
Today, the RansomHub gang of cybercriminals claimed on their Data Leak Site (DLS) an IT attack on Coca Cola.
We still do not know whether this cyber attack actually affected Coca Cola’s IT infrastructure, since there is still no press release about the incident on their corporate site.
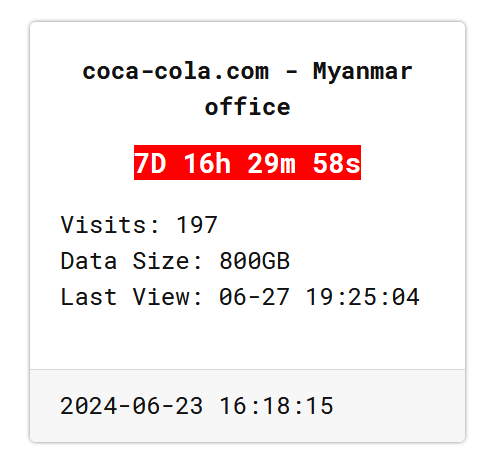
In the post published underground by the RansomHub cybercriminals, it is reported that the gang is in possession of 800GB of data, exfiltrated from the company’s IT infrastructure. They threaten publication in seven days.
There is also a countdown on the gang’s site showing that in 7 days and 16 hours, when there will be an update to the post. This course of action – as RHC readers know – generally takes place when no agreement has yet been reached on the payment of the ransom demanded by the cybercriminals. In this way, the criminals threaten the publication of the data in their possession, increasing the pressure on the hacked organisation, hoping that the payment will be made more quickly.
As is our custom, we always leave room for a statement from the company should it wish to give us an update on the matter. We will be happy to publish such information with a specific article highlighting the matter.
RHC will monitor the development of the matter in order to publish further news on the blog if there is substantial news. If there are persons with knowledge of the facts who would like to provide information anonymously, they can use the encrypted whistleblower mail.
Ransomware infections can be devastating to an organisation, and restoring data can be a difficult and laborious process that requires highly skilled operators for reliable recovery, and even without a data backup, there are many times when recovery is unsuccessful.
In fact, users and administrators are advised to take preventative security measures to protect their networks from ransomware infections, and they are in order of complexity:
Both individuals and organisations are discouraged from paying the ransom, as even after payment, cyber gangs may not release the decryption key or recovery operations may suffer errors and inconsistencies.
Cyber security is a serious matter and today it can deeply undermine a company’s business.
Today we need to change our mindset immediately and think of cybersecurity as an integral part of business and not think about it only after a cybersecurity incident has occurred.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
