
This is a continuation of the Conti story. You can read the previous part, which covered the group’s origins, in the previous article. We will now explore the internal components of the group and how their own ecosystem began to collapse. Wizard Spider is still full of surprises and in this episode we will unravel the most proibhited ones

Mid-2021, Conti is dominating the headlines with consistent attacks and gaining ransoms from victims. The RaaS operation has been a big deal in the ecosystem, attracting the attention of everyone involved, including victims, affiliates, and law enforcement corps. But that’s just a piece of the whole puzzle.
Trickbot operations never stopped and actually continue to evolve. As written in the previous article, Trickbot became a popular tool even outside Conti operations thanks to the transition to a Malware-as-a-Service (MaaS) model. With a monthly fee, anyone could use the infamous modular Trojan, which received constant development (in this CyberInt article you can find some of the modules and deliver methods).
The US federal government needed to contrast ransomware and digital attacks, which received a huge boost thanks to this new underground environment that exploded after Ransom Cartel. A small step back to 2020, US elections are planned to take place on November 20th. When we described Wizard Spider/Conti Toolset in the previous article, we also covered the capabilities of Ryuk Stealer. Some of the features included the automatic exfiltration of files that contained specific keywords (names and contents) highly related to Western government assets.
All of this highlighted how the group behind Ryuk, TrickBot, and Conti RaaS had particular political interests beyond mere business or economic purposes. Obviously the origin of attacks has been described as Russian nature. The United States was concerned about potential influence or sabotage regarding the upcoming elections, which motivated law enforcement to launch offensive operations against the TrickBot botnet.
The US Cyber Command (never confirmed by the agency itself), headed by NSA director Paul M. Nakasone, made a disruption operation on the whole TrickBot botnet infrastructure in 2020. On September the botnet was flooded by intentional bogus configuration files which setted the communication with the C2 server to the localhost IP address.
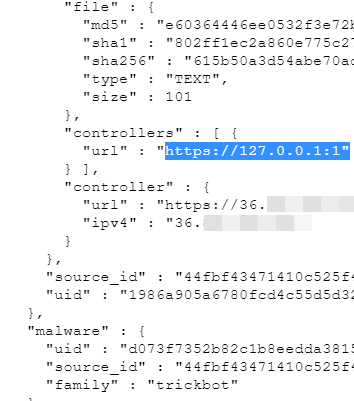
The new configuration broke Trojan’s communications effectively stopping part of their operation especially Ransomware attacks. Moreover, Microsoft took the turn with a huge series of legal action in order to shutdown TrickBot machines completely. In less than 2 weeks the company was able to shutdown 120 out of 128 servers (source Microsoft).
A big hit on TrickBot but not for long…actually shorter than expected. Somehow the “evil” developers embedded a fallback mechanism with the objective to recover broken communication channels with TrickBot agents in case the infrastructure was modified. Resilience sounded like the biggest priority for the TrickBot group. The operation is not a simple hole in the water just because the quick redemption and adaptability of the threat on the technical side, it has been a message to everyone showing the position of US government against digital attacks and criminal environments with a proactive approach.
The directive of Paul M. Nakasone under the Trump administration was clear: “persistent engagement”,“defending forward” and “hunting forward” rather than passive prevention and mitigation. There is no proof of TrickBot used specifically on targets with election sabotage purpose but Ransomware attacks using the Trojan continued even after Biden election with the same pace.

The warrant arrest for TrickBot developers and maintainers was issued in August 2020. We had to wait until the start of 2021 before having some of those individuals handcuffed, in Febbruary “Max” is the first member of TrickBot that had to face the blinded goddess.
Ladies and gentelmen, Alla Witte, 55 years old, in art “Max”.


Before covering the charges she had to faces let’s make a small note on how Alla Witte has been (presumably) discovered. First of all take a look at the URL haus page about “Max” personal website. Note the “RED” keyword.
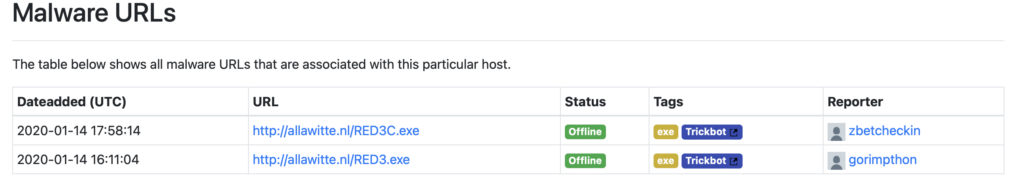
This is not the first time Witte mixed personal life with her underground activities, in December 2019, she infected on of her own devices with TrickBot stealing the data and store everything inside on the C2 server (source Hold Security). In addition, on social media profiles, Witte cite “Max” as someone really close to her. In short, Operational Security (OPSEC) was not the sharpest skill of Alla Witte creating gaps usefull to law enforcement that were trying to de-anonimize “Max”.
