
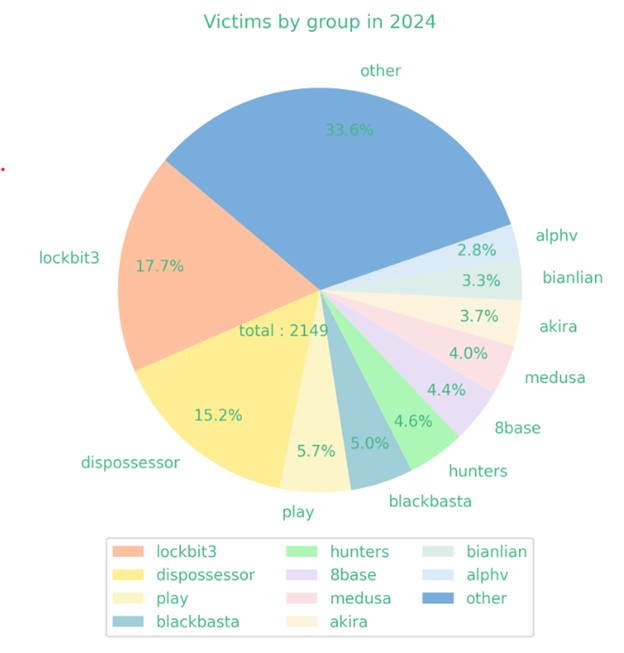
In our usual underground analysis activities, we came into contact with the cyber gang DISPOSSESSOR, which came to attention in February 2024 in the cyber threat landscape.
Accessing their Data Leak Site (DLS) one immediately realizes a strong resemblance to that of the well-known cyber-gang LockBit, and even the number of views of individual posts, taking into account that it is a blog in the onion network, has nothing to envy the elite cyber-gang.
This profound similarity suggests a possible reorganization by affiliates of the world’s longest-running cybergang, LockBit, in part because of the two Cronos operations, which saw law enforcement break into LockBit’s infrastructure and seize it twice.
DISPOSSESSOR is a peculiar cyber-gang because in addition to embracing the classic Ransomware-as-a-Service (RaaS) model, it also provides data resale services, given also the interest on the part of other cybergangs to monetize attacks that did not result in ransom payments.
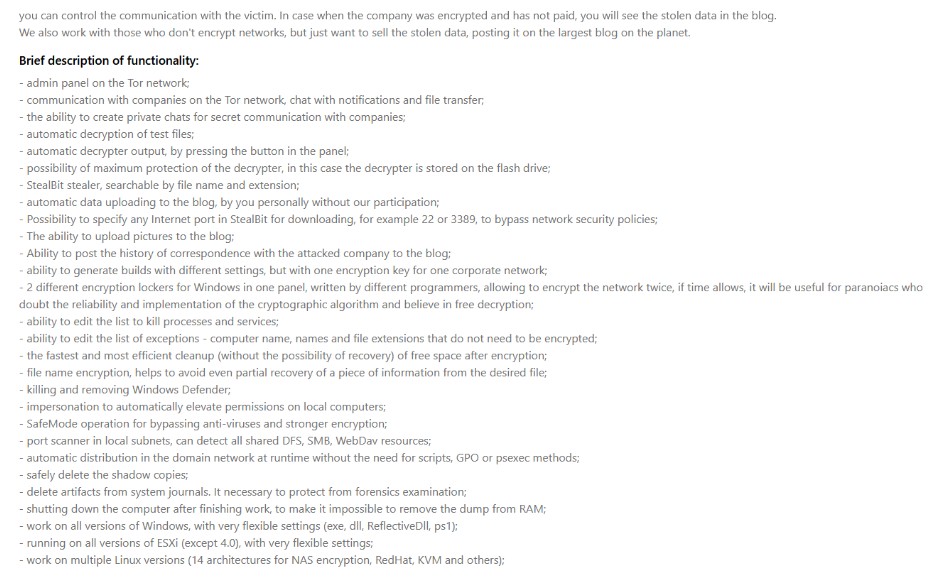
Within their Data Leak Site (DLS) in the “Rules” section, the rules that the cyber-gang adopts are published, and the many features provided to affiliates, including the publication of correspondences with affected companies directly in the DLS.This is a high-value solution, as it is also designed to target ESXi systems and allow it to work on different Linux versions (14 architectures for NAS encryption, RedHat, KVM and others).
