
Ransomware, a malware designed to encrypt data making them restorable only with the use of a private key. Relatively simple math is all that threat actors out there needs to disrupt networks around the globe, once lock out you can get your plain data back just in one way : cripto payment.
The real first Ransomware ever discovered was made by Joseph L. Popp Jr. with his malware called AIDS. Isolated in 1989, the program was stored inside a Floppy Disk with the label “AIDS Information Introductory”, sent in the email of 20,000 of WHO conference in Stockholm. Once opened the C: drive of the victim is fully encrypted, game over. To take your data computer back you had to pay a ransom ($200) sent via envelope to receive anoter floppy used to decrypt files.
That was just a sweet start of a real phenomenon and independent ecosystem with it’s own rules and organization. Ransomware-as-a-Service (RaaS) provide an affilation model between ransomware developers and attackers, in this way both party can improve attacks efficency with always increasing payments.
In this series of articles we will unravel the history of one of the most important, aggresive and influent RaaS also known as Conti. This group even if (technically) non active anymore left behind both shadows and lights, it’s history is the perfect example on how RaaS behave, how they are organized and, more importantly, who is behind online monikers.
We will cover from the really start to the present including everything in the middle, knowing Conti group history is valuable (probably even required) to understand the ransomware phenomenology in the past, present and future.
[…] But in case of your refusal to cooperate we will run a great damage to your business, you will lose ten times more in courts due to violation of the laws on the GDPR and yout partner’s data leak. We’ll inform your employes partners and government about this leak, your data will be pubblished on public blogs and salty competitors. We will inform media about cyberattack to your company and backdoor access to your company data will be sold to other hacker groups and it wil be the last day of your business. We don’t want to do that for sure and we will not do that if we negotiate successfully. We are waiting for you in that chat, think about your future and your families. Thank you. Bye
Ransom Cartel (named like this by Jon DiMaggio), a pioneer in the RaaS landscap, emerged in 2020 as breeding ground for several now-prominent and well known RaaS. Its members were affiliated with five different groups : Viking Spider, Suncrypt, Twister Spider, Lockbit Gang and, our primary focus, Wizard Spider.
Prior to delving into Wizard Spider, let’s briefly examine Ransom Cartel and the advantages it offered its member groups. Established in June 2020 by Twister Spider (active since 2018), the collective was predominantly composed of Russian-speaking individuals from Eastern Europe. A notable innovation was the introduction of the “no-CIS” rule explicitly in ransomware codes, preventing encryption of systems located in Commonwealth of Independent States countries.
Analysts discovered that the four groups collaborated to infiltrate networks, culminating in data encryption and exfiltration. These stolen data were then transferred to Twister Spider, who managed the data leak site (DLS) and negotiations. Each DLS post included an attribution to the specific group responsible for the breach.
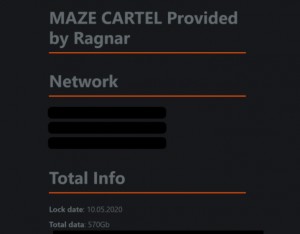
Furthemore the discovery of Command&Control servers belonging to different groups within the same IP range/address revealed strong ties between members. This evidences solidified their shared techniques and information exchange in operational and extorsion processes (eg:/ use of DDoS, VM for evasion, double extorsion). While the specific profit share mechanisms and affiliate programs are still unclear, it was evidnt the exceptional efficency and sophistication
The cartel had undoubtedly dueled the amazing increas in ransomware attack witnessed in 2021 and 2022 as well [1]. The red thread followed by the whole groups was aiming to reputational damage pushing to the limits victims.
Maze explicitly confirmed to BleepingComputer they cooperated with LockBit and “another group will emerge on our website […]” in June 2020. November 2020 Twisted Spider retired Maze trying to masquerade their ties with the other 3 groups, after a year of operations with this specific strain, transition to Egregor (started in September 2020). Togheter these operations allowed the group to extort (at least) $75 MLN from victims.
Suncrypt have been interviewed by BleepingComputer as well saying they have joined the cartel because “They just can’t handle all the available field of operations. Our main specialization is ransomware attacks”. Analysts have speculated that, in the first year of the ransomware era, actors capabilities were highly specialized making collaboration a minimum requirements to monetize their illecit activities. In september 2020 Suncrypt shutdown operations leaving the Cartel after re-emerging with standalone operations.
