
This is the last episode of “The Story Of Conti Ransomware” series, we would finally reach the decline of the group and what this means for the current ransomware landscape. In the previous article group we have approached operations made by law enforcement (mainly the FBI) and by some vigilantes which didn’t liked Conti’s political positions. Conti is not dead, it’s still living.

The Conti leak showed the world how “normal” a RaaS group of this size could be with the same organization of a “legit” company. But there is a message which we didn’t analyzed in the previous article, the user called “frances” made a statement about the future of the group on Febbruary 22 (2022)
@all
Friends!I sincerely apologize for having to ignore your questions the last few days. About the boss, Silver, salaries, and everything else. I was forced to because I simply had nothing to say to you. I was dragging my feet, screwing around with the salary as best I could, hoping that the boss would show up and give us clarity on our next steps. But there is no boss, and the situation around us is not getting any softer, and pulling the cat by the balls further does not make sense.
We have a difficult situation, too much attention to the company from outside resulted in the fact that the boss has apparently decided to lay low. There have been many leaks, post-New Year’s receptions, and many other circumstances that incline us all to take some time off and wait for the situation to calm down.
The reserve money that was set aside for emergencies and urgent team needs was not even enough to cover the last paycheck. There is no boss, no clarity or certainty about what we will do in the future, no money either. We hope that the boss will appear and the company will continue to work, but in the meantime, on behalf of the company I apologize to all of you and ask for patience. All balances on wages will be paid, the only question is when.
Now I will ask all of you to write to me in person: (ideally on Jabber:))
* Up-to-date backup contact for communication (preferably register a fresh, uncontaminated public Jabber account
* Briefly your job responsibilities, projects, PL [programming language] (for coders). Who did what, literally in a nutshellIn the near future, we, with those team leaders, who stayed in line – will think how to restart all the work processes, where to find money for salary payments and with renewed vigor to run all our working projects. As soon as there is any news about payments, reorganization and getting back to work – I will contact everyone. In the meantime, I have to ask all of you to take 2-3 months off. We will try to get back to work as soon as possible. From you all, please be concerned about your personal safety! Clean up the working systems, change your accounts on the forums, VPNs, if necessary, phones and PCs. Your security is first and foremost your responsibility! To yourself, to your loved ones and to your team too!
Please do not ask about the boss in a private message – I will not say anything new to anyone, because I simply do not know. Once again, I apologize to my friends, I’m not excited about all these events, we will try to fix the situation. Those who do not want to move on with us – we naturally understand. Those who will wait – 2-3 months off, engaged in personal life and enjoy the freedom 🙂
All working rockets and internal Jabbers will soon be off, further communication – only on the private Jabbers. Peace be with you all!
The message was posted 3 days before their pro-Russian statement, the leaks mentioned are all about the Conti playbook made by an ex-affiliate. Is not clear what are the “much attention to the company from outside” but probably the arrests of Conti’s developers raised some anxiety to “the Boss” which decided to stay off the radar completely.
The statement, knowing all the things that happened after it, have some issue. “Frances” admitted there are no money left for the paychecks but the total inside their (known) wallets contained $2 BLN [1], the group had an average of 2 attacks per day and surely they were not lacking of personell for their operations. “In the near future […] we will think how to restart all the work processes” looks as an interesting quote, if the group was in a stall situation why would they claim revenge in case of digital attacks within Russia borders pubblicly? The most realistic answer is that Conti had a subset of members (“ContiLocker Group”) that was the core of everything and “the Boss” was probably part of it.
Unluckly, this statement still remains a mystery but it pointed out how the groups have no intention to leave the scene. The chat leaks occured and Conti actually choosed silence while their own ransomware has been used against Russia.
17th April 2022, more than 20 institutions of Costa Rican government have been impacted by Conti ransomware. The instituions affected included the Ministry of Finance, Teelecommunications, Social Security Found and state internet service provider. The damage was more than a traditional ransomware attack : webpage defacements, email stolen, official Twitter accounts compromised and terabyte of sensitive data leaked.
