outlined its commitment to data and privacy protection for its customers. The management team receives regular updates about privacy and data protection, all employees are required to complete mandatory security training on an annual basis. Despite all the measures in play, this breach underscores the ongoing challenges companies face in protecting data from increasingly sophisticated security threats. This recent data breach serves as a stark reminder of the digital vulnerabilities and the critical needs for robust security solutions to safeguard systems from unauthorized access.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
