
A serious security incident appears to have hit the Virginia Department of Elections, causing the unauthorised dissemination of a large election database. The attack, claimed by a user known as IntelBroker, was made public through an online forum dedicated to data breaches.
The Virginia Department of Elections is the body responsible for administering elections in the state of Virginia. This department ensures that all elections are conducted fairly, transparently, and in compliance with state and federal laws. It oversees voter registration, supervises local and state elections, and maintains the integrity of the electoral process through secure data management and election staff training.
Currently, we cannot precisely confirm the accuracy of the reported breach, as the organization has not yet issued an official press release on their website regarding the incident. Therefore, this article should be considered as an ‘intelligence source’.
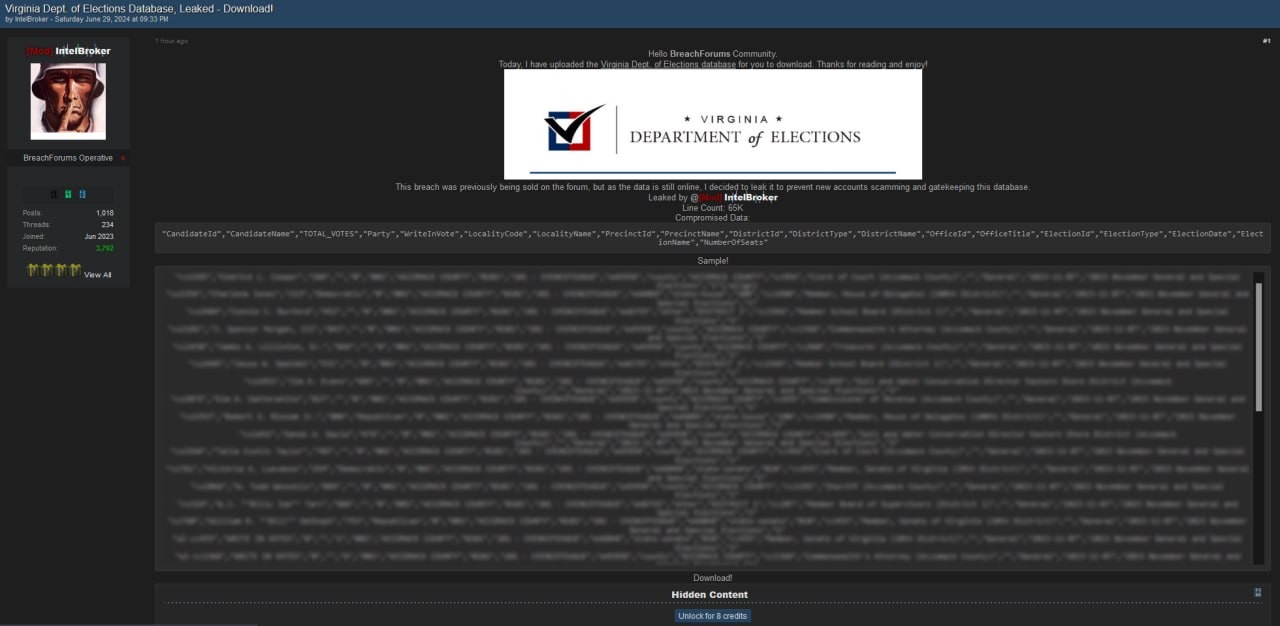
According to reports, the compromised database contained detailed information about electoral candidates. IntelBroker, the user who claimed responsibility for the attack, stated that the database had previously been sold on the forum. However, they decided to make it public to prevent further fraud by new accounts that could have taken advantage of this information. Currently, we cannot precisely confirm the accuracy of the reported information, as no official press release regarding the incident has been issued on the department’s website.
IntelBroker is a threat actor operating on the dark web, associated with the CyberNiggers group. Specializing in selling access to compromised systems, IntelBroker has orchestrated attacks against companies such as Zscaler and Europol.
Active on underground forums like XSS, Breachforums, and Exposed, IntelBroker has sold sensitive data at surprisingly low prices. IntelBroker also develops ransomware and is known for their ability to compromise high-profile systems, acting as an Initial Access Broker.
However, the information published by IntelBroker turned out to be wrong at times, with reports attributing attacks to companies other than those actually affected.
The leaked database includes a total of 65,000 rows of data, with details such as:
The dissemination of such sensitive information raises serious questions about the security of electoral data and the privacy of candidates. The leaked information can be used for malicious purposes, influencing public trust in the electoral system.
This incident underscores the importance of robust security for electoral data. Institutions must adopt preventive and reactive measures to protect sensitive information and maintain the integrity of the electoral process. Voters need to have confidence that their data and the electoral system as a whole are protected against such breaches.
As is our practice, we always leave space for a statement from the organization should they wish to provide updates on the matter. We will be happy to publish such information with a specific article highlighting the issue. RHC Dark Lab will monitor the situation to publish further news on the blog, should there be substantial updates. If there are individuals informed about the facts who wish to provide information anonymously, they can use the whistleblower’s encrypted email.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