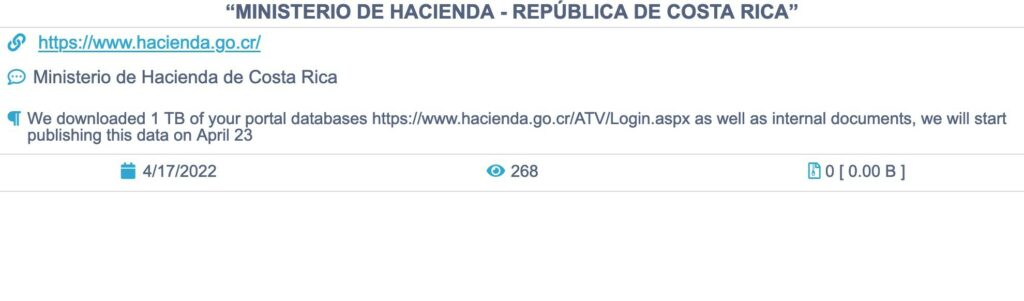
The first institution to be compromised was Ministry of Finance (ransomware deployed in April 17th but investigation uncovered the penetration started in April 11th) through compromised VPN credentials obtained via infostealer, Conti exfiltrated 672GB of data the 15th while it was still moving laterally into the networks.
The bad security posture of Costa Rican goverments permitted a quick and easy access to other sub networks where credentials and data could be stolen to continue the attacks. One of the first consquence was the shutdown of computers responsible of taxes administration.
The 18th Costa Rican goverment announced a shutdown of the taxpayers platform “due to technical problems”, the 19th Conti pubblished a new blog post demanding $10 MLN of ransom.
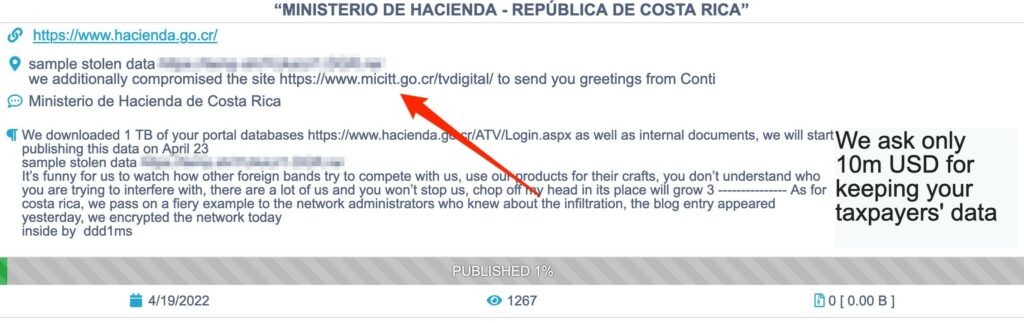
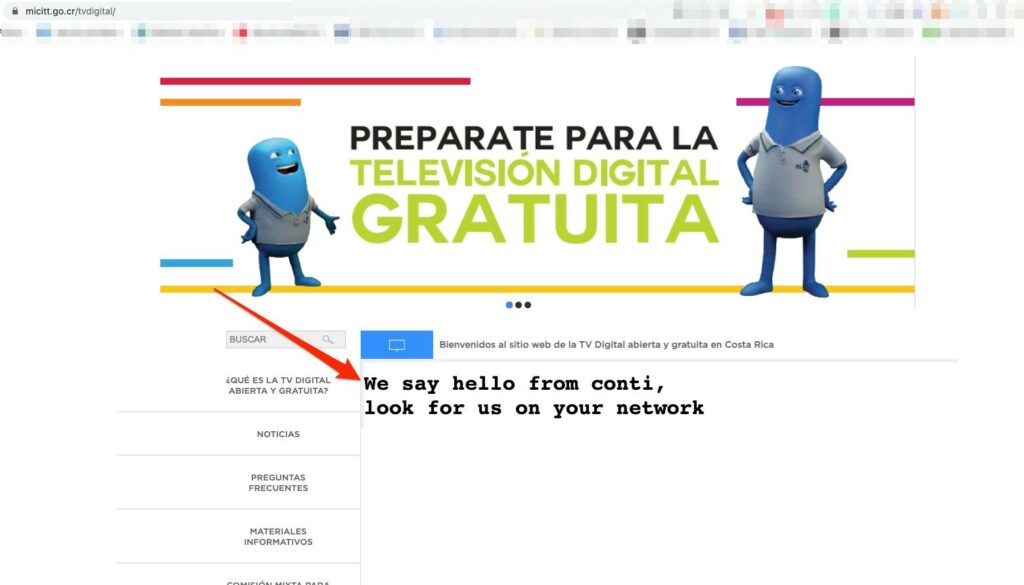
The next turn was on the Ministry of Science, Innovation, Technology and Telecommunications. The attacks will continue until the government of Costa Rica was not ready to pay the group, Conti is now nosier than ever. Another blog post on Conti DLS announced they will start leaking data if the government will not confirm the attack to their taxpayers, the next day the group kept its promise.