But who’s behind the original “Ransom Cartel” concept? Apparently REvil! After a series of failures in 2020 the REvil group started to hire new individuals in the underground including operators and negotiators. The two groups have huge similarities in ransom notes, ransomware code/techniques and Big Game Hunting strategy. This subset of threat actors has been called PINCHY SPIDER….but that’s a different story! Is not clear if Twisted Spider is related to REvil directly but the majority of attacks made by the cartel and the post-exploitation activities are close to REvil’s ones.
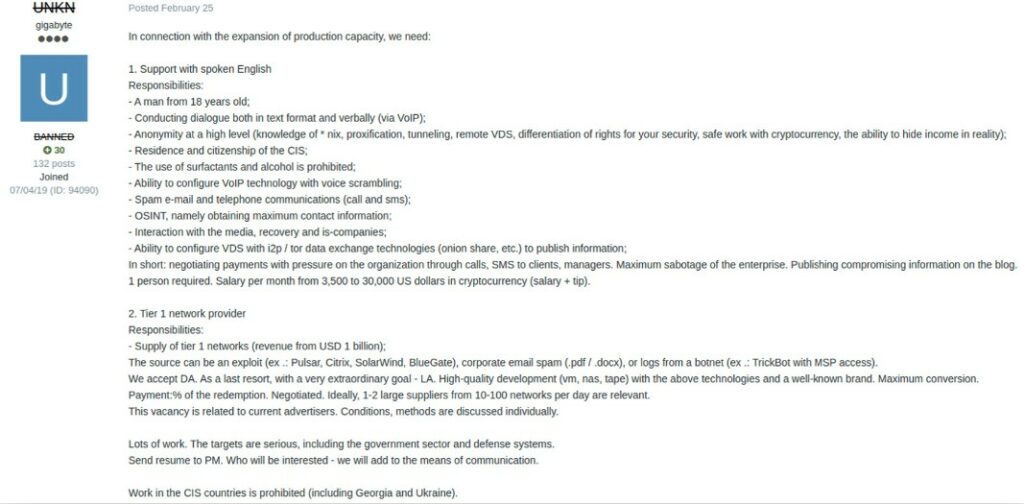
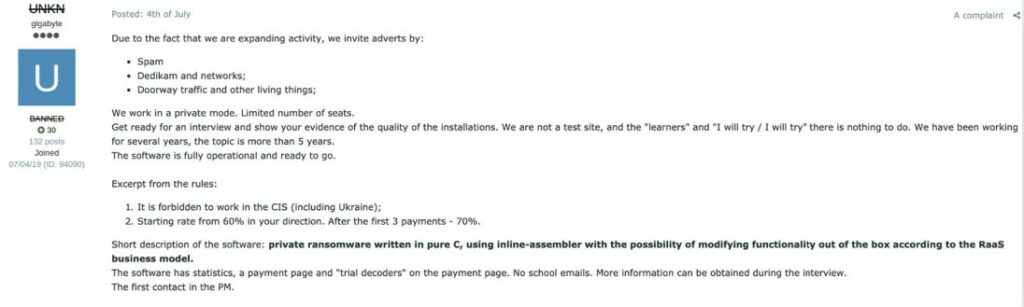
Twisted Spider creation last for approximately a year, after the retirement of Maze operations the group slowly degraded. Pinpointing the exact timeline is challenging, but it’s likely that Ransom Cartel’s shutdown occurred in early 2021.The underlying motivations remain obscure and, understandably, undisclosed to the public. Investigations have yielded partial results, revealing the members’ long-term aspirations for the cartel. While a large-scale operation might initially intimidate victims, it can also simplify law enforcement’s task. Ransom Cartel was not only large but also highly visible, drawing significant attention and some members where skeptical about the future of the collective. Collaboration within Ransom Cartel was often inconsistent and poorly defined, presenting a significant obstacle that ultimately led to the dissolution of the four groups.
Regarding the end of the “Ransom Cartel” the result have been incredibile, amazing and evolution of the RaaS landascape. Every group within the collective had (and some still have!) operated with their own RaaS : Lockbit Gang founded the (still) well known LockBit RaaS, Viking Spider continued with Ragnar Locker but in October 20 2023 have been affected in a chain of arrests, The last tracks of Suncrypt reside in 2022 making them a de-facto veterans in the field and Wizard Spider founded the protagonist of our story: Conti.
The Ransomware 2.0 Era officially started!
