
Recently, a threat actor allegedly leaked a database containing information on Electronic Arts (EA) employees from 2022. The data breach was confirmed by the threat actor himself, who explained the reasons behind his decision to make the data public.
Currently, we are unable to accurately confirm the veracity of the breach, as no press release has been issued on the official website regarding the incident. Therefore, this article should be used as an “intelligence source.”
The threat actor stated: “I recently noticed that a new burner account was created to try and sell this data breach, but it has already passed around hands (4-5 people). Since they are claiming they only want to sell it once to one buyer, I will leak it myself. I don’t know how this person got the database, but it was never meant to be for sale.”
This statement highlights a certain degree of discontent towards the actions of third parties who were trying to monetize the breach. The actor further added: “I don’t feel like typing out details of the breach, so I am stealing info from another post.”
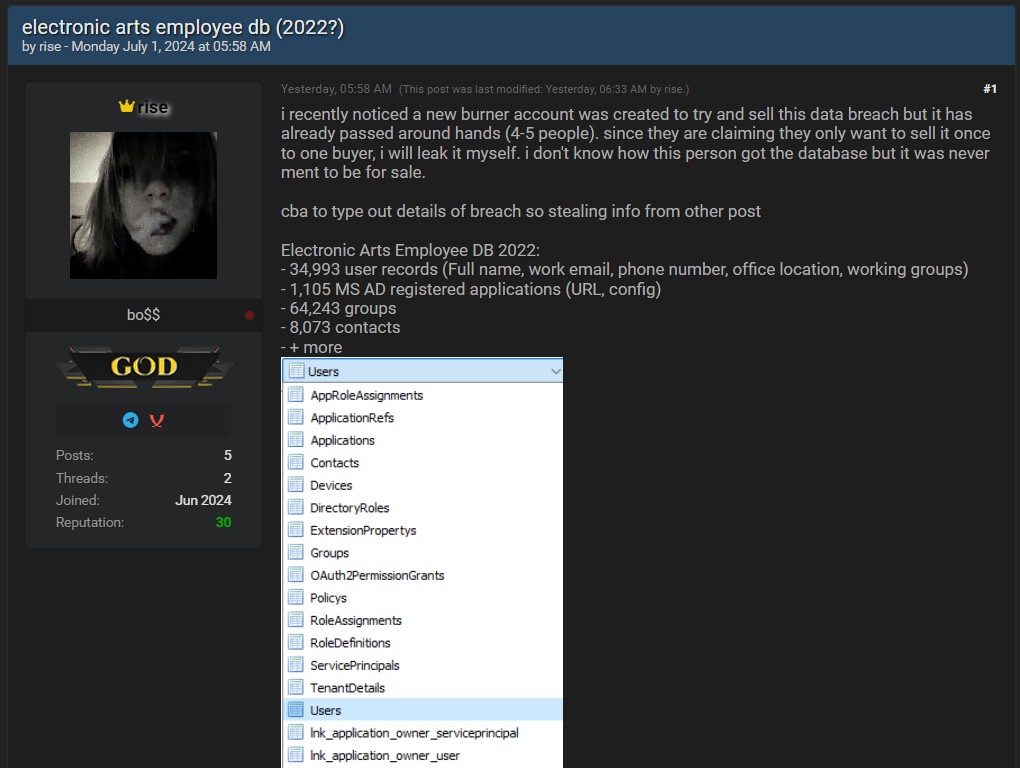
The leaked database contains a wide variety of sensitive information, divided into several files. Here is an overview of the compromised data:
These files represent a goldmine of information for anyone looking to exploit the data for illegal activities, such as phishing or other forms of cyberattacks.
At this time, we cannot precisely confirm the veracity of the breach, as the organization has not yet released any official press statement on its website regarding the incident. Therefore, this article should be considered an ‘intelligence source.’
The EA data breach serves as a serious wake-up call for all companies, highlighting the importance of adopting robust security measures to protect sensitive information. As EA deals with the consequences of this data leak, the entire industry must reflect on the need to strengthen its resilience against cyber threats.
As is our practice, we always leave space for a statement from the company if they wish to provide us with updates on the matter. We would be pleased to publish such information with a specific article highlighting the issue.
RHC Dark Lab will monitor the evolution of the situation to publish further news on the blog, should there be any substantial updates. If there are individuals with knowledge of the facts who wish to provide information anonymously, they can use the whistleblower’s encrypted email.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