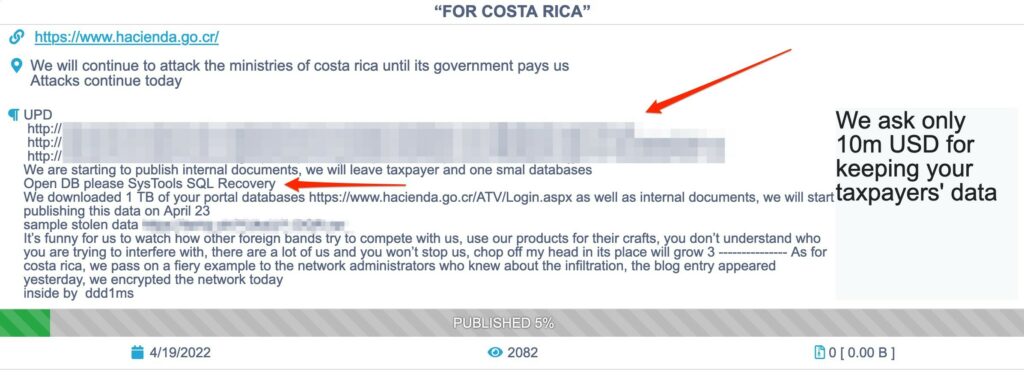
Attacks continued and Costa Rican government required the help from USA, Microsoft and Israel. The damage was wider than expected where good part of the nation was blackmailed by a single RaaS. The 21th Conti updated the audience with more victims.
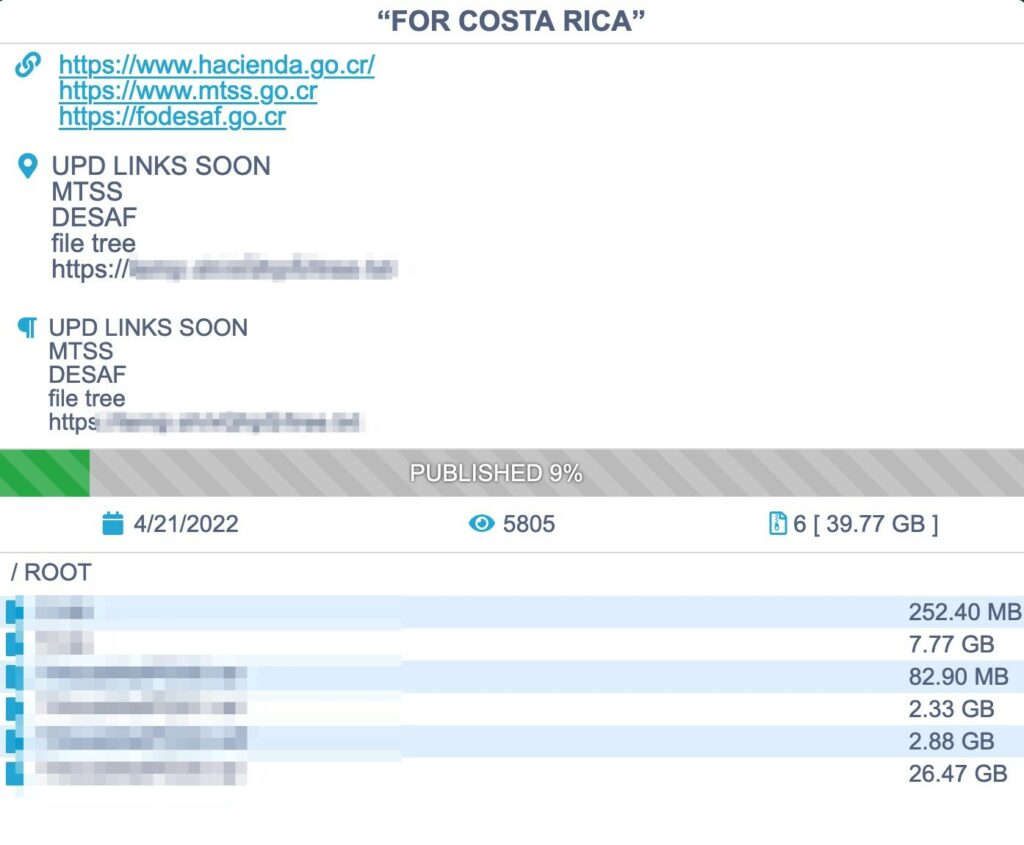
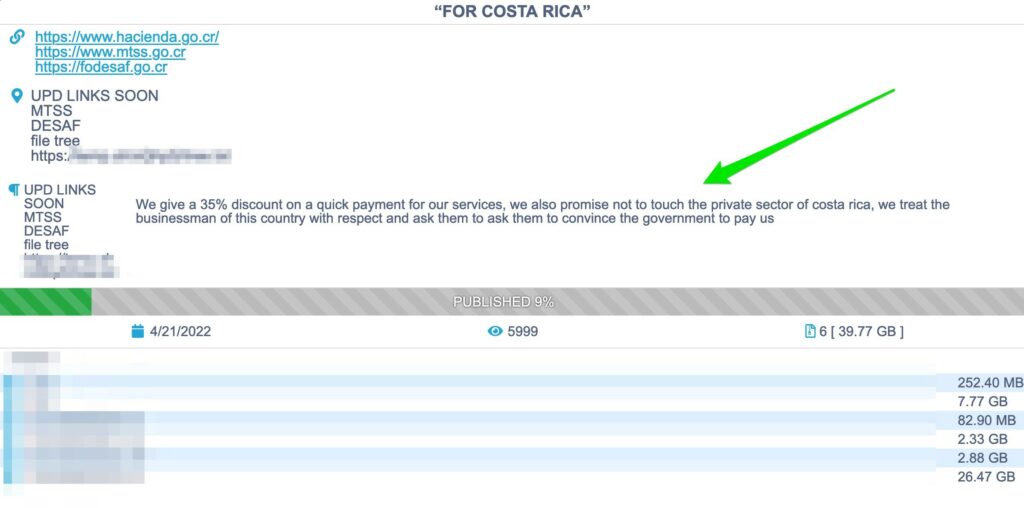
The last message was a 35% discount for the final ransom and requesting Costa Rican’s “businessman” to convince the government to pay.
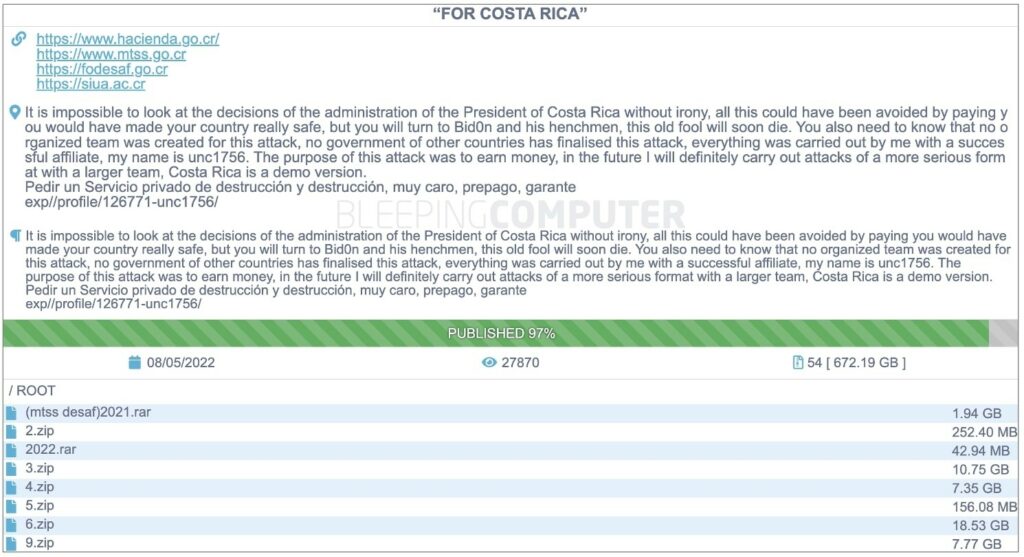
There are some unverified sources that disclosed the real ransom was below $1 MLN but there are no way to confirm this information. No one paid the ransom and data has been finally leaked, in a week a national government was disrupted. Some of the compromised assets required to be offline until June 2022 and on May 8 National Emergency was declared.
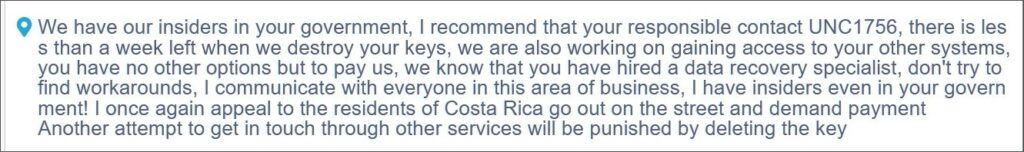
As response Conti declared that Costa Rica was just a “demo version” and they where preparing a larger team for this type of attacks. Other attack attempts have been detected within Costa Rican institutions, Conti also wanted to underline they have insiders and knowledge of every action taken by the blue team in charge of incident response process. All the leaks have been made by an affiliate called “UNC1756″.
During this large scale attack-chain Conti “employees” where moving to new realities as soon as they have received the message posted by “frances”. Conti was changing it’s skin, from centralized brand to distributed semi-autonomous groups.