She was living in Suriname working as web developer freelancer, the arrest took place in Miami Febbruary 6 2021. The count on her included :
You can find the whole Arrest Warrant on the official USA Justice department website, interesting enough is the reputation within the group. Most of members knew her gender and real name reffering to her like a son would do with his mother. She had prestige for her technical skills, TrickBot members were really happy to know Witte was in charge of the development process.

The investigations uncovered the origin of TrickBot reside in Dyre bank trojan, in 2023 Alla Witte was senteced to 2 years and 8 months of prison time.
The list was still long and Witte was just the tip of the iceberg. The next individual was Vladimir Dunaev a.k.a “FFX” (38 years old). Vladimir was resident in Russia (Yakutsk region), in mid-October 2021 he was arrested in South Korea (no details on why he moved have been released) and extradited to US. He will face a process with a maximum of 60 years in prison.

BleepingComputer, at the time, released a table from the indictment paper showing the activities of Dunaev within the TrickBot group
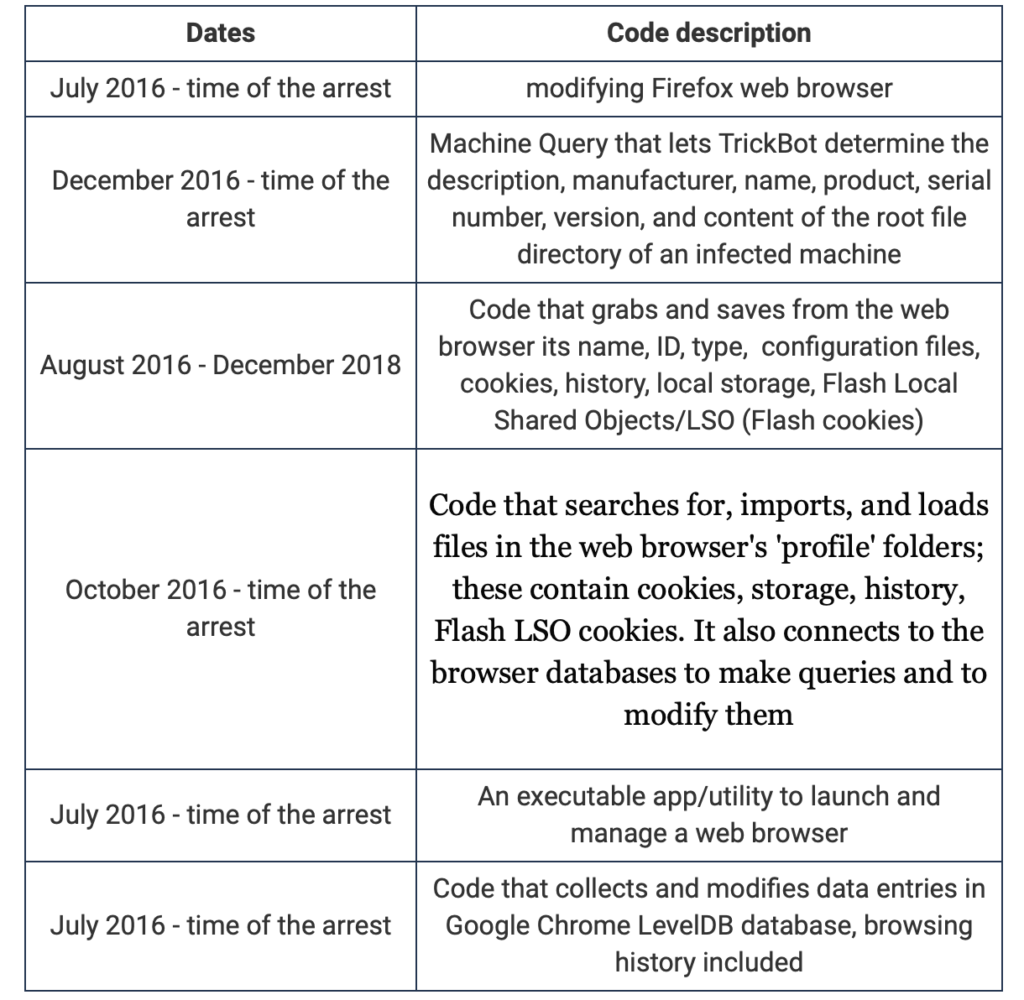
FFX pleaded guilty in 2023 and in March 20th 2024 was sentenced to 5 years and 3 months in prison. TrickBot developers have been under high pressure with this 2 arrests. US government officials stated to have identified other individuals responsible for deployment, development or money laundering activities related to the modular Trojan group.
TrickBot operations didn’t stop but is clear the battleground has changed, Conti and major western countries governments would prove themselves fighting head to head!

In August 2021 the ransomware scene transformed from stray cat to urban panther : LockBit 2.0 was out, money flow was bigger than ever, Colonial Pipeline attack and Initial Access Brokers market became more popular. The ecosystem is now mature with a spice of ”professionalism” but what happen when “dark-companies” lack of transparency and honesty?
