
Translator: Tara Lie
We often talk about the LockBit Ransomware-as-a-Service (RaaS) operation, recently remodelled as LockBit 3.0, which continues to bring important innovations to the ransomware cyber circus. Often these new alterations are so disruptive that they are adopted by other cybergangs due to how effective they are, introducing novelties or alternate ways to obtain a ransom payment.
As we know, cyber gangs have recently moved to version 3.0, which we have previously analysed to compare it to previous versions. The cyber gangs, like any regular organisation, updates and evolves its “business model” by continuously innovating – finding new ways to evade the security defences of companies, and updating their infrastructure, techniques, tactics and procedures (TTPs).
This is necessary to be both able to respond to your affiliates, and to be increasingly pervasive, as well as to find unconventional ways to monetize as much as possible.
But as we have often said, in order to extort money from a multinational, you cannot do everything alone: you need a group.
Specifically: a group of militarily organised, loyal and cohesive cybercriminals working together with different specialisations for one purpose: to extort as much money as possible from organisations.
We contacted LockBit 3.0 asking for an interview to learn more about the evolution of the 3.0 project, but also to talk about geopolitics, affiliations, monetization, percentages of ransoms paid, the evolution of ransomware and RaaS models, and also about Italy and the attacks made by Lockbit previously.
RHC: Hi Lockbit, Can you tell us more about the 3.0 project?
LockBit: A lot of upgrades, by and large the infrastructure has been expanded and the bandwidth has been increased, we can now work with an unlimited number of partners. Also, the source codes of DarkSide/BlackMatter windows locker were bought and significantly improved. There is added functionality from lockbit 2.0 such as self-spreading and elimination of a lot of bugs.
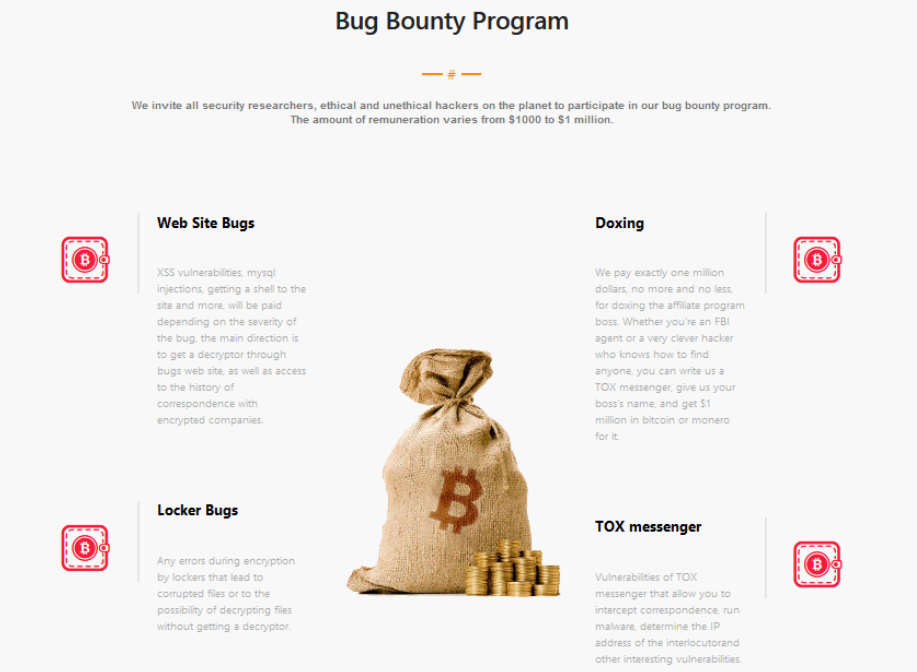
RHC: Could you tell us more about your bug hunting initiative? Is it a consequence of a cyber intrusion you suffered?
LockBit: No hacking, but there were some minor flaws that prompted us to create a bug bounty program, where at the moment we have already paid 50 thousand dollars to the individual who informed us of the bug.
RHC: The Conti ransomware team appears to be out of the game. Are you recruiting former members/affiliates of this gang?
LockBit: We don’t know who we recruit, people just come to us and say they want to work, we don’t ask them where they come from. There are no restrictions.