We can divide the new collectives in 2 subsets : Autonomous and Semi-Autonomous.
Autonomous Groups have been founded from scratch, they didn’t use Conti ransomware and their works was extortion solely via data exfiltration (at the start). Some of those groups developed their own encryptor in the future and are still living now. This subset included :
Semi-Autonomous Groups are made by former Conti members that wanted to continue to encrypt networks, probably good part of developers shifted to this type of collectives. Those groups implemented the RaaS business model at the really start and (the original) Conti was still at the top of management. Here we have notorious groups like:
The objective was to maintain Conti power but acting pubblicly under a different name. While the Costa Rican goverment was suffering from Conti damages those groups started to pop out under the radar thanks the noise made in April 2022. In the background, like deamons, Conti was preparing a new wave of ransomware groups.

On May 6th 2022 the US Department of State announced a reward for everyone who would share information about the people behind Conti Ransomware, up to $5 MLN. The 19th Conti started slowly to close their infrastructure starting from the admin panels, negotiation panels and stopped pubblishing post on their Tor DLS.
Apparently the Costa Rica attacks were a sort of excuse to gain visibility for the last time before leaving the landscape. Conti stopped to attack companies and the last week of June 2022 the DLS has been shutted down completely.
Conti is gone but some people decided to dwelve within the bunny hole trying to disclose the identity behind the RaaS. A major example has been “pancak3” a security researcher that made a whole format called “Who’s Behind The Keyboard” where he dox Ransomware operators. Everything was posted on his Substack (which he have been banned from) and one of this included “van” one of the developers of Conti (the original post can be found through the wayback machine).

We suggest to read the original post since it contains screenshoots of Van’s desktop, obtained through an Agent Tesla implant in 2021. After a month US Reward For Justice (RFJ) showed the face of “Target” another Conti member (which we have already met in the previous episode) and the moniker of other 4 members, RFJ requested informations marked them as responsible of malicious activity against critical infrastructures in USA.
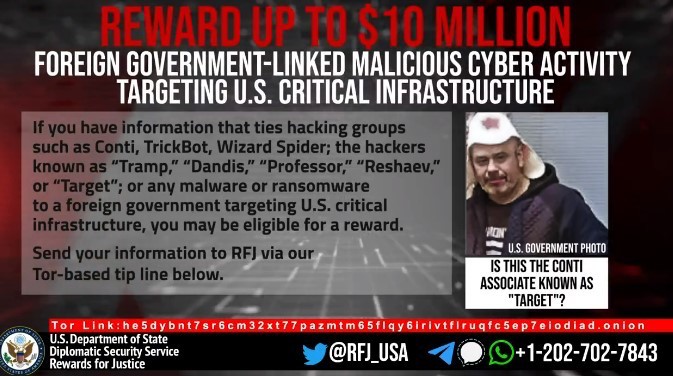
Moreover the FBI added some data about the Conti activity, 1000 victims have been identified which have paid a total of $150 MLN to the RaaS. In conclusion the US government said they were looking for people with “different nationalities and citizenship”. Their investigations highlighted that even if the group was linked to Russia, parts of their members are scattered worldwide.
Dragos (OT Security firm) analyzed the trend of industrial organizations victim of ransomware attacks, when Conti officially closed a decrease of attacks has been detected. Dragos claims that Conti was responsible of 28% attacks within the industrial sector and their retirement is a partial cause of the quick decrease but warning about new groups like BlackBasta which have been highly focused on this type of victimology.
From this point in time, Conti disappeared. Their attack to the Costa Rican goverment was the final ceremony before closing their activities.

As said in the intro of the article, Conti legacy is still living. The RaaS has roots of the origins of the current Ransomware Phenomenology and the capabilities to drive the future as well. Their influence affected victims as well, in 2022 more victims refused to pay the ransom made by those groups. There are a number of reasons behind this but one can be linked directly to Conti, paying this type of group (especially after their political positions) is too risky as the FSB and other Russian entities are under sanctions. After the leaks the link between such entities and Conti was too obvious.
Shifting to new smaller units is also a tattic used by threats to bypass sanctions (like Evil Corp did with LockBit) and dispel all the attentions they have attracted in the 2022. Let’s dwelve the new forms of Conti!
BlackBasta has been the group with the closest victimology to the Conti one : manufacturing, construction and industrial sector. Not just on TTPs and victims but also on profencies in terms of money is pretty similar to the original group, Elliptic made a great analysis of BlackBasta wallets where more than $100 MLN have been received from ransom payments (329 collected for this analysis).