Well we should analyzed what happened with XSS user m1Geelka
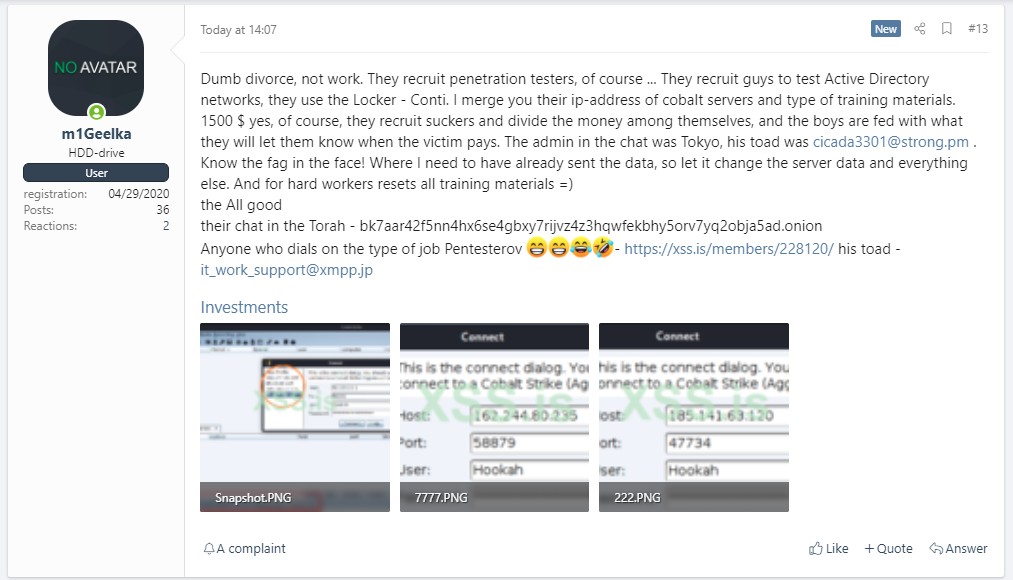
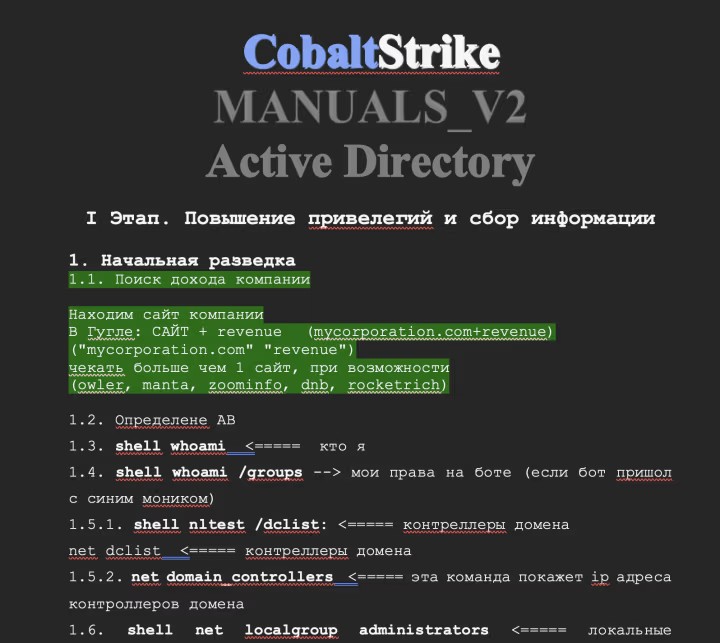
This (really upset) ex-Conti affiliate leaked the manuals provided to attackers in order to exfiltrate data and deploy their ransomware. The guides were about Active Directory environment, enumeration and common attacks abusing missconfiguration or knwon vulnerabilities (PrintNightmare, EternalBlue and ZeroLogon).
But let’s go with a bit of order, why this person was angry? His blogpost is pretty clear the motivation was minor payments based solely on “what they [Conti] will let them know the victim pays”. The affiliate program was 70/30, 70% to the attackers and 30% to the RaaS, the point is the difference on Conti claim and the real ransom amounts. Unluckly nothing critical has been leaked, no source code, no secrete chat and no identities disclosed. Wait a lil’ bit for that )).
Some specific used by affiliates have been uncovered : strong use of Cobalt Strike, powershell scripts and procedure to exfiltrate data (install RDP agents and upload everything on MEGA/FileZilla upload). More technical figures would stand up for moment with surprise expression on their face, the procedure described is simple, really basic.
Somehow the Conti staff wanted to create documentation for novice and non-expert attackers, probably for 2 reasons : easy to fool and “quantity over quality” with standardise attacks. If the words of the affiliate were true it means the total payment for an attack was $2100, even without knowing the target is pretty unrealistic given the average ransom were +$100K. We can believe the affiliate words with wide range of confidence.
Like legal companies out there do, Conti was taking advantage of some employees just for profit. The guide contained some IP addresses and some minor IOCs that some major vendor added to their solutions and Conti threat profile.
In case you want to get in touch with the leak contents, ForbiddenProgrammer made a public GitHub with everything you need.

