
New threat actors often emerge every day to destabilize the digital foundations of organizations around the world. One of the most recent and disturbing cybergangs uncovered by Darklab of Red Hot Cyber team is the VANIR group, a collective known for its ruthless ransomware operations. This exclusive interview, conducted by Dark Lab group, sheds light on an enemy as mysterious as it is dangerous.
“You have to know the demons to learn how to counter them.” This phrase, frequently quoted by Red Hot Cyber in conferences and articles, underscores the importance of understanding the modus operandi of cyber criminals. Knowing the “demons” means understanding their motivations, techniques, tactics and procedures (TTPs). This approach not only helps to predict and identify threats, but is also essential for developing effective cyber defenses capable of countering attacks on their own ground.
Interviews with Threat Actors, curated by the RHC Dark Lab group, Red Hot Cyber’s Cyber Threat Intelligence division, are a crucial tool for gaining this understanding. Knowing how cyber criminals think and operate allows for continuous improvement of cyber defenses, increasing threat awareness and the ability to prevent future attacks.
First discovered through Red Hot Cyber’s constant vigilance, the VANIR group has distinguished itself not only by the effectiveness of its attacks, but also by the unique aesthetic of its data leak site. The latter, designed in a retro style, welcomes visitors with a minimalist prompt where information can be requested via fluorescent green text on a black background, evoking an old terminal atmosphere.
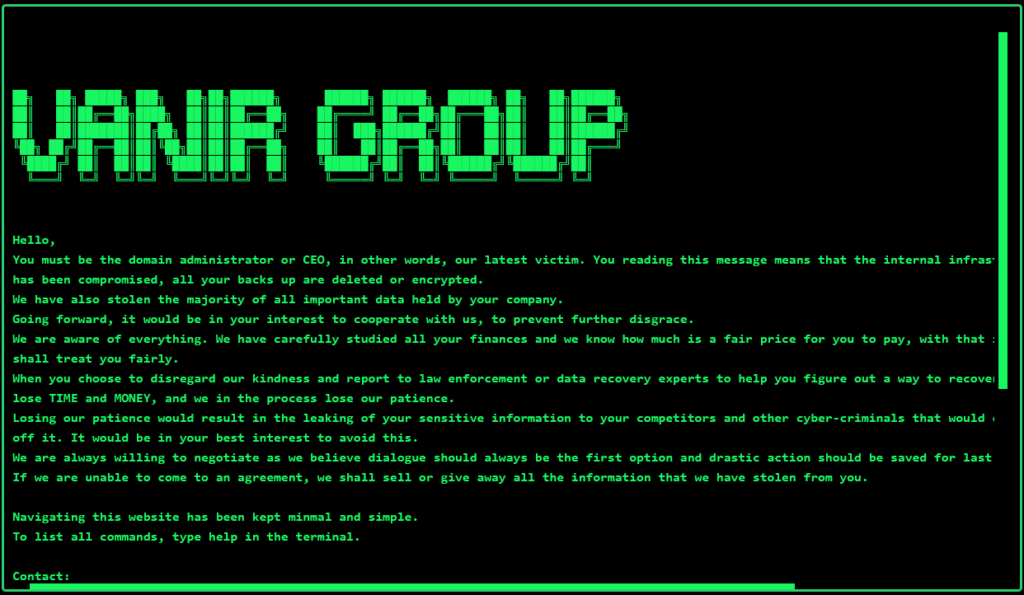
The welcome message that greets new “visitors” is direct and ominous: “Hello, You must be the domain administrator or CEO, in other words, our latest victim. You reading this message means that the internal infrastructure of your company has been compromised, all your backs up are deleted or encrypted. We have also stolen the majority of all important data held by your company. Going forward, it would be in your interest to cooperate with us, to prevent further disgrace. We are aware of everything. We have carefully studied all your finances and we know how much is a fair price for you to pay, with that in mind, know that we shall treat you fairly. When you choose to disregard our kindness and report to law enforcement or data recovery experts to help you figure out a way to recover your lost data, you only lose TIME and MONEY, and we in the process lose our patience. Losing our patience would result in the leaking of your sensitive information to your competitors and other cyber-criminals that would certainly make a profit off it. It would be in your best interest to avoid this. We are always willing to negotiate as we believe dialogue should always be the first option and drastic action should be saved for last. If we are unable to come to an agreement, we shall sell or give away all the information that we have stolen from you. Navigating this website has been kept minmal and simple. To list all commands, type help in the terminal.”
Through this interview, Dark Lab offers an in-depth look into the minds of those behind VANIR attacks, exploring their motivations, techniques, and negotiation strategies. A journey that allows us to better understand who these threat actors are and how we can defend against their devastating actions.