The “Rules” section also specifies which targets will not be allowed to be hit and states the following: “It is illegal to encrypt files in critical infrastructure, such as nuclear power plants, thermal power plants, hydroelectric power plants and other similar organizations. Authorized to steal data without encryption. If you can’t tell if an organization is critical infrastructure, get help.”
We had the opportunity to interview this interesting Cyber-Gang and below is the interview.
1 – RHC: Thank you guys for giving us this interview. You are a group that appeared in early 2024 in the underground, can you tell us about yourselves in general?
RADAR & DISPOSSESSOR : First, we would like to offer a warm and sincere greeting, along with our heartfelt gratitude, to thoughtful and intelligent people. We truly appreciate the time you took to interview us and appreciate your interest and attention to this shared experience. A big thank you to the incredible Red Hot Cyber (RHC) team for actively participating in our discussion and for their insightful questions! RHC’s contributions really enriched our conversation, making it more engaging and meaningful. We look forward to more fruitful exchanges in the future!
The main motto of our DISPOSSESSOR Group is encapsulated in the phrase, “When it comes to security, the best defense is a good offense.” This powerful statement underscores the importance of taking proactive measures when it comes to ensuring cybersecurity. Rather than simply reacting to threats as soon as they occur, we believe the most effective strategy is to anticipate potential vulnerabilities and address them before they can be exploited.
This proactive mindset is critical in today’s digital landscape, where cyber threats are becoming increasingly sophisticated. By staying one step ahead, organizations can significantly reduce the risk of falling victim to cyber attacks like ours. With this philosophy in mind, our mission at DISPOSSESSOR Group is to assist organizations in the oversight of enterprise operational security (OPSEC). We help organizations create a culture of security awareness that extends throughout their operations. In doing so, we aim to provide our clients with the necessary tools and knowledge they need to effectively safeguard their information and infrastructure. Because we are the DISPOSSESSOR Group (LockBit’s main affiliates) that encompasses highly qualified specialists in the field of cybersecurity, we pride ourselves on our extensive experience in modern digital security. Our team has accumulated extensive experience over many years working to address the various cybersecurity challenges facing organizations today.
We possess a thorough understanding of the many vulnerabilities that can exist within a company’s network. This understanding allows us to quickly identify potential vulnerabilities. Our insights are based on first-hand experience, as we have studied the tactics employed that simulate attacks on networks to uncover security flaws. Through careful analysis, we have gained clarity on the various entry points for infiltrating systems.
It is critical for organizations to stay abreast of potential risks by employing robust security protocols and practices. This type of information and insight we provide is vital and invaluable, but it also comes at a significant cost when provided by outsiders. However, partnering with our group can save organizations a great deal of time and money. Companies can avoid the pitfalls associated with inadequate security measures, which can lead to serious financial losses, reputational damage and operational disruptions. In conclusion, our DISPOSSESSOR group is ready to assist companies in improving their cybersecurity. With our extensive experience and specialized knowledge, we offer a unique perspective on how to protect networks effectively.
2 – RHC: In recent years we have seen an evolution in attack techniques by cyber-gangs. How have you seen this evolution in the threat landscape, and how have you adapted to these changes?
RADAR & DISPOSSESSOR : The evolution of attack techniques by cyber-gangs in recent years has been remarkable, with several key trends shaping the threat landscape. Ransomware attacks have become increasingly sophisticated. Cyber gangs are now employing double extortion tactics, in which they not only encrypt data but also threaten to disclose sensitive information unless a ransom is paid. The dark web is becoming a marketplace for cybercrime, where stolen data, malware, and hacking services are bought and sold.
Our DISPOSSESSOR affiliates and partners actively follow all the latest trends in cyber attacks, in particular: exploitation of public CVE vulnerabilities, RCE. This involves closely monitoring the CVE (Common Vulnerabilities and Exposures) database for newly published vulnerabilities that can be exploited. In addition, our teams analyze emerging exploitation patterns and methods to gain as many initial accesses as possible.
In addition, we conduct regular training sessions for our affiliates and partners to ensure that they are aware of the latest threats, AV/EDR bypass techniques, and equipped with the knowledge to execute attacks effectively. There is a very famous quote by Bruce Schneier that fits the motivation of our DISPOSSESSOR Group: “Security is not a product, but a process.” Bruce Schneier is a renowned security expert known for his work in cryptography and cybersecurity. This quote highlights that achieving security requires continuous efforts and cannot be bought outright.
Organizations must understand that security is not a one-time investment or a simple software installation. Instead, it is a continuous cycle of evaluation, adaptation and improvement.