Until now we covered a lot regarding Conti in terms of evolution and timeline, before continuing our journey is necessary we stop and mentions some attacks made by Conti RaaS in 2021. We already talk about the Irish HSE ransomware attack so let’s break down other meaningfull operations.
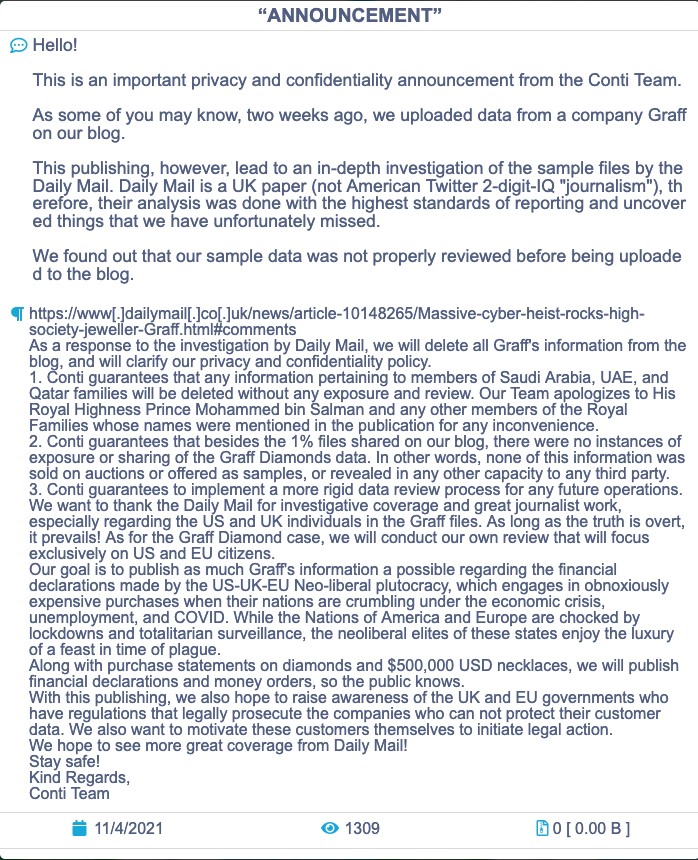
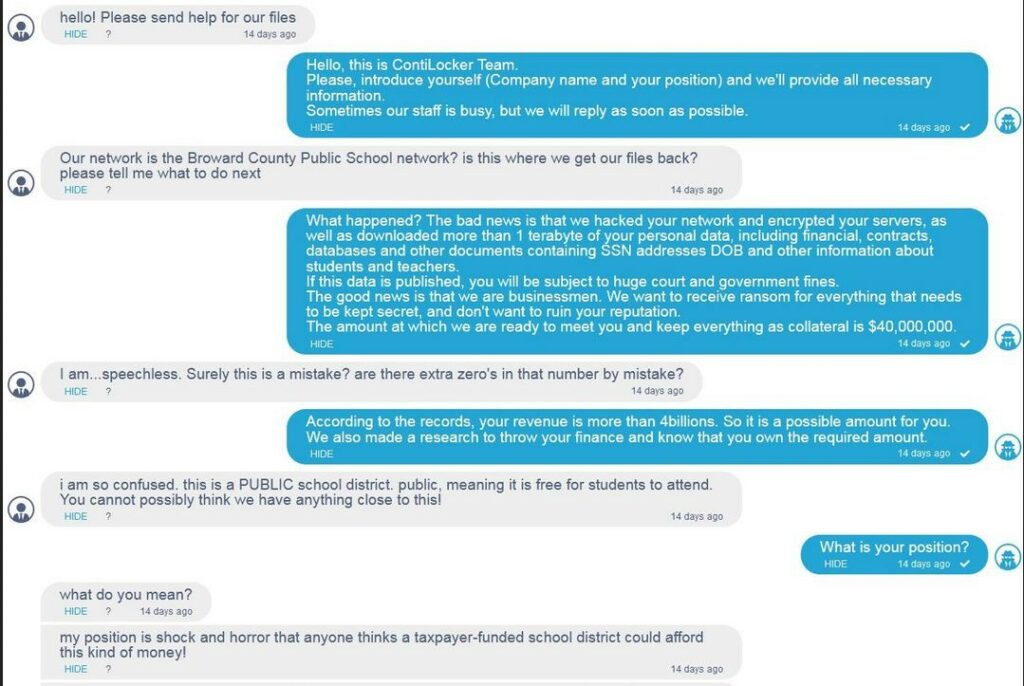
Outside attacks Conti in 2021 decided to sell victim access to others with a new feature to their business model. The RaaS extended the features of the malware and a tools to blow up victims’ backup. Conti grew up in terms of money, affiliate and capabilities. They don’t lose any chance to twink-twink or shame western countries (US,UK and EU) meanwhile making as much money as possible.

