
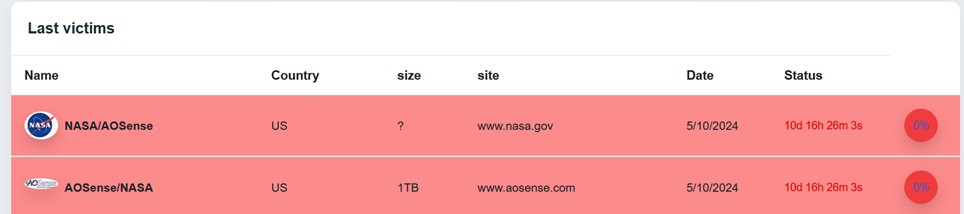
In recent years, the landscape of cyber threats has been dominated by increasingly sophisticated ransomware groups. Among them, the ransomware group Stormous has gained notoriety for targeting high-profile organizations, including government entities and technology companies. On October 5, 2024, information concerning NASA and AOSense, an American startup that develops sensors based on quantum technologies, appeared on Stormous’ data leak site. These pieces of information, labeled as “victims” by the group, have not yet been officially confirmed by either NASA or AOSense but represent an important source of intelligence to be analyzed.
Stormous is a cybercriminal group known for its ransomware and data-leak campaigns. Active since at least 2022, it has targeted a wide range of victims, including sectors like healthcare, education, and, more recently, government organizations and space agencies. The group’s modus operandi is fairly standard: they use spear-phishing techniques or known vulnerabilities to compromise victims’ networks, encrypt the data, and demand ransom for its release.One unique feature of Stormous is their active presence on social media and communication channels on the dark web, through which they publish stolen information and list their victims. This not only puts pressure on the victims to pay the ransom but also on the public and other potential victims to demonstrate their “effectiveness.”
In the specific case of NASA and AOSense, the data that appeared on Stormous’ site reports encrypted file sizes (including 1TB for AOSense), suggesting a significant breach of sensitive data. Although no precise details have been reported for NASA, the official site www.nasa.gov is listed as one of the group’s targets.
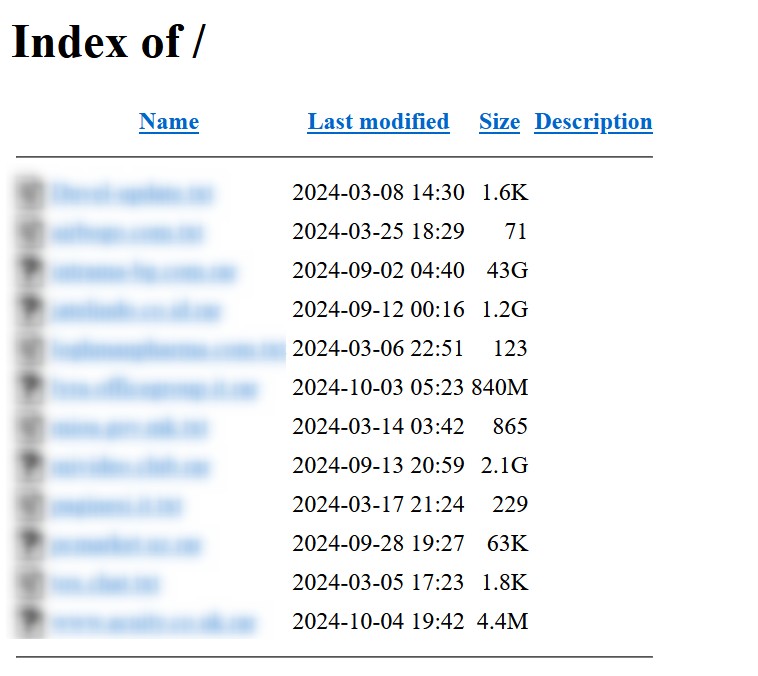
The analysis of the available information, based on visible data, indicates that Stormous uploaded a series of files and documents related to NASA and AOSense. However, the presence of indexed files and the lack of official confirmation suggest that these claims should be approached with caution. Many ransomware groups publish claims without having obtained actual access to all the declared data, aiming to create panic and force ransom payments.
If confirmed, the attack on NASA would represent one of the most severe breaches in recent years, considering the sensitivity of the data handled by the U.S. space agency. The compromise of AOSense, on the other hand, could have significant implications in terms of technological research, especially in the field of quantum sensors, an advanced technology used in critical sectors such as defense and navigation.
This alleged attack by the Stormous ransomware group against NASA and AOSense raises fundamental questions about the security of critical infrastructures and emerging technologies. While the leaked information is not yet officially confirmed, it nonetheless represents a significant concern for the cybersecurity community. Further analysis and confirmation will be needed to fully understand the extent of the breach and to adopt appropriate response measures.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