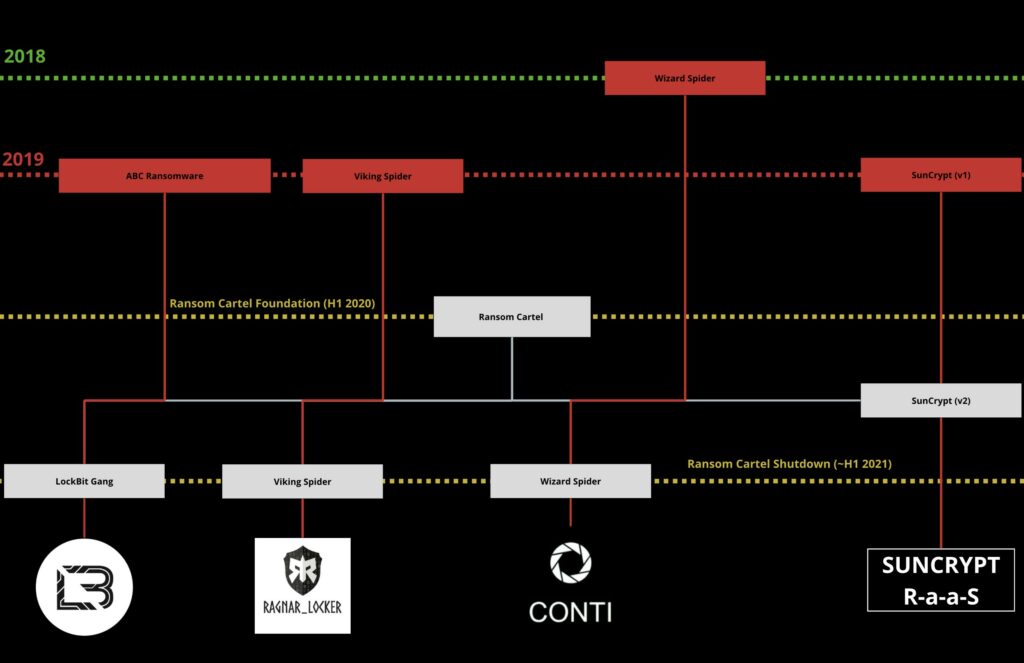
The Ransom Cartel was surely prepared on offensive operation but there was only one group which skills have been far superior by others, Wizard Spider. This threath proved sophisticated TTPs and a vast armory. Identified in 2018 using Ryuk Ransomware in the wild and joined the Cartel collective in August 2020 raising the bar significantly.

The group is interesting, they operated in different teams enabling different operations concurrently developing their own unique tools including:
Should be clear enough the huge flexibility and different operations conducted by this team, they are not just smart attacker but professinal developers as well. Wizard Spider performed multiple operations at once highlighting numerous individuals behind the group and extremelysharp skills.
Conti operations would become a new standalone product after leaving the Ransom Cartel and it would dominate the whole environment expanding the Wizard Spider web.
In August 2020 the official DLS of Conti officialy opens to the public.
The vintage look have been quickly changed with an aestethic and professional version in December 2020 presenting Conti as Ransomware-as-a-service. From the grand opening of their DLS to the end of 2020 Conti pubblished (approx) 175 victims and was just the start.
The year 2021 has been the golden age of this RaaS with consistent operations over west companies and critical infrastructure. On their prime they have been the second highest RaaS in terms of market share with just REvil above them.