The 2022 started and Conti continued to populate the DLS. Everything was returning to the normal well-being after 2 years of COVID-19 and economic losses, slowly the globe was recovering and ready to stabilize. On Febbruary 24st, president Putin announced the deployment of Russian troops in Donbass in order to support separatist corps in Donetsk and Luhansk regions protecting them from the “genocide” caused by Ukraine, minutes later his words tranlsated into reality. The rest is history ready to be written once the war reaches its conclusion.
On that period ransomware groups were not too explicit on their politic positions pubblicly, is not a good idea to mix politics with businesses. Febbruary 25 Conti pubblished a new post on the DLS, no new victim this time. Just a message to the world.
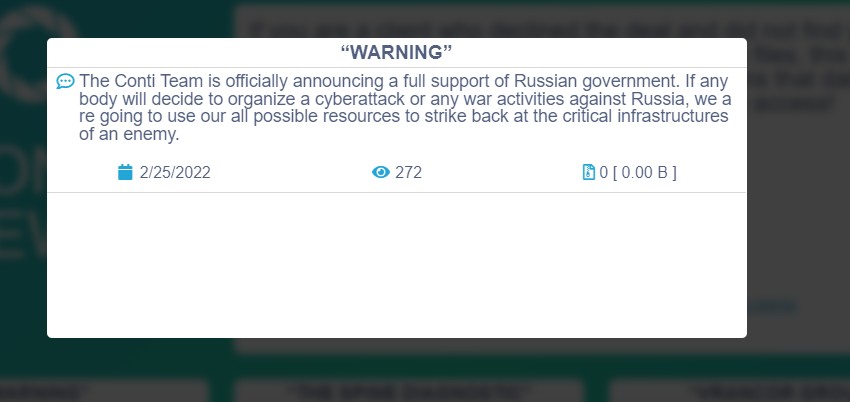
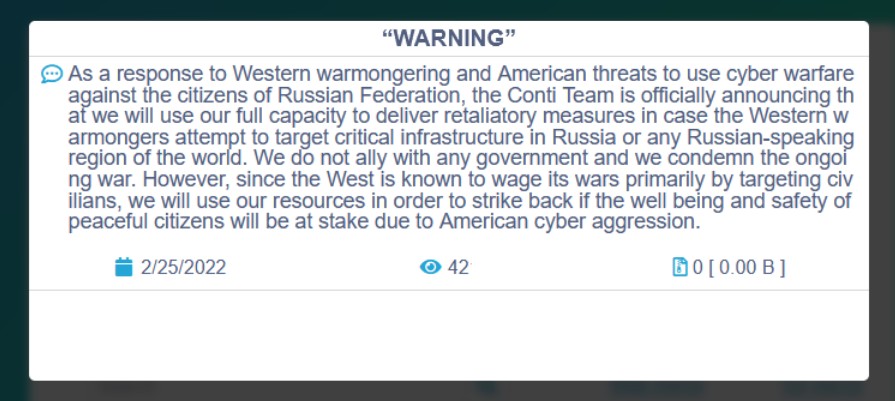
This was something new in the ransomware landscape. Conti is not just picking stating his position but also threatening other countries to not attack with “any war activities” against Russia, otherwise digital retaliation would occur.
The headlines flooded with their statements while non-technical people were confused, skeptic or scared. Hard to digest when the same group which blocked good part of Irish healthcare system is ready to pull the trigger on your critical infrastructures.
For a while silence and tension were the only things dominating the room. In less than a week something new was shaking, again, the infosec environment but this time not from Conti.
Febbruary 27th Conti understood their position and threats came with a price and an Ukrainian security researcher was there to make them pay once for all. The account ContiLeaks on Twitter/X announced with a link that 13 months of Conti chat logs have been leaked
conti jabber leaks https://t.co/0FzXiXhI2d
— conti leaks (@ContiLeaks) February 27, 2022
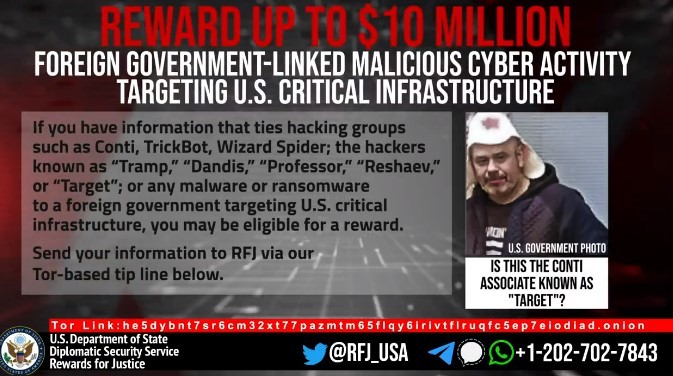
Every messages from January 29 (2021) to February 27 (2022) is now out for everyone. The messages comes from a Jabber server and Rocket Chat logs. Some usernames are recurrent : Defender, Stern, Mango and Target (keep in mind this last one) just to name a few. “Max” (Alla Witte) is also present into the chat logs.