RHC: What is it that makes you a RaaS operation that has been on the market for 2 years? What is special about you compared to others?
LockBit: Weakness and Courage. We have a mental illness. There is no fear at all, no fear of being caught or killed. And of course the modified satellite of Elon Musk, God bless America!
RHC: Can you tell us how many people are involved in your RaaS operation? People such as developers, affiliates, support, etc…
LockBit: More than 100 people
RHC: The victims you post on your data leak site are the ones who don’t pay the ransom. Many researchers have made predictions about how many companies allow you to monetize. What is the exact percentage of agencies and companies who pay the ransoms?
LockBit: 10%-50% pay the ransom. It depends on how well the company is attacked and whether it has secrets and backups.
RHC: Will internal affairs change with version 3.0 or will they remain the same for your team ?
LockBit: There are a lot of changes.
RHC: On an international level, unlike Conti, you have not taken sides and always report that you are not connected to politics. How rewarding is this choice in the geopolitical sphere?
LockBit: This is our personal worldview, we are against war and bloodshed, we are ordinary pentesters and we make this world more secure – thanks to us companies can learn a lesson on security and fix their vulnerabilities. Conti, and their rebranding BlackBasta, are political hackers, they work to destroy infrastructure just to do maximum damage to the company. And we, in turn, benefit all the companies in the world and make them safer and more secure.
RHC: We are seeing a lot of downtime for the transition to “Project 3”. Are they related to technical problems?
LockBit: The downtime was due to the transfer of infrastructure and partners, debugging new mechanisms and above all, at the height of summer, many people take a break and are on vacation.
A Killnet post inviting members of Conti and REvil to “an unforgettable safari in the United States, Italy and Poland!”
RHC: Recently the KillNet group asked for the help of several ransomware groups for its operations. What do you think about them?
LockBit: I don’t know anything about this, but I think it’s just a counter-action in cyber-warfare, Russia gets attacked by hackers from the United States, Europe and Ukraine. Russia simply responds by creating its own cyber units, the natural course of events. For every action there is an equal and opposite reaction. The main thing is to not start a nuclear war, cyber war is not offensive and not as dangerous as nuclear war.
RHC: What are the main differences between LockBit 2.0 and LockBit 3.0 ? Where did the need to upgrade come from?
LockBit: Partners are constantly asking for new features, we respect their wishes. Project 3.0 is created on the base of DarkSide/BlackMatter source code that we have acquired, eliminating many bugs and adding the latest functionality, besides added functionality from Lockbit 2.0 such as self-propagation. And above all, a new Linux locker with support for 14 Linux architectures.
RHC: Several days ago a ransomware gang compromised an organisation operating in the healthcare sector in Italy. What do you think about attacking healthcare?
LockBit: Our opinion on the attack on medical organisations is written in our blog. We cannot be careless about the security of data that constitutes medical secrets, we must be very careful and selective with the post-payment pentest of medical institutions, so that they think about protecting information and not relying on the mercy of government groups who will just steal to destroy their infrastructure without the ability to pay the ransom.
Image from LockBit 2.0’s data leak site when ULSS6 Uganea in Padua was attacked.
RHC: We are now talking about you as an elite operation. Big numbers and big earnings. What is the ingredient that has made you stay in the market for a long time, attracting many affiliates?
LockBit: Honesty. We are the only affiliate program in the world that does not touch the ransoms obtained by partners, all other affiliate programs take payments from your wallet and then transfer the share to the partners. When the amount gets high you start talking about rebranding (as occurred with the Alpha affiliate program), they scammed the partner who had collected a large payment by closing the DarkSide program, waiting for new fools and a new big payment for the next rebranding.
RHC: Several days ago the media reported that REvil stated that the Russian government could use cyber gangs as a weapon against Ukraine. What do you think?
LockBit: I think it’s quite realistic, why not? What would you choose, a mop up your ass or a job at the computer?
RHC: A few months ago you attacked the IT infrastructure of ULSS6 Euganea, an Italian hospital. How did you find the organisation’s infrastructure, giving a grade from 1 to 5?
LockBit: 1
RHC: How do you consider the level of security of Italian organisations in general?
LockBit: 1
Original interview with Lockbit conducted via TOX Messenger
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