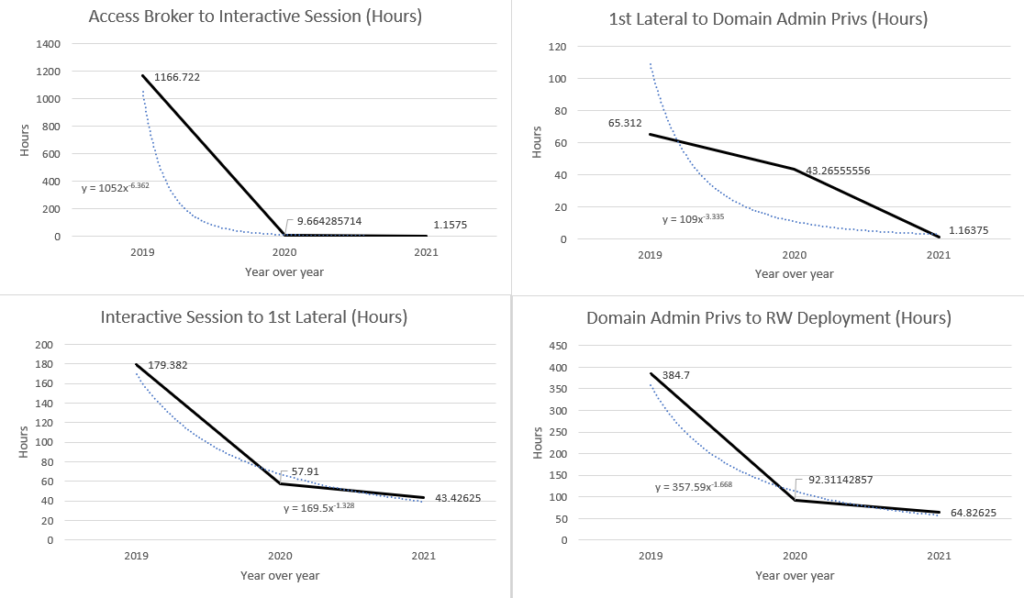
In april 2021 a threat actor was able to encrypt victim network from an inital stage payload in just 2 days and 11 hours. Analysts found wide options of C2, phishing addresses, initial access techniques and malware used in their operations underlying the rang of Conti’s Ransomware Operators TTPs pool which, as result, dropped the average time to damage a victim : from 2 months to 3/4 days.
But Conti isn’t that famous for their skills, instead their reckless victim selection. Since the 26th October 2020, KrebsonSecurity followed a tip from a “reliable resources” that warned the ransomware group behind Ryuk (Wizard Spider) was building a reputation on the Russian underground forums for targetting and damaging healthcare digital assets. The threat became reality shortly after reaching the peak with the Health Service Executive (HSE) attack.
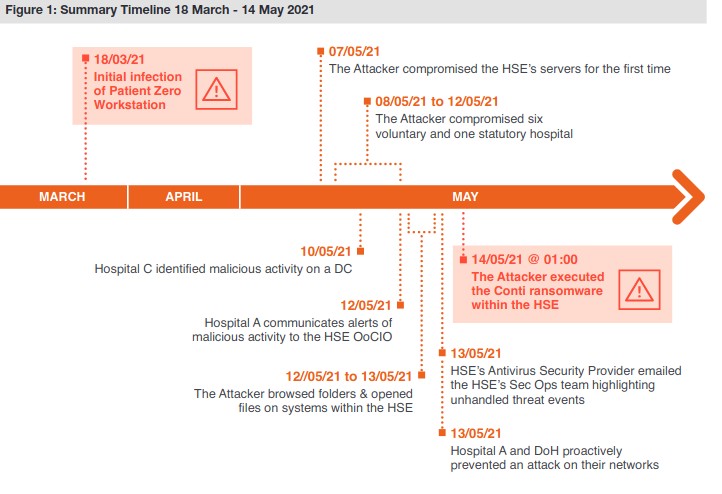
HSE is an healthcare system in Ireland public founded founded at the start of 2005. The 14th May 2021 (in the middle of Covid pandemic) Ireland received the biggest cyberattack in the whole country history impacting hospitals appointment systems, COVID testing referral, vaccine registration portal and shutdown of HSE national and local networks. A full scale disruption made by the Conti ransomware file encryption with several month of recovery as price for the healthcare provider that slowed down the whole country hospitals and medical centers. Encryption was not the only problem Ireland has to face but also stolen data used for double extorsion into the hands of Conti staff.