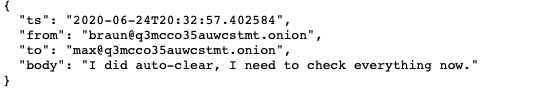

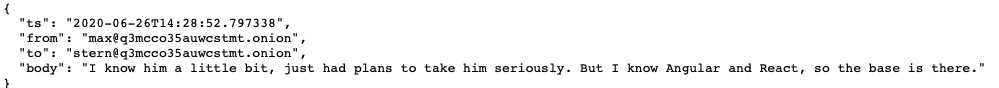
Check Point Research made an amazing job with an in-depth analysis of the chat logs, something special is their graph rappresenting the organigram of the group.
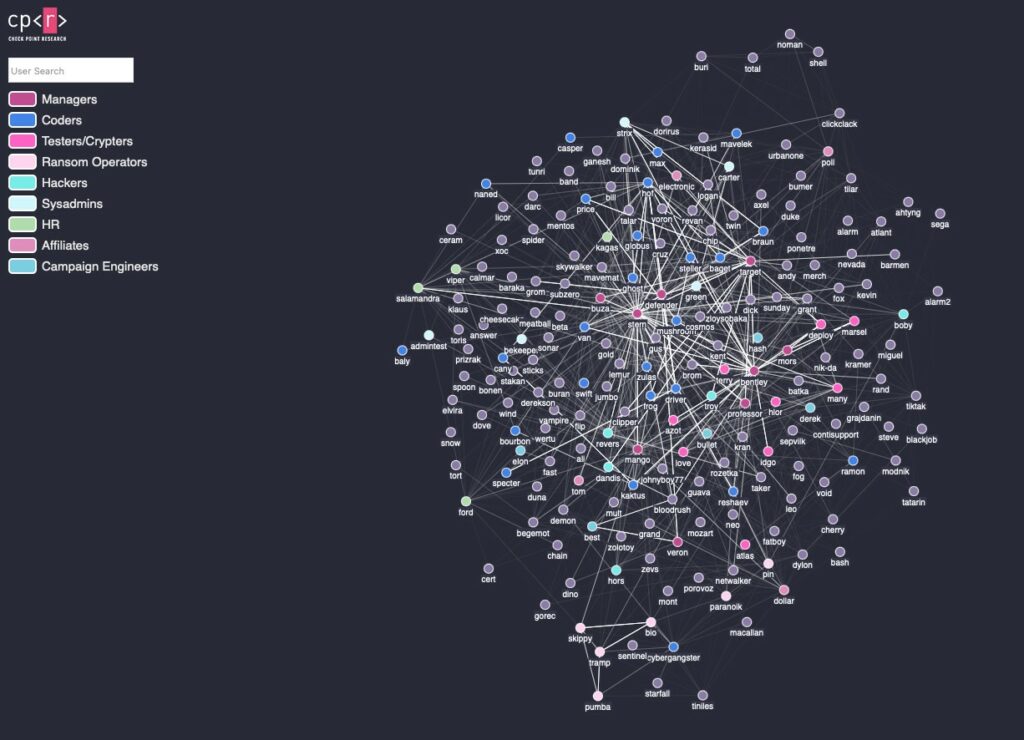
Even if was just a little scratch, what came out with analysis was between brilliant and surprising. The structure of the group is really far from a simple group of computer specialists. Human Resources, sysadmins, affiliates, negotiator, operators and developers are well distincted from each others, with timetables and day-off like a regular company. They have also project outside malware like the creation of a social media for blackhats. An “employee of the month” program was also part of the Conti company structure, individuals with outperforming results would be rewarded with an extra payroll.
To understand how much professionals those people are take into account that when Windows 11 was out Conti had a team responsible just of reverse engineering the software seeking for new exploit and abuses.
Chats include recruitment, updates, executable/DLL requests for crypto and relations with other ransomware families like Ryuk, Maze and LockBit (apparently, LockBitSupp in persons have joined the chat with pseudonym “Brom”). A good part of development process was about AV evasion where “employees” asked to their “supervisor” to buy CarbonBlack AV and other major AV/EDR product. Same thing on Reverse Engineering and testing, a refurbished SonicWall (SMA 410, the new model at the time) have been bought for that.