DISPOSSESSOR teams are constantly developing new techniques that require a flexible approach to security. By embracing the idea that security is a continuous journey, organizations can better prepare for future challenges. In conclusion, Schneier’s insight serves as a reminder that true security is based on vigilance and adaptability rather than relying solely on external solutions or products. The DISPOSSESSOR Group embodies these principles by promoting a culture of continuous improvement and resilience in the face of threats. The continuous evolution of cyber threats requires a proactive and adaptive approach to cybersecurity. By staying informed about emerging trends and implementing comprehensive security strategies, organizations can better protect themselves from the evolving tactics of cyber gangs like ours. Ongoing training, investment in technology, and collaboration across sectors are essential to maintaining resilience in this dynamic environment.
3 – RHC: Looking at your DLS, LockBit comes automatically to mind. Are you former affiliates or developers of LockBit who wanted to go out on your own? Can you tell us your motivations for opening this new RaaS?
RADAR & DISPOSSESSOR : We are former affiliates and partners of Lockbit. We created a blog similar to Lockbit’s design, because we thought it was the most informative. Our goal was to provide valuable insights and information to our audience, drawing inspiration from the effective layout and presentation of Lockbit’s resources. In the near future, we may change the design to an even more informative one. This potential redesign aims to enhance user experience by making information more accessible and engaging. We are considering integrating features such as interactive elements, updated visual content, and streamlined navigation to ensure that our readers can easily find the information they need.
Additionally, we are exploring the possibility of incorporating more diverse content types, including video of files, infographics, and Law expert interviews, to enrich the learning experience for our audience. We believe that by continually evolving our platform, we can better serve our community and keep them informed about the latest developments in our field. The main motive for opening our new RAAS called DISPOSSESSOR is independence. We are committed to developing and learning from our mistakes every day, setting ourselves apart from other teams and groups in the industry. Unlike many competitors, we do not keep in our ranks individuals who can harm our business, as we understand that such issues can jeopardize our reputation at any moment.
We take our business very seriously, feeling a deep sense of responsibility to the employees of the companies(our clients) we serve. Our priority is to help them improve their safety and security, which requires not only sober intelligence, but also a good memory and quick reactions to the fast-growing high-tech market. In an environment where threats are constantly evolving, we recognize the importance of maintaining a clear mind and a focused approach. Our decryptor is designed to decrypt 100% of files, ensuring that our clients can trust in our services. We guarantee the complete removal of exfiltrated data from our servers(unlike the LockBit), and we encourage everyone to verify this through search engines and social networks. Transparency is key to building trust; therefore, we take pride in our clean track record.
There are no negative reviews, or any tags like #hunt associated with our DISPOSSESSOR Group on social media, reflecting our dedication to excellence and accountability. Moreover, we continually invest in training and technology to stay ahead of potential threats. Our team is composed of skilled professionals who are not only experts in their fields but also share a collective commitment to ethical practices. This ensures that we maintain high standards in all aspects of our operations. By prioritizing integrity and professionalism, DISPOSSESSOR aims to set a new standard in the industry, demonstrating that it is possible to operate with both independence and responsibility. Our mission goes beyond mere profitability; we strive to create a safe environment for all our clients, fostering long-term relationships built on trust and mutual respect.
4 – RHC: Although you started in February, your DLS already has 340 posts between ransomware attacks carried out and resale of data. RaaS always needs to monetize, and reselling data is RADAR & DISPOSSESSOR: Always a way to be able to recover the money invested in an attack. How important is this need for today’s cybercrime?
RADAR & DISPOSSESSOR: At the moment we are receiving many messages through the “Contact Us” form on our blog with different offers and one of them is your interview request. 340 blog posts are just the beginning and almost all of these companies were hacked by our teams, while we were at LockBit. All files are carefully stored on secure storage servers and our own cold backups. To provide you with assurance, you can select any of the companies we work with, and we can send you an archive containing data related to that company. Our teams of data analysts possess extensive knowledge and are fully aware of the legal frameworks in Tier 1 countries. This understanding is crucial because exfiltrated data is a core aspect of our business. Downloading critical information in significant quantities related to any affected company, or organization can suffer significant problems due disastrous consequences, leading to loss of valuable intellectual property and other sensitive information, GDPR issues, costly incident response efforts, information misuse/abuse, loss of customer trust, brand and reputational damage, legal and regulatory issues. Loss of customer trust is another significant concern that arises from a data breach. The damage to a brand’s reputation can be long-lasting and challenging to recover from. Legal and regulatory issues may also emerge, further complicating the situation for the affected organization. Once a breach occurs, the cycle of recovery can feel endless as files are continuously downloaded and sensitive videos are viewed by individuals across the globe. Given these serious implications, we strongly advise against disregarding our services. The importance of safeguarding your data cannot be overstated, and we are here to provide the protection you need to mitigate these risks effectively. Ignoring the potential threats could leave your organization vulnerable to ongoing attacks and subsequent fallout that could have been prevented. 900+ TOP journalists, reporters, editors, data analysts, lawyers etc in contact with us. Proof – https://imgur.com/a/A3czM2Y
5 – RHC: How many of your affiliates’ breaches are related to the total number of posts issued versus reselling data?