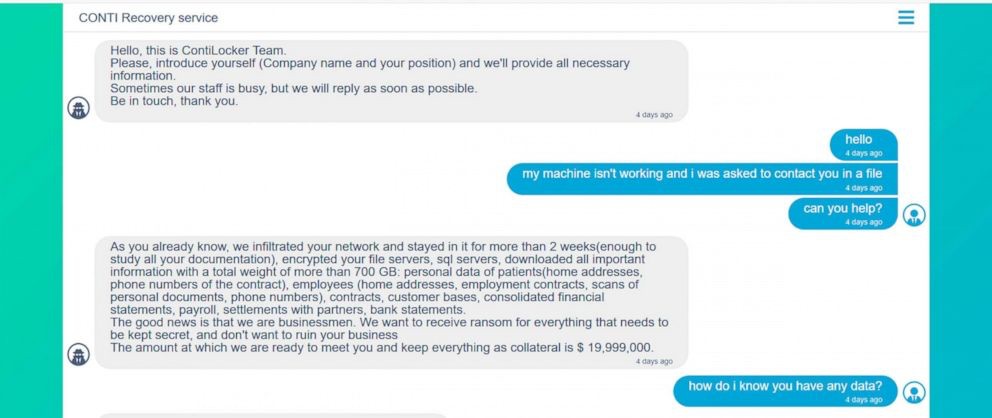
Conti decided the ransom, in the negiation chat, and set it at $20 MLN with additional samples from the 700GB of stolen data : 27 sensitive files belonging to 12 different individuals. The total cost of attack including recovery and legal procedure costed about $100 MLN. HSE made a public statement highlighting the threat used a 0-day vulnerability and “there was no experience in how to respond to the attack” but, during the incident response processes, professionals found tons of outdate workstations (Windows 7 which is not receiving security patches from 2020) around HSE networks that surely helped attackers in the attack procedure.
“The opportunity for error is massive. I mean things like people getting the wrong blood transfusions, samples being sent under the wrong patient’s name […] I reviewed one patient and needed to make a decision about whether to change medication. He didn’t know what he was on, and I couldn’t verify that information”
Medic in Dublin after the HSE shutdown
Conti decided to give the decryptor for free (which was slow and “bad” standing with security professionals words) while still threating to release the data collected, Irish government decided to refuse the payment meaning all health data have been sold for the RaaS profit.
Was this an isolated attack to the healthcare sector? No! The Irish NCSC (National Cyber Security Center) notified attack attempts to the Ireland Department of Health. NCSC forces isolated the systems and found Cobalt Strike (widely used by the group, we would cover this in the next episode) payloads and digital artifacts similar to the ones retrieved in the HSE network but we cannot state at 100% Conti was behind this (attempt of) attack as well.
The core of the Conti attack was not just disruption of a public service but ruining the reputation of HSE, legal actions and dense cost between fines and cybersecurity renovations have been made. We cannot state how much money they have made selling the healthcare data (actually, we are not aware if the data have been sold in first instance) but what we can conclude is that HSE image has been deeply ruined while Conti ones stands strong, an “amateur” offensive group brought Ireland hospitals to their knees with a single malware.
In 2021 Conti outranked the other groups in the scene in terms of money making. Their formula worked, Conti RaaS operation alone is still the best in terms of (documented) profit. In 2021 their extornions worked for $180 MLN since the creation of the RaaS, which was the double of DarkMatter responsible of the Colonial Pipe Ransomware Attack which changed the vision of cybersecurity (at least) in US.
The United State Department of Justice offered help to Ireland during the HSE meltdown, apparently they took the opportunity to get in touch (indirectly) with the threath. USA pubblished 2 documents regarding Conti and their operations the Joint Cybersecurity Advisory : Conti Ransomware (September 2021) and an FBI Flash (May 2021). The latter is a description of the threat with IoC and TTPs while the former state the FBI locate 16 different attacks made by the RaaS affecting critical infrastructure.
Within this 16 attacks (globaly Conti collected 400 victims in just a year, 290 only in the USA) we have not just healtcare but also 911 dispatcher centers and with the higher ransom being of $25 MLN. Enough is enough, from now on Conti is officially an enemy of the US goverment.
For instance in August 2021 Conti successfully attacked Nokia subsidiary (SAC wireless) headquarters in Chicago, in April 2021 Broward County Public School, Florida (demanding $40 MLN) and between Septmeber and October 2021 the compnay JVC Kenwood (1.7 TB data stolen plus $7 MLN ransom).
Regardless of Conti, Ryuk and Trickbot (which became a malware-as-a-service product) operations didn’t stop and the group is looking more like a company than a simple criminal gang. They are organized, they have dense internal communication and huge payrolls. In particular Trickbot is becoming wide popular between threat actors outside Conti and Wizard Spider with persistence maintenance and features addition (especially evasion techniques).
Every interesting story needs some obstacles in the protagonist way and The Wizard Spider empire is near to encounter a lot of them. In the next episode of this small saga we would cover the first arrests, leaks and insight that affected Conti and it’s enviroment. We have talked about 2019,2020 and 2021 but a lot more needs to be written. In Febbruary 2022 the world has to deal with a new war in east europe, Russia-Ukraine ware, and this event would uncover the whole Conti background.
To be CONTInued…
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.