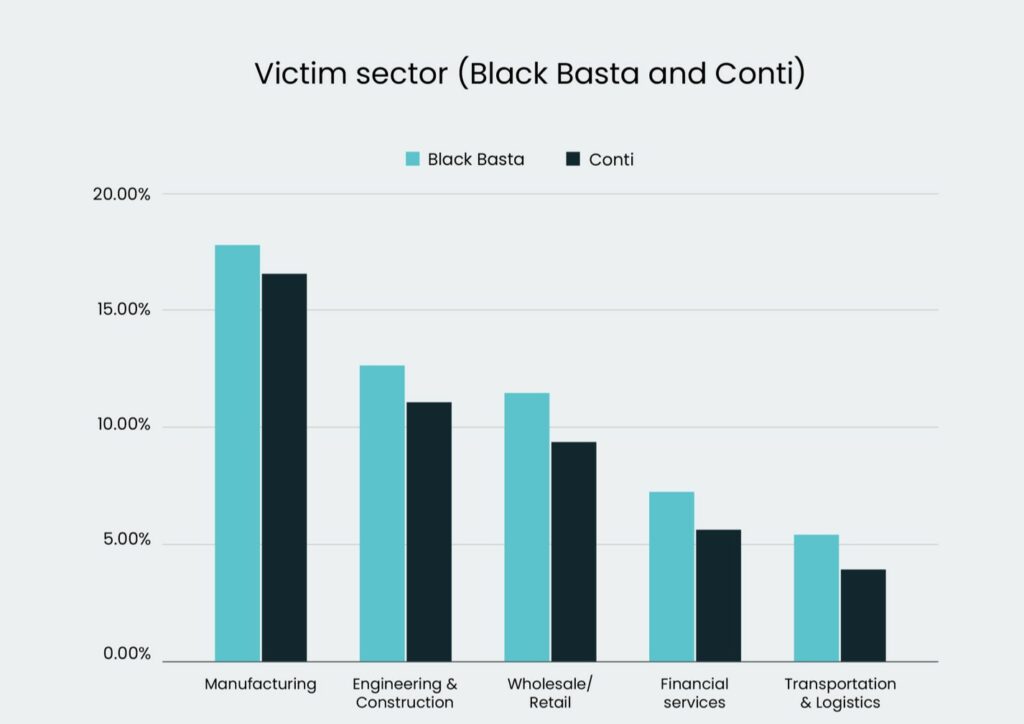
The group is still active with a high grade of adaptability and social engineering skills allowing them to get initial access in combination with vulnerability like CVE-2024-1709 (ConnectWise).
Quantum, Diavol, Karakurt and Royal are some “minor” strains which have been believed to used by same operators, one of the proofs is the money flows from these strains which all of them point to Stern (one of the Conti admins).
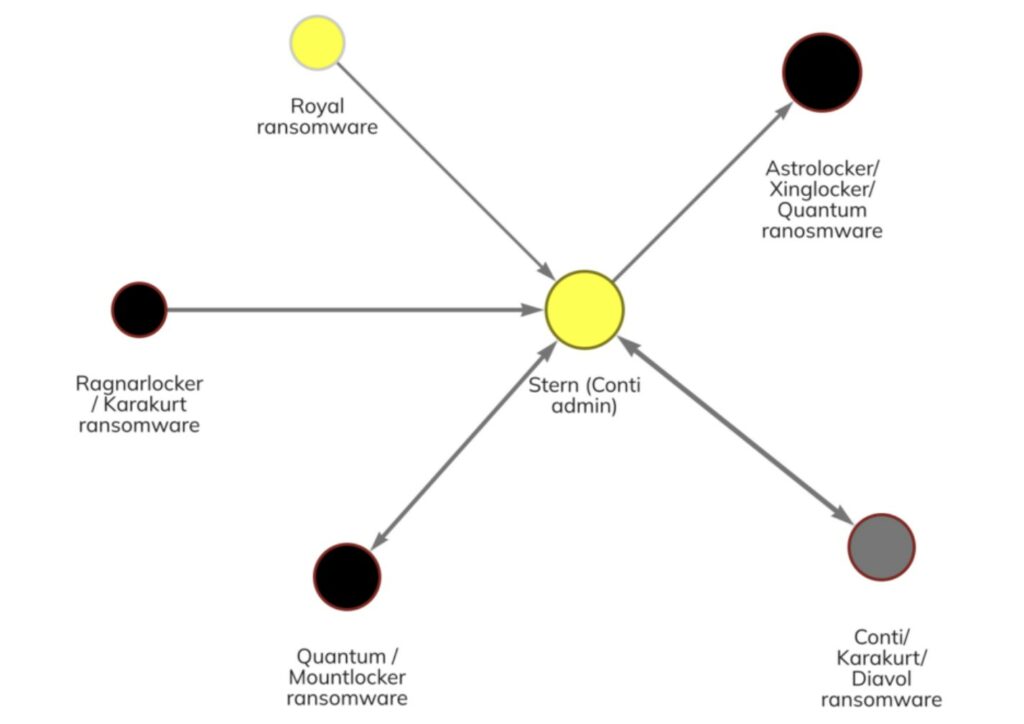
Karakurt was one of the most prolific new Conti extensions, recently (in 2024) one of their negotiator was arrested uncovering payments range from $250,000 to $1.3 MLN received from affected companies. There are no doubt about the connection between Karakurt and Conti, the VPS subscription have been paid by Conti wallets disclosed after the leaks in 2022.