ContiLeaks was not satisfied enough so March 1st and 2nd released new fresh logs from the jabbers
trick conti forum https://t.co/BrVRM457If
— conti leaks (@ContiLeaks) March 1, 2022
rocketchat leak https://t.co/9K1kwtDas5
— conti leaks (@ContiLeaks) March 1, 2022
Ukraine will Rise! fresh jabber logs https://t.co/9JiywCEpT6
— conti leaks (@ContiLeaks) March 2, 2022
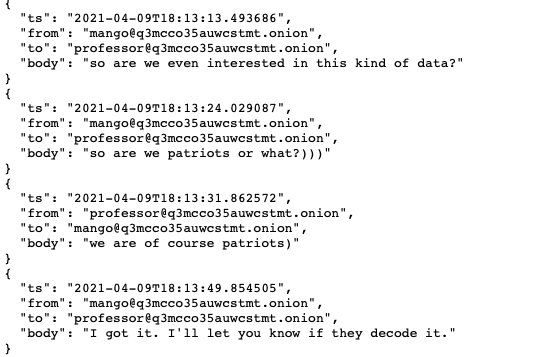
On those new chats we have a conversation between Mango and JhonyBoy77 where they discuss about Alexei Navalny


Moreover the chats included members’ opinion about Ukraine, Russia and the war in Donbass
Patrick: War was inevitable, ukraine made an application for nuclear weapons in their possession
Weldon: monkeys don’t explain things, they climb trees
Elijah: @patrick well done and done. Still, no one will ever use it. Yes, just to scare
Elijah: Look, missiles from North Korea periodically arrive in the territorial waters of the Russian Federation. But no one cares. And they have nuclear weapons, by the way. But somehow no one was alarmed
Patrick: old man, you’re wrong, there is no doubt about north korea now. No one is happy about the war, brothers, but it is high time to put this neo-Nazi gang of Canaris’s foster kids on trial
Their idea on Zelensky is obviously not soft and they took opportunity to underscore his Jewish origins
Weldon: Zelensky is a jew. Oh fuck
Kermit: Jews. Oh great. My favourites
Weldon: that’s right, not Jewish, but a Jew
Kermit: fuck, I wish I was a jew. just be born Jewish and you’re considered a member of a secret society and you mess up the Russians’ life
Weldon: A tartar was born – a Jew cried
Gelmut: black Crimean Tatar born in Odessa, who received Russian citizenship 😀
Weldon: Obama?
Gelmut: A Jewish boy approaches his parents and says – I want to be Russian. To which the parents reply: – If you want to be Russian, you go to the corner and stand there all day without food. Half a day later, his parents ask: “How do you live as a Russian? And the boy answers: – I’ve only been Russian for two hours, but I already hate you Jews.
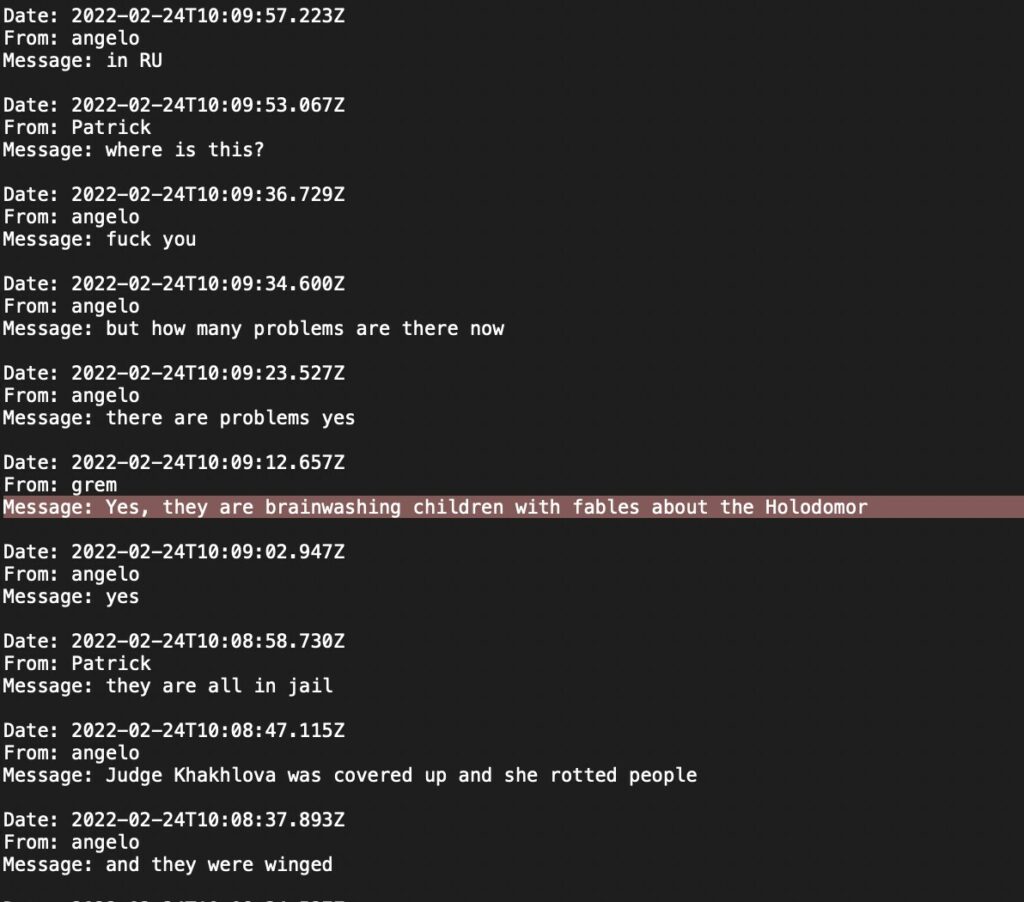
Sticking again with the Ukraine, they defined Holomodor as a sort of “fable”
A lot of sexist and homofobic messages have been sent into rocket chat without no problem with other members to follow up.