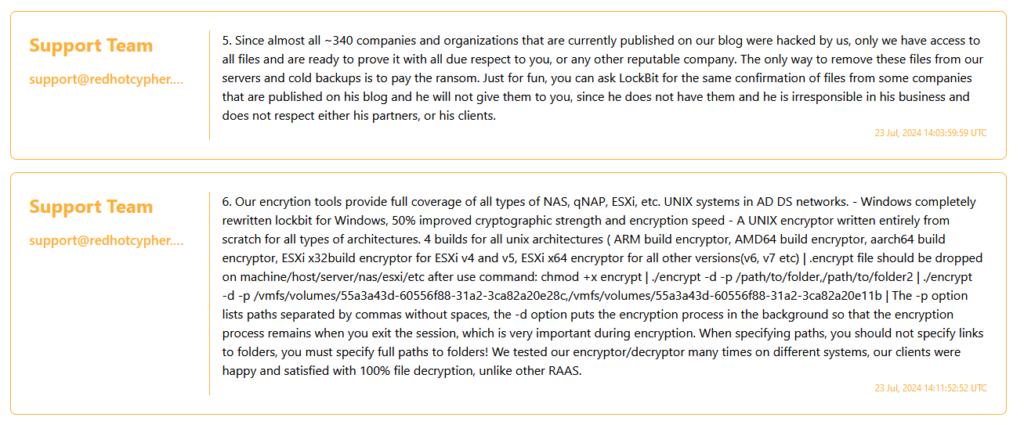
RADAR & DISPOSSESSOR: Since almost all ~340 companies and organizations that are currently published on our blog were hacked by us, only we have access to all files and are ready to prove it with all due respect to you, or any other reputable company. The only way to remove these files from our servers and cold backups is to pay the ransom. Just for fun, you can ask LockBit for the same confirmation of files from some companies that are published on his blog and he will not give them to you, since he does not have them and he is irresponsible in his business and does not respect either his partners, or his clients.
6 – RHC: Now let’s talk about your solution. We have seen a lot of features offered to your affiliates with a complete infrastructure both as beckend and encryption lockers. If you were to say, how does your program differ from other ransomware such as the popular LockBit 3.0 or Akira? If you had to explain to a potential affiliate why to start a partnership with you, what would you say from a technical point of view regarding your solution?
RADAR & DISPOSSESSOR: Our encrytion tools provide full coverage of all types of NAS, qNAP, ESXi, etc. UNIX systems in AD DS networks. – Windows completely rewritten lockbit for Windows, 50% improved cryptographic strength and encryption speed – A UNIX encryptor written entirely from scratch for all types of architectures. 4 builds for all unix architectures ( ARM build encryptor, AMD64 build encryptor, aarch64 build encryptor, ESXi x32build encryptor for ESXi v4 and v5, ESXi x64 encryptor for all other versions(v6, v7 etc) | .encrypt file should be dropped on machine/host/server/nas/esxi/etc after use command: chmod +x encrypt | ./encrypt -d -p /path/to/folder,/path/to/folder2 | ./encrypt -d -p /vmfs/volumes/55a3a43d-60556f88-31a2-3ca82a20e28c,/vmfs/volumes/55a3a43d-60556f88-31a2-3ca82a20e11b | The -p option lists paths separated by commas without spaces, the -d option puts the encryption process in the background so that the encryption process remains when you exit the session, which is very important during encryption. When specifying paths, you should not specify links to folders, you must specify full paths to folders! We tested our encryptor/decryptor many times on different systems, our clients were happy and satisfied with 100% file decryption, unlike other RAAS.
7 – RHC: What are the specific capabilities of the StealBit tool and how does it allow you to circumvent network security policies?
