
A high-ranking user of BreachForums, known as “GOD,” is reportedly selling an alleged database belonging to the U.S. Military, which purportedly contains data on over 385,000 personnel and contractors. This database would have been acquired in November 2024 and is said to include critical personal and service-related information.
If authentic, the database would contain various fields of sensitive data,
which may be categorized under the following headers:
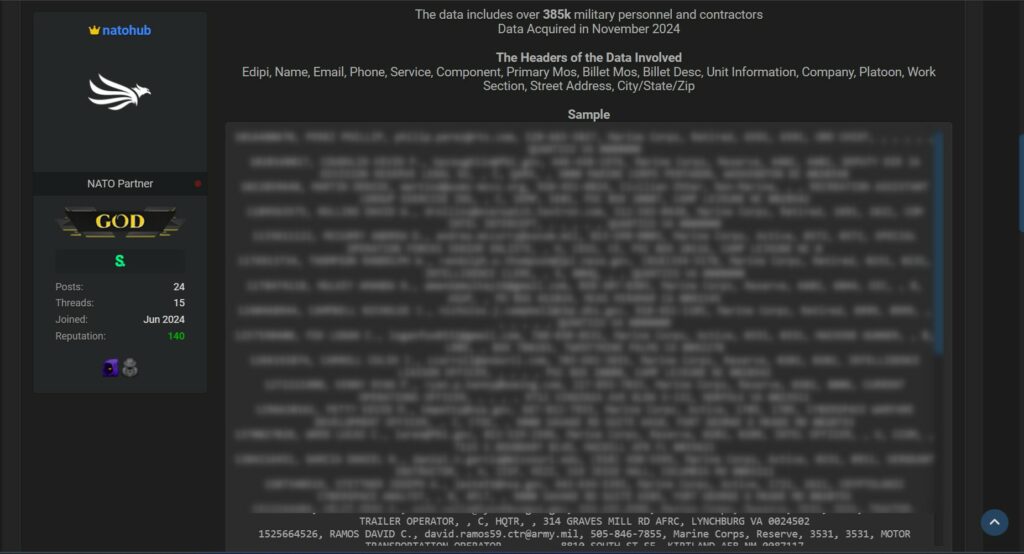
At this time, we cannot confirm the veracity of this information, as the organization has not released an official press statement on its website regarding the incident. Therefore, this article should be regarded as an intelligence source.
If confirmed, this data leak could pose a severe risk to national security by exposing sensitive information of U.S. Armed Forces members. Details like MOS codes and platoon information could facilitate espionage activities, targeted phishing, and other cyber-attack operations. The data could be exploited to profile key personnel, increasing the risk of advanced social engineering attacks.
Military data breaches are a critical concern for national security agencies. Incidents like this could expose not only active personnel but also contractors, who often work on highly sensitive projects for the U.S. government. If this intelligence source were verified, a database of this scale and with such detailed information would represent a valuable target for malicious actors and foreign espionage groups.
This potential breach would pose a significant threat to the safety of U.S. military personnel and contractors. Although the exact details of the database acquisition are unconfirmed, the cybersecurity community should remain vigilant to mitigate the associated risks. Until further verification, this information remains an intelligence source to be considered with caution.
As is our practice, we welcome a statement from the organization if it wishes to provide updates on the situation. We would be pleased to publish any such information in a specific article highlighting the issue.
RHC will monitor developments closely to publish further updates on the blog if substantial news arises. Individuals informed about the case who wish to provide information anonymously can use the whistleblower’s encrypted email.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