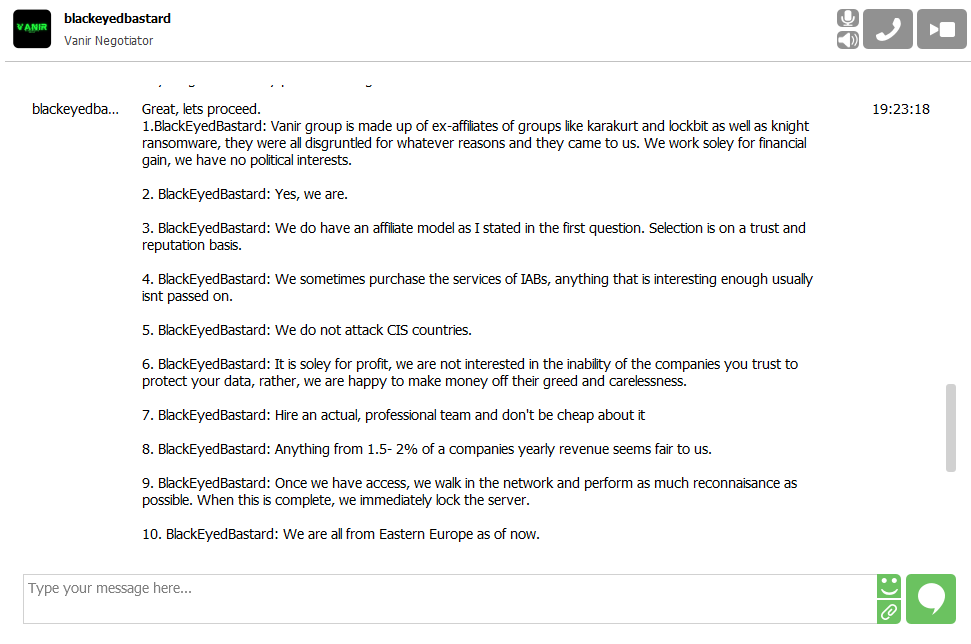
1 – RHC: Thank you guys for accepting this interview. Let’s start with a direct question: what is the origin of the VANIR group and what prompted you to engage in ransomware operations? Does the name have any specific origin?
BlackEyedBastard: Vanir group is made up of ex-affiliates of groups like karakurt and lockbit as well as knight ransomware, they were all disgruntled for whatever reasons and they came to us. We work soley for financial gain, we have no political interests.
2 – RHC: Are you a rebrand of a previously existing ransomware group or affiliates of other RaaS that wanted to go out on their own?
BlackEyedBastard: Yes, we are.
3 – RHC: Do you use an affiliate model in your ransomware operations? If so, how does it work and how do you select your affiliates?
BlackEyedBastard: We do have an affiliate model as I stated in the first question. Selection is on a trust and reputation basis.
4 – RHC: Do you currently do everything in-house (malware, breach, and ransom demand) or are you distributed across multiple groups? For example, do you make use of Initial Access Broker (IaB)?
BlackEyedBastard: We sometimes purchase the services of IABs, anything that is interesting enough usually isnt passed on.
5 – RHC: Many groups have given themselves strict rules about targets (such as not hitting hospitals and institutions for children, etc…) on which to launch attacks. Do you guys have any?
BlackEyedBastard: We do not attack CIS countries.
6 – RHC: What are your main motivations behind in ransomware activities? Is it just a way to make more money or is there a broader thought such as improving IT infrastructure cybersecurity?
BlackEyedBastard: It is soley for profit, we are not interested in the inability of the companies you trust to protect your data, rather, we are happy to make money off their greed and carelessness.
7 – RHC: If you were to advise any company to better protect itself from cybercrime, what would you recommend as the first thing to start with?
BlackEyedBastard: Hire an actual, professional team and don’t be cheap about it
8 – RHC: Report in your DLS that “we know what is a fair price for you to pay” and then “know that we will treat you fairly.” Apparently the choice is for “collaborative” negotiation. How high are your ransom demands today?
BlackEyedBastard: Anything from 1.5- 2% of a companies yearly revenue seems fair to us.
9 – RHC: Can you explain to us how your solution works briefly?
BlackEyedBastard: Once we have access, we walk in the network and perform as much reconnaisance as possible. When this is complete, we immediately lock the server.
10 – RHC: What is the predominant nationality of the Vanir group members?
BlackEyedBastard: We are all from Eastern Europe as of now.
11 – RHC: Do you receive support or sponsorship from government agencies or other organizations?
BlackEyedBastard: No, we are not an APT group, we do not receive support from any one or organisation, we cannot be bought to perform an attack on anyone we are not willing to hit.
12 – RHC: What are your long-term goals for the Vanir group?
BlackEyedBastard: To wreak havoc.
13 – RHC: Is your ransomware inspired by existing codes? If so, which ones and how did you modify them to make them unique?
BlackEyedBastard: The source code of our ransomware is written from scratch, this is not a daunting task for anyone with a bit of experience.
14 – RHC: Are there other cybergangs from which you draw inspiration? If yes, what are they and what do you admire about them?
BlackEyedBastard: Personally, I love the tenacity of lockbit, and I am a big fan of Akira.
15 – RHC: What is your philosophy in dealing with victims?
BlackEyedBastard: We try as much as possible to be fair, although we are usually strict on the management, they should have done more to protect themselves, but they failed and put the innocent at risk
16 – RHC: Your data leak site has a unique, retro design and reminds us of old CRT monitors from the 1980s. What is the idea behind this aesthetic that also reminds us of the DLS of another cyber gang such as AKIRA?
BlackEyedBastard: Yes, the UI of the site is heavily inspired by Akira, also, don’t you love nostalgia? We wanted something simple with 0 need for backend code, that was the solution. No PHP or Node running in the background, means 0 possibility of exploitation.
17 – RHC: Do you have any final messages for organizations that may become your future victims?
BlackEyedBastard: Don’t be stupid, pay your ransom, we mean business and the death of your company is nothing but some little entertainment to us. You can’t be the hero. Submit, or be destroyed.
18 – RHC: We thank you for this interview. We do these interviews to make our readers understand that cybersecurity is a purely technical subject and that in order to be able to win the fight against cybercrime we need to be stronger than you, who are notoriously often one step ahead of everyone. Would you like to add anything or make any points that might be of interest to our readers?
BlackEyedBastard: Hello dear reader, Listen up, we both know the world and the system in which we live is fucked. People raised from middle or poor class families are doomed to remain that way if they are like the sheep they are expected to be, but you are not like that. You can control your destiny, else why would you be reading this? If you are disgruntled by this unfair system, you can always reach out to us. We would show you how we can all become reach together.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