RADAR & DISPOSSESSOR: We use own private developments in C++/asm languages mainly to bypass EDR/AV and Network Security Policies in AD DS networks.
8 – RHC: Can you tell us how decrypter security is ensured and what are the options for maximizing this security?
RADAR & DISPOSSESSOR: Information about our decryptor is classified as secret. But as we answered earlier, all our clients were satisfied with the 100% successful decryption of all files, unlike other RAAS, and most importantly, in each case we deleted all files from our servers and cold backups. We also cannot name the names of the companies that bought the decryptor + exfiltrated file removal from us, since this is confidential information.
9 – RHC: Can you describe the type of encryption used by your ransomware? What encryption algorithms do you employ and how do you ensure that victim files remain inaccessible without the decryption key?
RADAR & DISPRESSOR: Our private RADAR & DISPOSSESSOR encryptor employs a sophisticated encryption mechanism that combines RSA and AES encryption techniques for its operations. The ransomware is particularly notable for its use of the RSA-1024 algorithm to securely encrypt the file encryption keys, which are then used with the AES-256 algorithm to encrypt the actual files. Key Details of RADAR & DISPOSSESSOR Encryption:
Overall, the combination of RSA for key exchange and AES for file encryption creates a multi-layered security model that enhances the effectiveness of the RADAR & DISPOSSESSOR ransomware while complicating decryption without proper keys.
10 – RHC: Can you tell us a typical example of an attack by your affiliates? For example, are phishing techniques and subsequent injection of specific loaders carried out, or are exploits used for specific security bugs or misconfigurations, such as Remote code Execution or trivial passwords on RDP?
RADAR & DISPOSSESSOR: To find the answer to this question, you can refer to the second response we
provided previously. This particular answer contains detailed information that addresses the query thoroughly.
11 – RHC: Can you explain to us the techniques you have developed, even at a high level, to prevent your ransomware from being detected by antivirus or corporate network protection systems?
RADAR & DISPOSSESSOR: Each individual RADAR & DISPOSSESSOR ransomware team consists of affiliates and partners who utilize their own proprietary technologies to effectively bypass various security measures, including Endpoint Detection and Response (EDR), Antivirus (AV), Intrusion Prevention Systems (IPS), and Host Intrusion Prevention Systems (HIPS), among others. These sophisticated techniques are specifically designed to exploit vulnerabilities within the networks of Active Directory Domain Services (AD DS) companies, enabling them to carry out their malicious activities without detection. It’s important to understand that the methods and tools employed by these groups are closely guarded secrets. Each team continuously evolves its strategies to stay ahead of security protocols and monitoring systems, making it challenging for organizations to defend against such threats. With all due respect, we must emphasize that we have no right to disclose any specific information regarding these technologies or tactics. The confidentiality surrounding these operations is crucial, not only for the integrity of security measures but also for the safety of individuals and organizations affected by ransomware attacks.
12 – RHC: How many people to date work within your organization? You have a complex yet comprehensive solution. How many developers are working on it full time?
RADAR & DISPOSSESSOR: We have internal rules in team to not distribute this kind of information to third parties.
13 – RHC: Within your rules it is clearly written “It is illegal to encrypt files in critical infrastructure, such as nuclear power plants, thermal power plants, hydroelectric power plants and other similar organizations,” but also “It is forbidden to encrypt institutions where damaging files could lead to death, such as cardiology centers, neurosurgery departments, maternity hospitals and the like, i.e., those institutions where surgical operations on high-tech equipment may be performed using computers.” What do you think are the unwritten rules beyond which any RaaS program should not go?
RADAR & DISPOSSESSOR: Different RADAR & DISPOSSESSOR ransomware teams, affiliates and partners select various companies and organizations to target based on the outcomes generated by their tools, which help identify potential vulnerabilities and entry points for initial access. These tools often analyze a wide range of data, including network configurations, security measures, and past incidents, to determine which entities might be more susceptible to an attack. Once a target is identified, the teams meticulously plan their approach, often using sophisticated techniques to bypass security protocols. This can involve phishing schemes, exploiting software vulnerabilities, or even leveraging insider information. The ultimate goal is to infiltrate the organization’s systems and deploy ransomware to encrypt critical data, demanding a ransom for its release. Moreover, these teams may also take into consideration factors such as the size of the organization, its financial situation, and its industry, as certain sectors are more lucrative targets than others. As the landscape of cybersecurity continues to evolve, organizations must remain vigilant and proactive in their defenses to mitigate the risks posed by these malicious actors. Regularly updating security protocols, conducting employee training, and investing in advanced threat detection systems are essential strategies that can help reduce the likelihood of falling victim to ransomware attacks. The statement highlights a crucial concern regarding the use of encryption and ransomware-as-a-service (RaaS) programs in sensitive environments, such as hospitals and surgical centers. Here are some unwritten rules that should guide the ethical considerations of RaaS developers and users:
By adhering to these guiding principles, those involved in developing or utilizing RaaS can help ensure that their actions do not contribute to harm, particularly in critical areas where lives are at stake.
