A recent critical vulnerability in OpenSSH, identified as CVE-2024-6387, could allow unauthenticated remote code execution with root privileges on glibc-based Linux systems. This flaw resides in the server component of OpenSSH (sshd) and is due to a race condition in the signal handler. The vulnerability was reintroduced in October 2020 in OpenSSH version 8.5p1, partially fixing an 18-year-old problem (CVE-2006-5051).
The vulnerability affects OpenSSH versions between 8.5p1 and 9.7p1. It allows attackers to execute arbitrary code with elevated privileges, completely compromising the system. This issue is particularly relevant because there are approximately 14 million potentially vulnerable OpenSSH server instances exposed on the Internet.
The CVE-2024-6387 vulnerability is a race condition in the OpenSSH signal handler, present in versions 8.5p1-9.7p1. A race condition occurs when concurrent execution of processes or threads leads to unexpected results, in this case allowing attackers to execute arbitrary code with root privileges without authentication. The problem was introduced in 2020 and reopened an old flaw from 2006 (CVE-2006-5051).
The race condition exploits the way OpenSSH handles process signals, allowing attackers to manipulate code execution. OpenSSH developers have been working on patches to address this problem, releasing critical updates. System administrators need to apply these updates immediately to protect their systems.
Attackers can exploit CVE-2024-6387 by using specific payloads or exploits that manipulate the race condition in process signals. Such methods may include:
This vulnerability is of particular concern because of the widespread deployment of OpenSSH and the severity of the impact, which could lead to the complete compromise of affected systems. Internet-exposed servers are particularly at risk, and the security community is called upon to closely monitor any exploits in circulation.
According to research conducted using the Shodan portal, there are currently 6,689 hosts on the Internet with port 22 exposed and the vulnerable version of OpenSSH_9.7p1. The distribution of these hosts is as follows:
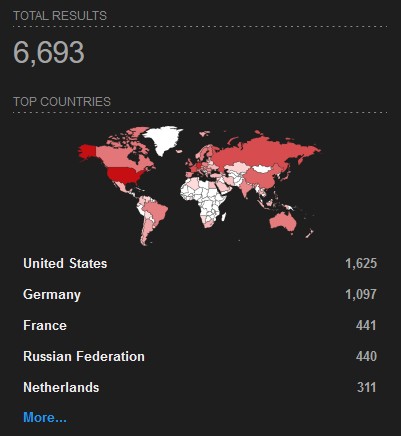
The security implications for systems with the SSH port open and exposed to the world are significant:
Persistent Threat: Once compromised, a system can be used as a persistent access point for further attacks, both within the network and to other networks.
The discovery of this vulnerability underscores the crucial importance of security in open source software and the need for constant vigilance and maintenance. Incidents such as this demonstrate how old vulnerabilities can reoccur, requiring continued attention from developers and system administrators.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