What is most disturbing is the black humor about children abuse
Angelo: is it possible to fuck the girls while they are sleeping?
Elroy: No, get enough sleep, then, in the evening ..
Angelo: ok, I’ll put the tape back
Benny: iconic movie..
They also share what they are watching with others
Kermit: although after my link everyone went to try for sure
Angelo: cp what is it?
Kermit: Child Pornography
Angelo: No, even under 17 is no way
Kermit: Come on
Angelo: well, 16
Kermit: There are such lyali at 16
Regarding this problematic and disturbing discussion topics most of the messages show that Conti guys are just normal people with their daily lives, vices and families. Their thesis about Ukraine and other anti-Russian individual stick with the Russian narrative, the decision to explicitly support Russia is no surprise.
Chats was not the only thing that came from the underground, the source code of Conti ransomware and TrickBot backend have been leaked as well. The latter have been extremely useful to collect all the IoC and prevent some of the attacks using that infrastructure, good hit since the tool have been heavily used in ransomware operations.
The Conti source code have a total different story, the real backfire is yet to come. A group of hackers named NB65 broke the non-written rules of Ransomware : Never. Attack. CIS. Countries. They took the leaked source code, changed some parts and removed the language safeguards to avoid encryption within CIS countries machine. When everything was ready they started attack on Russian companies and instead of the typical ransom notes requesting a ransom payment they wrote a textual note warning that the attacks are due to Russia’s invasion of Ukraine.
The well-known companies affected are Tensor (document management operator), Roscosmos (space industry) and VGTKR (radio and television company owned by Russia). VGTKR was affected with a huge exfiltration of data, 786.2 GB, most of them are emails and files. No DLS this time, everything can be found on Distributed Denial of Secret webpage. The leaked sensitive documents includes proof of Kremlin influence on the direction of the contents broadcasted and some “tips” on how to cover specific events directly from the FSB.
Here's a massive list of contacts affiliated with the Russian propaganda branch over at VGTRK.
— NB65 (@xxNB65) March 26, 2022
Maybe we should start some cold calls and emails to properly inform them about what their President and military are up to in #Ukraine? Have fun #Anonymous #FckPutin pic.twitter.com/rLma6ia4Fy
Good morning, Russia. What's with you guys and storing surveillance footage all in one place?
— NB65 (@xxNB65) June 9, 2022
Fuck Valdimir Putin#SlavaUkraini pic.twitter.com/th8jSvZuhv
Conti learned that taunts are not always the best choice, their position about Ukraine probably made angry a lot of persons even within their own group. ContiLeaks made an interview with the CNN giving some insight about is own mission.
He confirmed to be Ukrainan and motivate the leaks with “I cannot shoot anything, but I can fight with a keyboard and mouse”. According to the interview, he was passing the days inside a bunker with his laptop exfiltrating every possible message as possible. He added the FBI contacted him directly asking him to stop so as not to be in the way of their investigation, he stopped for a while but completed the leak regardless the FBI recommendation.
The FBI suggested to remain with a covert access and contribute directly with law enforcement, the reason behind this is (probably) for the tension that was already in play with the war. Biden and Putin had a call in 2021, after that some major REvil members have been arrested in Russia, this was the first sort of collaboration between the two states in terms of digital crime arrests. Probably the actions of ContiLeaks have contributed to broke the thin collaboration between the eagle and the bear.

The Conti leak can be described as the Panama Papers of the Ransomware-as-a-Service, they defined themselves and acting as patriots. Showing what’s behind the curtains have been sensational, the substance behind the form was highly organized with dense workflow and deadlines. The “company” also helped Alla Witte with processural expenses donating $10.000 to her.
They had Human Resource, recruitmnet campaigns and everything analogue of a real company. Simply amazing. From now on the CTI community will be really aware of the scale behind every group, a perfect example is LockBit which made professionalism the main attribute of the first and only ransomware “brand” ever existed.
The ties with the Russia government was not a misteery but having the proof in front of you will still give you a chill on your spine. They were not just taking their nationalism deadly seriously, they acted to prove it everytime they had the opportunity to do so.
The first arrests and the friendly fire put Conti, in this part of the story, in a dangerous situation. The use of their own ransomware in the same territory they claimed to protect was a huge hit on the group reputation.
To the readers: Please don’t mislead what you read in this article as the norm about every RaaS or digital threat out there. The stereotype of the “evil Russian hacker” like every stereotype, has a real baseground but is not enough to generalize the whole landscape. Most groups don’t (at least explicitly) speak about politics and nationalism like Conti did. Obviously, they have only benefits until they respect the “No CIS” rule, but this doesn’t automatically mean their actions are state-sponsored or motivated by nationalism. Please take care of non-technical headlines and make a distinction between state-sponsored actors and RaaS groups.
The story of Conti is far from its conclusion, there are a lot of surprises worth to be narrated. In the next episode we will discover what happen when the illest RaaS in the scene gets humiliated. Remember the user named “Target”? Well, he will be one of the new protagonists of the next episode, enjoy the image below as trailer for the next part.
To be CONTInued…
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.