Royal Ransomware is now rebranded as BlackSuit still active posing a huge threat to the healtcare sector and it’s supply chain. In 2022 Royal has been one of the most prolific ransomware strains gaining notoriety within the ecosystem.
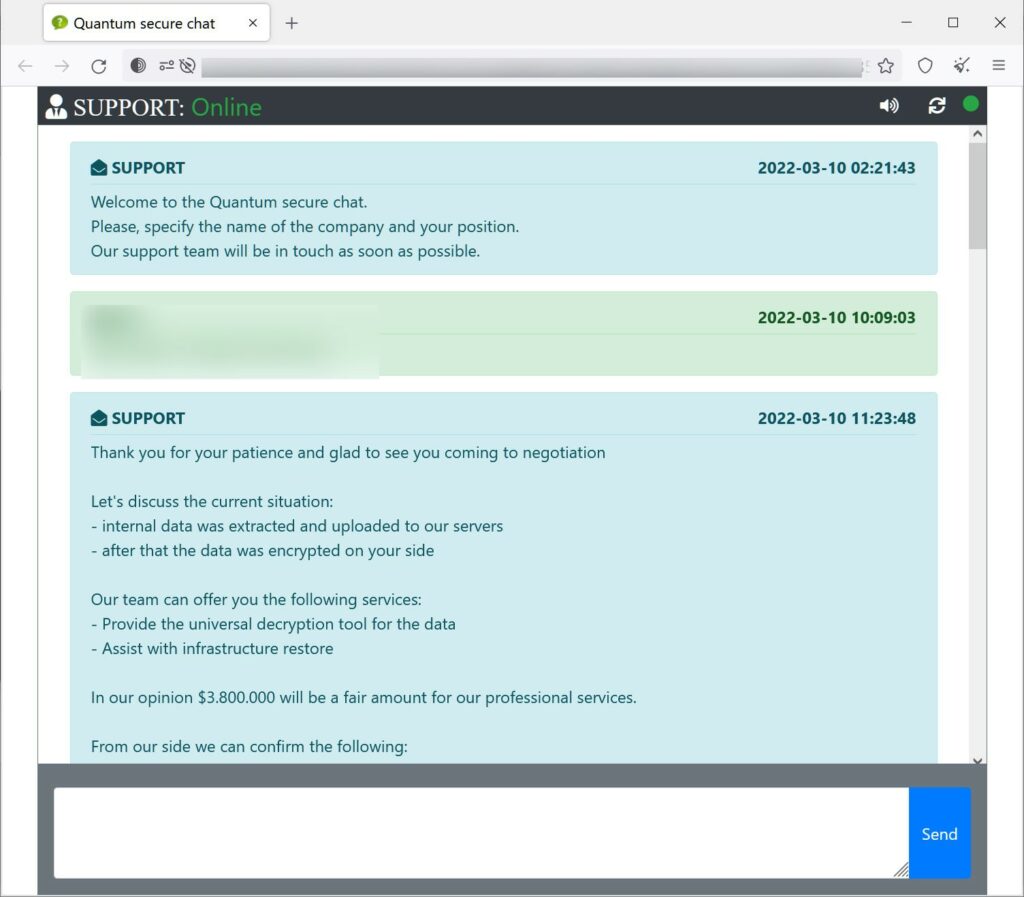
Quantum is one of the most unsual case in ransomware history, according to DFIR Report on of the attack made by this group (from initial access to encryption) lasted less than 4 hours! This strain changed name a lot during it’s exisistence : XingLocker, AstroLocker and QuantumLocker. One of the negotiation chat has been leaked online showing a ransom demand of $3.8 MLN. The group have never been active like other RaaS so is hard to understand if is still active or has been rebranded.
