
In principio c’era il Verbo…
i computer, prima di passare all’era del transistor, erano macchine ciclopiche, pesanti, affamate di elettricità, le quali utilizzavano la valvole termoionica o tubi sottovuoto per funzionare, e quindi eseguire capacità di calcolo ridottissime.
Parliamo ad esempio dell’ENIAC, del 1945, il primo computer general-purpose digitale creato per consentire di risolvere problemi sul calcolo delle curve balistiche dei proiettili.
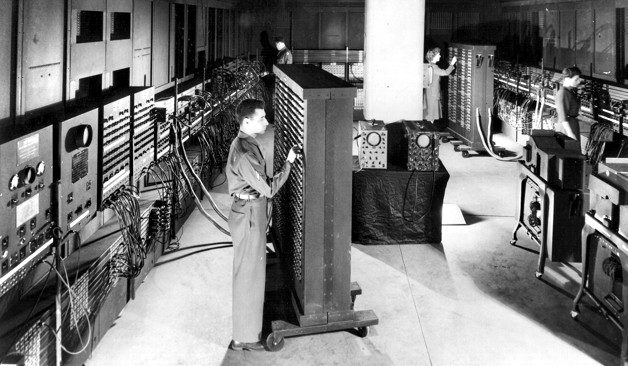
L’Electronic Numerical Integrator and Computer (ENIAC)
Pensate che questo gigantesco computer occupava lo spazio di 1800 piedi quadrati e consumava circa 150 kilowatt di potenza e si narra che la prima volta che venne acceso, tutte le luci di un quartiere di Filadelfia si spensero a causa dell’enorme carico elettrico.
Ma non fu il solo, ci furono l’EDVAC, l’UNIVAC e tutta la saga dei grandi computer a transistor quali gli IBM, i DEC PDP, partendo dal PDP-1 di cui ne abbiamo parlato in un precedente articolo, utilizzato da Steve Russel per la realizzazione del primo videogioco munito di Gamepad dal titolo SpaceWar! quando militava presso il Tech Model Railroad Club dell’MIT.
Insomma, ne vennero prodotti molti di questo grandi computer, dalla IBM, dalla DEC, dalla General Electric, ma ci fermeremo a questa ultima e precisamente al GE-600, ovvero una famiglia di computer mainframe originari degli anni ’60.

Su quest’ultimo computer, vennero avviati nel 1964, degli sviluppi importanti, per la produzione di un sistema operativo chiamato Multics, acronimo di Multiplexed Information and Computing Service, che possiamo senza ombra di dubbio citare come la genesi dei sistemi operativi moderni.
Venne creato da uno sforzo congiunto tra il MIT Project MAC, guidato dal grande Fernando Corbatò (che abbiamo già incontrato in un altro video su redhotcyber in quanto inventore della password e del profilo utente), assieme alla General Electric e ai laboratori Bell.
Il sistema Multics era un sistema operativo mainframe time-sharing davvero innovativo per quel periodo ed era scritto in PL/I, un linguaggio di programmazione di terza generazione sviluppato all’inizio degli anni ’60 come alternativa all’Assembler.
E’ stato il primo sistema operativo ad introdurre un file system gerarchico, come nei computer di oggi, ad avere un processore di comandi come le comuni shell, oltre ad introdurre il concetto di Access Control List e la on-line reconfiguration, quella capacità di aggiungere o rimuovere banchi di memoria e dischi a caldo.
Multics, come abbiamo detto, introdusse il concetto di file system gerarchico e la directory principale del sistema operativo venne chiamava “root”. Root in Multics si intendeva la radice dell’alberatura delle directory che erano memorizzate sul volume fisico che conteneva la partizione dove era presente la directory root.

Nel 1969, come tutti sappiamo Ken Thompson iniziò a scrivere la prima versione del sistema operativo UNIX in codice assembler su un PDP-7, presso i laboratori Bell, e chiamò l’utenza privilegiata, la superuser con il nome “root”, probabilmente ispirato dal sistema operativo Multics, con il quale aveva lavorato in precedenza.
Secondo LinuxInfo, l’uso del termine root, per l’onnipotente utente amministrativo, potrebbe essere derivato dal fatto che root è l’unico account con permessi di scrittura (cioè, il permesso di modificare i file) di tutta l’alberatura del file system.
La directory root, a sua volta, prende il nome dal fatto che i filesystem (cioè l’intera gerarchia di directory usata per organizzare i file) nei sistemi operativi Unix-like sono stati progettati con una struttura ad albero in cui tutte le directory si diramano da una singola directory che è analoga alla radice di un albero.
Multics è stato rilasciato nel 1969, proprio nel periodo dell’avvio della scrittura di UNIX da parte di Ken Thompson.
Non ci sono fonti affidabili sulla storia dell’utenza root, ma presumibilmente Ken Thompson, ispirandosi a Multics, diede il nome “root” al superutente, in quanto padrone assoluto dell’alberatura delle directory e dei file presenti in un sistema operativo.
Fonti
https://en.m.wikipedia.org/wiki/Superuser
https://multicians.org/myths.html
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…