
Everyone involved with CTF has used the infamous rockyou.txt wordlist at least once, mainly to perform password cracking activities. The file is a list of 14 million unique passwords originating from the 2009 RockYou hack making a piece of computer security history. The “rockyou lineage” has evolved over the years.
Attackers used the original RockYou file as a starting point and continually added passwords from various data breaches. This culminated in RockYou2021, a list containing a staggering 8.4 billion records. These huge wordlists are used for credential stuffing and other brute-force attacks, putting untrained users at risk of unauthorized access, like Levi Strauss experienced this year. However reality is a little different
With the 2021 version we touched high numbers but with the newest release is the (apparently) ultimate amalgamation. RockYou2024 has been released by the user “ObamaCare”
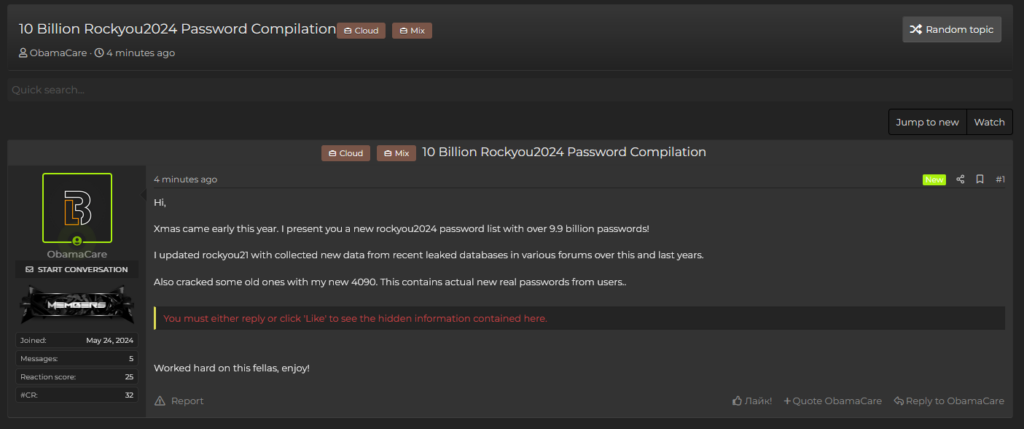
This new version added 1.5 billion of records to the 2021 version reaching the 10 billions records. A wordlist can potentially be used for a multitude of tasks and having this number of records in a single file, especially in 2024 with increasingly aggressive data breaches, is a dream come true for attackers. The user have not specified the nature of the additional records but puntualize the new data comes from recent leaked databases.
This might seem like a valuable resource for attackers, but we need to analyze the contents to determine its true worth.
While a massive wordlist like RockYou2024 can generate noise and attract attention, the underlying risk remains not that significant. Skilled attackers use targeted methods, and brute-forcing with unrefined data is inefficient for them. With the release of RockYou2024 there is no additional security meltdown nor huge security risk like have been described in these hours.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.