Meow (MeowCorp, MeowLeaks) is a strain that was based entirely on the Conti source code and appeared in the second half of 2022. The real shift of the group occured in 2024 where 80 (approx.) attacks have been attributed to the group, in the timeslot July-September the group was responsible of 68 victims with a huge spike. In 2023 a free decryptor for MeowCorp has been released after the leak of the private keys on a non-specified forum. Right now the group switched to encryption-less operations focusing entirely on data exfiltration with subsequent extortion.
3AM, emerged in 2023 after professionals discovered their ransomware was used as backup option when LockBit encryptor was blocked by AV/EDR, is another group with strong connection with Conti. The tools and TTPs used by 3AM are associated with infrastructure of previous attacks made by Conti (especially during the year 2022).
Akira is one of the RaaS with the best looking DLS in the whole scene, appeared for the first time in March 2023 it was able to grow really fast demanding ransom from $200,000 to $4 MLN.
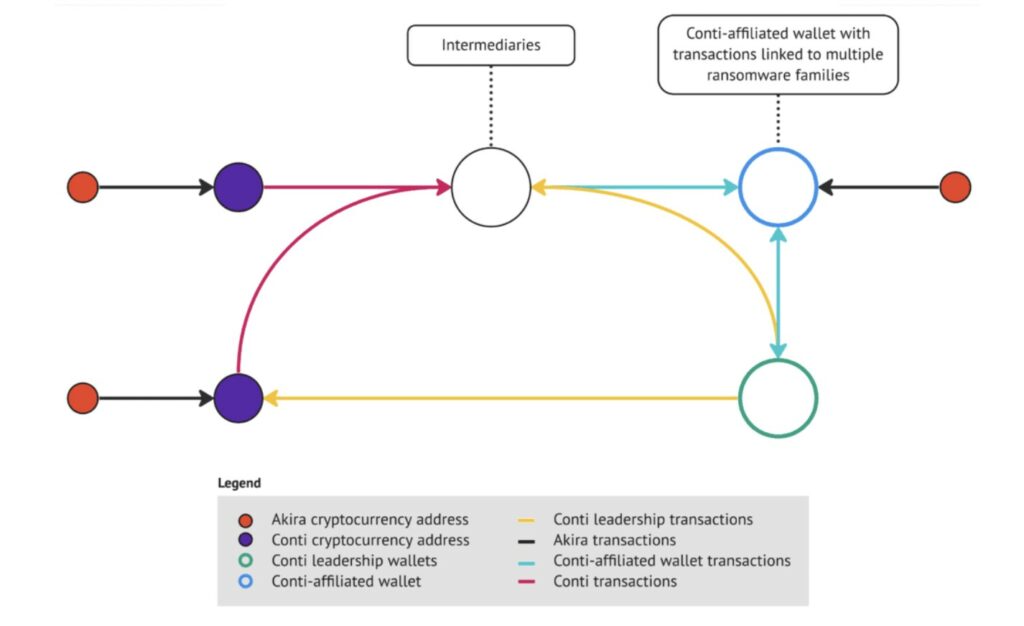
The group share same feature of Conti (eg:/ same extensions ignored, similar ChaCha encryption) and part of their code overlap with the leaked Conti source code. Artic Wolf made a great blockchain analysis on the transaction made by Akira wallet, the whole amount of payments are sent to Conti addresses before they reach the affiliate. This moneyflow is the same used by both Diavol and Karakurt.
The group is still hunting and is currently operating with a new sophisticated ransomware family after a period of data-exfiltration-only campaigns. In 2024 the group reached a market share of 17% on the total ransomware attacks. According to FBI, from their first appearance to the start of 2024, Akira was able to collect $42 MLN from 250 victims.
About the Conti investigation made by the US Federal Government, the 7th September 2023 new charges against Conti and TrickBot campaign have been issued where we can find real names of some nicknames presented into the Chat Leaks made in 2022 like “Mango” and “Defender”. The 9th September 2023 the UK government announced a new set of sanctions (in collaboration with the US) to 7 Russians individual involved in the Conti group.
The story of Conti Ransomware finally reached it’s end but it started a new ones ready to be explored. Right now, as we showed, Conti is more a organisational decentralized structure than a ransomware group. This is why is important understand the background of this huge groups, ransomware history is relatively recent but we proved how quickly can change. Tracking down ransomware groups origins and their present reflection is just another way to understand the threat which need to be mixed with technical aspect of this phenomenology to have an effective preparation to defend against them. Conti taught to good part of current landscape how to perform ransomware and other lateral activities but also showed to the world how this type of enemy can be countered with a combination of law enforcement and indipendent forces…to be CONTInued(?)
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.