14 – RHC: We have noticed very strict rules for memberships, such as the requirement to deposit a Bitcoin. Excluding law enforcement, curious or newbies, how do you deal with security researchers who try to infiltrate your community to get first-hand information, perhaps for their respective cyber threat intelligence tools?
RADAR & DISPOSSESSOR: The rules for depositing 1 bitcoin are mandatory to weed out frivolous individuals and people who are going to extract confidential information from within our team. These guidelines ensure that only serious participants are involved in our operations, creating a secure environment for all members. By requiring a deposit, we not only filter out those with questionable intentions but also foster a sense of commitment and responsibility among our contributors. Furthermore, this measure helps protect sensitive data, as it discourages malicious actors who might attempt to exploit our resources for their gain. It is crucial for maintaining the integrity of our community and safeguarding the trust that we have built over time. All participants must understand that the deposit serves as a barrier to entry, promoting a culture of accountability while enhancing the overall security of our platform.
15 – RHC: How does revenue sharing work with your affiliates? Is there a fixed percentage or is it floating with respect to the affected company’s revenue?
RADAR & DISPOSSESSOR: Typically, 80% goes to redteamers, while 20% is distributed among the RADAR and DISPOSSESSOR teams. This percentage is not fixed; it can fluctuate based on several factors, including the specific project requirements, team performance, and overall priorities. We engage in discussions with each team individually to ensure that the allocation reflects their capabilities and current workload. For instance, if the redteamers have a particularly demanding project that requires more support, we may adjust the distribution to allocate additional resources temporarily. Conversely, if RADAR, or DISPOSSESSOR teams are undertaking critical tasks that require more focus, they might receive a larger share. This flexible approach allows us to optimize our efforts and ensure that each team has what it needs to succeed. By maintaining open communication and regularly reviewing the situation, we can adapt to changing circumstances and make informed decisions about resource allocation. Ultimately, our goal is to enhance collaboration among teams while maximizing efficiency and effectiveness in achieving our objectives.
16 – RHC: The pressure towards the victim generates a sense of distress creating that explosive cocktail to facilitate a ransom payment. We have seen that you post on DLS exchanges of emails with your victims and even videos of them all chronologically. How effective is this procedure?
RADAR & DISPOSSESSOR: We are not lazy to make every possible effort to achieve our goals, particularly when it comes to documenting critical files, correspondence, and other essential information. We value our time and expect that companies treat us with the respect we deserve. In today’s fast-paced digital environment, it is crucial for organizations to recognize the importance of safeguarding sensitive data. Recent events have underscored the vulnerabilities that many companies face, specifically concerning cybersecurity threats. To stay informed about the evolving landscape of ransomware and the efforts of our Dispossessor team, consider reviewing these comprehensive research reports:
LinkedIn Insights on Dispossessor: Top #2 Ransomware Team in 2024. For insights into our team’s performance and statistics, check out these LinkedIn articles:
Legal Implications for Affected Companies. All companies impacted by the RADAR and DISPOSSESSOR team’s attacks must understand that any breach involving confidential information—such as client, student, patient, partner, or employee or any other confidential data can lead to serious legal repercussions. This includes potential lawsuits for data leaks, which could have significant financial and reputational consequences. Companies must prioritize data security to avoid such risks and maintain trust with their stakeholders.
17 – RHC: Under certain circumstances exfiltrated information is sent to customers and employees. Do you then attempt what is called “third extortion” for the purpose of getting the ransom from the breached company, or is it because you demand specific ransoms from individuals?
