
In the last few hours, the Data Leak site of the ransomware gang Play Ransomware has published a new claim: the giant MIPS Technologies (www.mips.com) has been the victim of an attack.
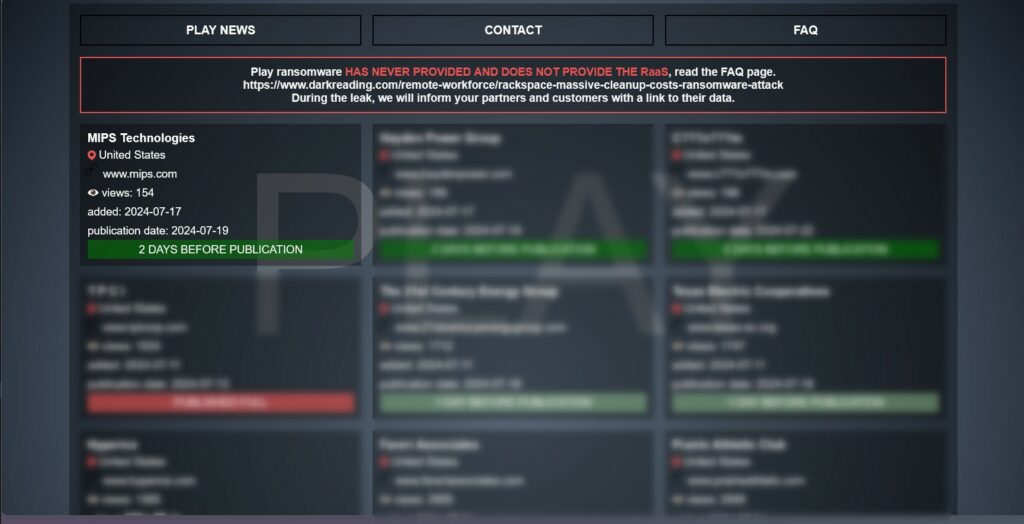
Although the official publication is scheduled for July 19, 2024, the site has already made some details public, raising concerns among the company’s partners and customers.
Play Ransomware is one of the many ransomware gangs that have emerged in recent years. These criminal groups operate by encrypting victims’ data and demanding a ransom for restoration. Play Ransomware is distinguished by its strategy of publishing stolen data on Data Leak sites, increasing pressure on victims to pay the ransom. The gang recently denied offering the Ransomware-as-a-Service (RaaS) model, in which affiliates can use the ransomware in exchange for a share of the proceeds. This was clarified on their Data Leak site with a prominent notice, likely to avoid confusion and preserve their operational reputation.
Play Ransomware is known for exploiting vulnerabilities in public applications and using stolen account credentials to gain initial access to victims’ systems. A significant example is the exploitation of the “Citrix Bleed” vulnerability (CVE-2023-4966), which allowed the group to access sensitive information and conduct targeted attacks. Once access is obtained, the group uses a variety of legitimate but compromised tools to carry out its operations. Among these are PowerShell, Cobalt Strike, Mimikatz, and WinSCP, used for lateral movement, data exfiltration, and persistence within compromised networks.
Play Ransomware has hit over 300 organizations worldwide, including critical infrastructures and major cities like Oakland and Lowell, causing significant operational disruptions and the theft of sensitive data. The group tends to focus on small and medium-sized businesses, managed service providers, and government entities, with particular attention to North America and Europe. The group does not include ransom demands directly in the ransom notes but invites victims to contact them via email, usually with domains ending in @gmx.de. Payments are requested in cryptocurrencies, adding an additional layer of anonymity and difficulty for law enforcement to trace the funds.
MIPS Technologies is a prominent name in the field of microprocessor technology. Founded in the 1980s, the company was a pioneer in the development of RISC (Reduced Instruction Set Computing) microprocessor architectures. These processors have found applications in various sectors, from embedded devices to servers and telecommunications systems.
Over the years, MIPS has introduced numerous innovations that have revolutionized the world of microprocessor technology. Their RISC architectures have been adopted in a wide range of applications, demonstrating the effectiveness and flexibility of their designs. The company has continued to evolve, expanding its product portfolio and maintaining a prominent position in the global technology sector.
According to information on the Play Ransomware site, the attack compromised an unspecified amount of sensitive data, including private and personal confidential documents, client documents, budgets, payrolls, accounting, contracts, tax information, IDs, and other financial information. The attack was added to the site on July 17, 2024, and the full publication is scheduled for July 19, 2024.
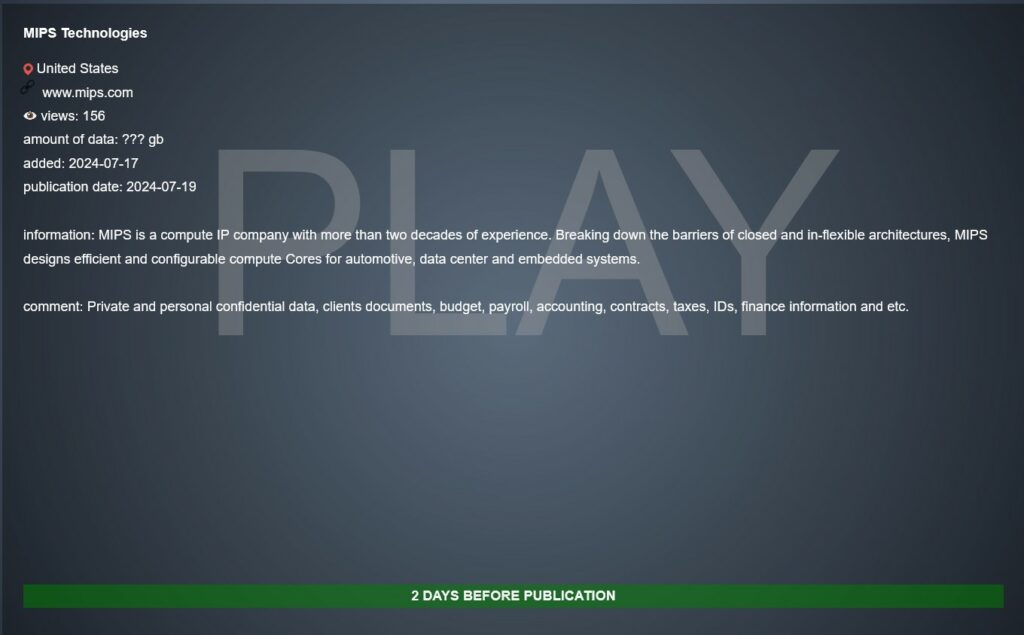
At the moment, we cannot accurately confirm the veracity of the breach, as the organization has not yet released any official press statement on their website regarding the incident. However, if confirmed, the data breach could include sensitive information about clients, internal details about ongoing projects, and other critical data.
This article should be considered as an ‘intelligence source’ rather than a definitive confirmation of the data breach. The wait for an official statement from MIPS Technologies is crucial to verify the extent of the attack and understand the measures the company intends to adopt to mitigate the damage.
As is our custom, we always leave room for a statement from the company should they wish to provide us with updates on the matter. We will be happy to publish such information in a specific article highlighting the issue. RHC will monitor the evolution of the situation to publish further news on the blog, should there be substantial updates. If there are people informed about the facts who would like to provide information anonymously, they can use the whistleblower’s encrypted email.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
