
Nel mondo della sicurezza informatica, le notizie sui data breach sono all’ordine del giorno. Recentemente, una nuova presunta violazione ha fatto scalpore: il moderatore di BreachForums, noto come IntelBroker, ha affermato di aver divulgato i codici sorgente (SRC) di vari prodotti di Rapid4Cloud.
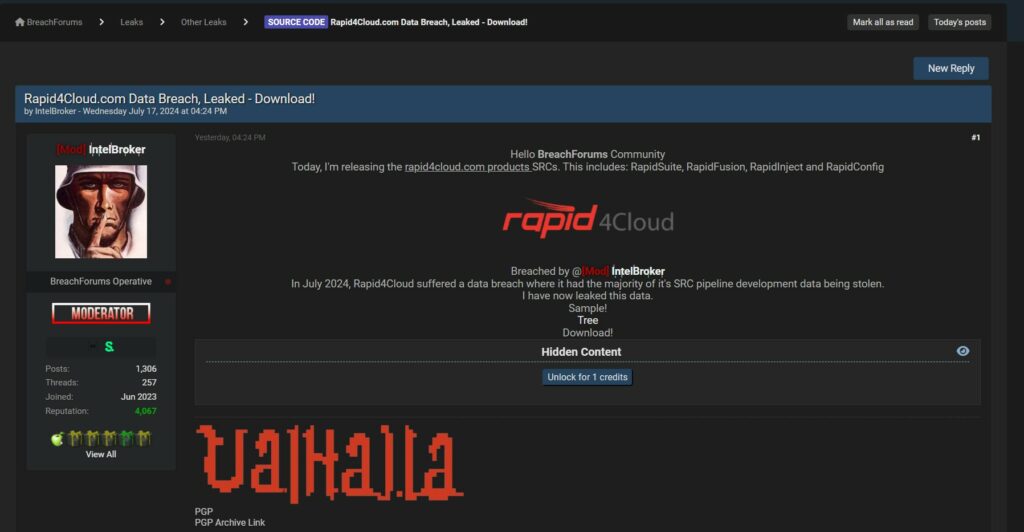
Secondo quanto riportato da IntelBroker sul forum, i dati rubati includerebbero i codici sorgente di diverse suite di Rapid4Cloud, nello specifico:
La dichiarazione di IntelBroker è avvenuta il 17 luglio 2024, specificando che la fuga di dati sarebbe avvenuta nel corso dello stesso mese. IntelBroker ha fornito link per il download dei dati, suggerendo che una quantità significativa di informazioni sensibili è ora disponibile pubblicamente.
Intelbroker è un individuo (o un gruppo di hacker criminali) operante nel dark web, tra le risorse underground quali xss, Breachforums, Exposed. Si tratta di un attore di minacce operante nel gruppo di hacker “Cyberniggers“, ed è attivo sia nelle categorie di hacktivismo che nella criminalità informatica, soprattutto come Inital Access Broker (IaB).
Se la fuga di dati dovesse essere confermata, le implicazioni per Rapid4Cloud potrebbero essere significative. La divulgazione dei codici sorgente potrebbe mettere a rischio la sicurezza dei loro prodotti e compromettere la fiducia dei clienti. Inoltre, i criminali informatici potrebbero sfruttare le vulnerabilità presenti nel codice per attacchi futuri.
L’affermazione di IntelBroker riguardo la fuga di dati di Rapid4Cloud ha sollevato preoccupazioni significative nel campo della sicurezza informatica. Tuttavia, fino a quando Rapid4Cloud non rilascerà una dichiarazione ufficiale, questa notizia deve essere considerata come una fonte di intelligence piuttosto che una conferma definitiva della violazione. Nel frattempo, è essenziale che le aziende continuino a migliorare le loro misure di sicurezza per proteggere i propri dati sensibili.
Come nostra consuetudine, lasciamo sempre spazio ad una dichiarazione da parte dell’azienda qualora voglia darci degli aggiornamenti sulla vicenda. Saremo lieti di pubblicare tali informazioni con uno specifico articolo dando risalto alla questione.
RHC monitorerà l’evoluzione della vicenda in modo da pubblicare ulteriori news sul blog, qualora ci fossero novità sostanziali. Qualora ci siano persone informate sui fatti che volessero fornire informazioni in modo anonimo possono utilizzare la mail crittografata del whistleblower.
Nota: Questo articolo è basato su informazioni non confermate e dovrebbe essere considerato come una potenziale fonte di intelligence piuttosto che una verifica definitiva dell’accaduto.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…