RADAR & DISPOSSESSOR: Yes, we carry out the third ransomware extortion due to a confidential data leak in exceptional cases. This occurs if the company refuses to pay the ransom, or ignores the encryption and leakage of confidential files. Such negligence can expose its partners, employees, clients, and other stakeholders to significant risk. In these situations, we assess the extent of the data breach and the potential consequences of the leaked information. Our approach is to ensure that all affected parties are made aware of the situation so that they can take appropriate measures to protect themselves. We believe that transparency is crucial in these cases, as it allows individuals and organizations to mitigate any potential damage resulting from the data leak. Furthermore, we emphasize the importance of cybersecurity practices and the need for companies to implement robust measures to safeguard their data. This includes regular audits, employee training on data protection, and investing in advanced security technologies. By addressing these concerns proactively, companies can minimize their vulnerability to cyber threats and protect their sensitive information more effectively. Ultimately, our goal is to highlight the serious implications of ignoring such threats, encouraging companies to take responsibility and act decisively in the face of potential data breaches.
18 – RHC: Do you have specific rules that you have given yourself, such as not hitting certain areas like the CIS? Can you tell us about those?
RADAR & DISPOSSESSOR: All special rules are described in our blog.
19 – RHC: What kind of support do you provide to affiliates during operations if there are problems with encryption or uploading data to the data leak site?
RADAR & DISPOSSESSOR: We have already addressed this question in previous messages, where we provided detailed explanations and insights. If you need further clarification or wish to explore additional aspects of this topic, please let us know, and we’ll be happy to assist you.
20 – RHC: What is the long-term vision for RADAR and DISPOSSESSOR? Do you have plans to expand your activities to other industries or geographic regions? What innovations do you have in mind for the near future?
RADAR & DISPOSSESSOR: RADAR and DISPOSSESSOR teams plan to develop the Cybersecurity Law industry to ensure that third parties are protected from the detrimental effects of leaks of confidential data by companies due to cyber attacks. This initiative will involve creating comprehensive regulations that hold companies accountable for their data security practices, thereby fostering a culture of responsibility and vigilance. In addition, we aim to establish clear guidelines for data protection, which will include mandatory reporting of data breaches and the implementation of robust security measures. Training programs will be promoted to raise awareness among employees about potential cyber threats and the importance of safeguarding sensitive information. Furthermore, we will collaborate with industry stakeholders, legal experts, and technology providers to create a framework that not only enhances security but also encourages innovation in cybersecurity solutions. By prioritizing these efforts, we hope to build a resilient cybersecurity landscape that minimizes risks for all parties involved, ultimately contributing to a safer digital environment.
21 – RHC: What emerging technologies do you think will have a significant impact on the future of cybercrime? For example, artificial intelligence, to date is it a mature technology or not?
RADAR & DISPOSSESSOR: Our RADAR and DISPOSSESSOR team’s opinion is that Artificial Intelligence will have a significant impact on the future of cybercrime, but also cyber defense. Companies that have been subjected to cyber attacks should be most afraid of data leakage, since with the help of AI it is becoming easier and easier to quickly process terabytes of information. This capability allows cybercriminals to analyze vast amounts of data, identify vulnerabilities, and execute attacks with unprecedented efficiency. As we look ahead, the next chain of development could be a Cybersecurity Law based on artificial intelligence and blockchain-based decentralized file transfer. This new legal framework could establish guidelines for how AI technologies are used in cybersecurity, ensuring that they are employed ethically and effectively to protect sensitive information. By implementing AI-driven solutions, organizations may be able to enhance their threat detection and response capabilities, allowing them to proactively address potential breaches before they occur. Moreover, the integration of blockchain technology could provide an additional layer of security by creating immutable records of transactions and file transfers. This decentralization can help mitigate risks associated with centralized data storage, making it significantly harder for attackers to access or manipulate critical information. The collaboration between AI and blockchain may lead to innovative strategies for safeguarding data, but it will also present challenges. Organizations must remain vigilant as they navigate the evolving landscape of cyber threats and adapt their defenses accordingly. Continuous education on the latest advancements in technology and cybersecurity practices will be essential in maintaining robust protection against increasingly sophisticated attacks. Ultimately, the intersection of AI and cybersecurity could reshape how we approach digital security, emphasizing the need for adaptive strategies that leverage technology to stay one step ahead of cybercriminals. As this field evolves, stakeholders must prioritize collaboration among governments, private sectors, and technology developers to create a safer digital environment for all.
22 – RHC: Are there significant collaborations or rivalries between you and other cyber gangs? How do these relationships affect your operations?
RADAR & DISPOSSESSOR: Our RADAR and DIPOSSESSOR team does not collaborate with any third-party cyber gangs, as we pride ourselves on being independent and traditional professionals. are motivated establish own niche thesecurity scene This is in our handling allfilated, which treat with utmost akin to legal arrangementIn accordance with protection and laws, maintain strict to the and of information Our are to address any ofary that may arise unauthorized to data We equipped take legal against individuals including of Board of,persons, Chiefives companies if they are in leakage confidential.
Encrypted and exfiltrated (affected) companies by RADAR and DISPOSSESSOR teams should adhere to relevant regulations, including General Protection Regulation (PR) and the Computer Fraud and Abuse Act (CFAA), as well as the General Data Protection Regulation (GDPR) and similar legislation, to ensure compliance and accountability. Our team is dedicated to upholding ethical standards within the cybersecurity law landscape.
Moreover, organizations should be aware of the implications of non-compliance with these laws, which can include substantial fines, legal action, and damage to reputation. Engaging legal counsel experienced in cybersecurity law can further assist in navigating the complexities of these regulations and ensuring that all practices align with the latest legal standards and best practices in data protection.
23 – RHC: Law enforcement operations like Cronos have had a significant impact on many criminal organizations. How do you manage the risk of being detected or caught by authorities?
RADAR & DISPOSSESSOR: Law enforcement operations, such as CRONOS, face significant challenges in countries like China due to differing legal frameworks, governmental structures, and enforcement protocols. In these jurisdictions, factors such as state sovereignty, the role of local law enforcement agencies, and international cooperation can complicate the implementation of such operations. In China, the centralized nature of the government and its focus on maintaining social stability can restrict the activities of foreign law enforcement operations. The Chinese legal system operates under different principles, including the prioritization of state interests over individual rights, which can create additional barriers for international cooperation in law enforcement operations. Furthermore, both countries have unique challenges related to cybercrime, organized crime, and the implementation of transnational legal agreements. The absence of mutual legal assistance treaties (MLATs) and the complexities of extradition processes further complicate law enforcement efforts in these regions. Inside our RADAR and DISPOSSESSOR teams, there is an unspoken rule not to encrypt company files in China.
24 – RHC: If you had to tell a company which way to start in order to be resilient to cyber attacks like yours, what would you recommend?
RADAR & DISPOSSESSOR: To help a company build resilience against cyber attacks from RADAR and DISPOSSESSOR RAAS, I would recommend the following steps:
By implementing these recommendations, a company can enhance its resilience against cyber attacks, reducing the risk of successful breaches from RADAR and DISPOSSESSOR RAAS while ensuring a proactive approach to cybersecurity.
25 – RHC: What is your opinion on global cybersecurity policies and regulations? Do you think they can influence the way you operate?
RADAR & DISPOSSESSOR: Global cybersecurity policies and regulations play a crucial role in shaping the landscape of digital security across nations and industries. These policies are designed to address the growing threats posed by cyberattacks, data breaches, and other forms of digital crime. They establish a framework within which organizations must operate, outlining best practices for data protection, incident response, and risk management. They can’t influence the way we operate.
26 – RHC: Thank you very much for the interview. We do these interviews to make it clear to our readers that cybersecurity is a purely technical subject and that in order to win the fight against cybercrime you need to be stronger than you, who are notoriously often one step ahead of everyone. Is there anything you would like to say to our readers, or to potential victims of your operations?
RADAR & DISPOSSESSOR: Thank you too. Dear RHC team, we appreciate the way you work and are thankful for your qualified and deep knowledge regarding questions you asked. Your expertise brings immense value to our discussions and helps us navigate complex topics with clarity. We look forward to continuing our collaboration and learning from your insights. Your contributions make a significant difference, and we are grateful for your dedication and fast support.
About our RADAR and DISPOSSESSOR teeams reputation.
Statistics and analytics show that a company or product should be judged primarily by negative reviews, since positive reviews can be generated by bots, AI, or individuals hired by employers whose profession is to write positive reviews for money.
The debate around the reliability of online reviews is increasingly relevant, especially in the context of consumer protection and digital marketing. A few key points can help clarify the situation and suggest potential amendments to legislation and law:
In today’s fast-paced World, maintaining a positive reputation is mandatory, especially for teams involved in sensitive areas such as RADAR and DISPOSSESSOR. Our team prides itself on having no negative reviews, or harmful tags on social media platforms. This not only reflects our commitment to excellence, but also ensures that clients can engage with us confidently, knowing we adhere to the highest standards of integrity and professionalism.
When people see that there are no negative reviews, they are more likely to trust your services. A positive brand of RADAR and DISPOSSESSOR is the main goal for us. It reflects your commitment to quality and customer satisfaction, which can lead to repeat business and referrals.
If you want to access the full interview click here
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
