
Author: Roberto Villani, Tanslate: Vincenzo Marcovecchio
Why will the cyberg wars, indeed the cyber-guerrillas, be more and more present and involve us more and more?
The short century, the 1900s that we have left for more than 20 years has left us the logic of the opposition between states. If at the time the conflict was between east and west, today it is much more extensive and sees the participating actors always in opposition, no longer ideological but strategic.
We have always said that natural resources are the main element of conquest, first of all water that guarantees life and therefore existence itself, and to follow all the other natural elements that can guarantee the existence of peoples. This is why every country makes claims on territories in the world where the main resource, water, is very present.
Enemies, friends, allies
It is clear that those countries that have been less fortunate and have deserts or territories where it is impossible to extract or produce wealth are always at a disadvantage. The economic disintegration caused in the former USSR has left enormous repercussions in the new millennium, the countries that had linked themselves to the USSR were left without support and still do not want to be linked to the US, at least apparently, because the adage that “pecunia non olet “. The international panorama therefore sees countries in struggle, with relative alliances, sometimes firm and sometimes liquid, facing each other or forging alliances, in order not to destroy each other.
We see very clearly that the USA, in its position of “masters” of the world, imposes rules or economic instruments on other countries less inclined to lower their heads, very heated verbal conflicts occur in internationally recognized forums such as the UN, or in other situations of international scope.
We see the other countries responding more or less energetically to these impositions, but under the agreements, the secret meetings, the strategic moves always take place. It is the power of diplomacy that parallels that of strategy. A former US president also coined a philosophy for this way of doing things, calling it “strategic patience”, because clearly unleashing large-scale conflicts doesn’t help anyone.
As it happened during the Cold War, where the two nuclear powers faced each other by exposing their respective nuclear arsenals, going so far as to open the silos threatening to use the missiles, without ever pressing the button – fortunately – today the same thing happens between the powers in conflict. Another legacy of 1900. The MAD (mutual assured destruction) which guaranteed the destruction of the participants in the war in the event of a nuclear attack, and also the MAD today is very evident among countries, especially between North Korea and the USA.
So why will the cyberguerrilla stay long?
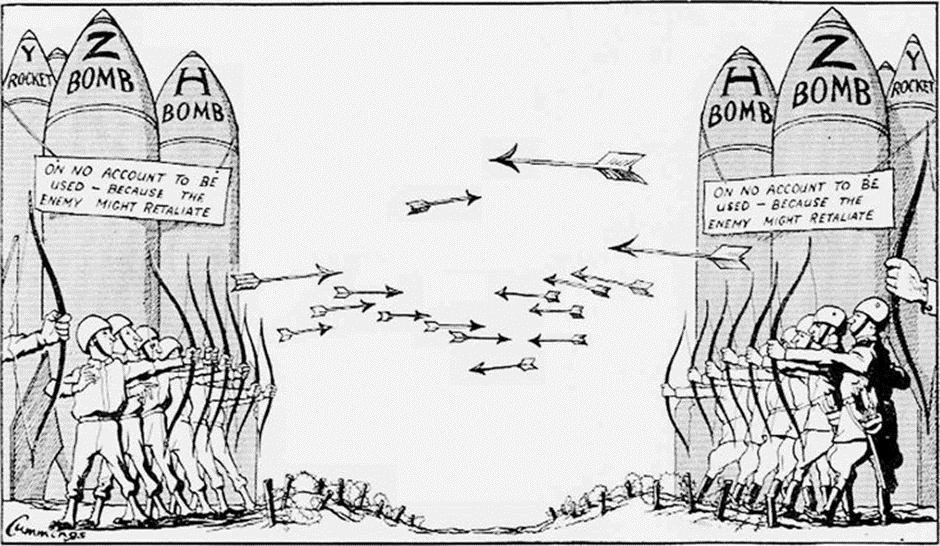
The cyber guerrilla will remain for a long time simply because the MAD guarantees it. No country in conflict will have the courage to launch a nuclear missile or attack its opponent first, there will be threats, there will be attempts, moments of tension, but no one will dare to push the button – just look at the history of the past to understand that We’ve had many fools who could do it – but it didn’t happen. The battleground will therefore only be cyber technology.
The US, if you think about it, has never attacked countries that knew how to possess nuclear weapons. They have never moved their always advanced and economically strong army to countries that know how to possess nuclear weapons. They make an underground war on them, of attrition, of diplomacy, but they have never attacked as they did with other countries, such as Iraq and Afghanistan.
The information of the US intelligence services and their allies always report precise details about the nuclear strength of the hostile country, in addition then the Open Source Information corroborates the intelligence information obtained from the secret operating cycle, therefore the collection process that takes place dictates the strategic political decision.
So what better weapon to attack without pressing the red button?
The answer is cyberguerrilla. Hundreds of attacks carried out every day, on a large scale in order to weaken the enemy, simulations of aggression, cyber countermeasures, experiments of hardware and software destruction, cyber battles in the economic, information, communication sectors, alteration of technological elements produced and resold , disinformation, destruction of operational intelligence cells, blackmail or sabotage but it will all be related to the IT world, because this will be the battlefield of the near future

Since 2017, the surge in cyber attacks has been evident, why? If you remember the US president at the time, it was Donald Trump and in his speech to the UN that year he made it clear that it was his intention to stop the North Korean nuclear program, at any cost. This idea is not just of Trump, even those who preceded him have always had this intention, the story tells it very well.
If attempts were made to negotiate, they always took place because it was announced to the world that something was wrong in North Korea. And it did not go above all in the nuclear sector.
But North Korea has had the only leadership in the Kim dynasty since the 38th parallel border was created, and totalitarian or dictatorial regimes always enjoy two advantages over democracies. The speed of decisions and the long duration of the strategy. Unlike democracies that at each presidential or government election have to review their political programs, and decide what priorities should be, dictatorships, on the other hand, not giving a damn about the peoples, decide what to do, more directly and without parliamentary votes.
Since 2017, therefore, precisely by virtue of the MAD, the new clash option is cyber only. The groups of North Korean and Chinese cyber criminals have received indications from their respective “leaders” to develop the best operational and guerrilla strategies to counter-attack and respond to the attacks that will be brought to them from all sides.
Modern MOOTW (military operations other than war) will become more and more increasing, we know and have repeatedly said that the field of action of this new conflict does not exist, because it is everywhere. Modern cyber guerrillas will never ask where to fight, because physical space does not exist and therefore the battle can be anywhere in cyber space.
Already since 1985, the countries most attentive to cyber development, but above all the countries with less strength in terms of economic availability to be used in arms and armies, have begun to think about the cyber sector, in order to effectively counter the USA. The latter too often engaged in resolving wars on the ground, have allowed an advance of the little ones towards this sector which is now important.
Who would have thought that Iran and North Korea came to have cyber “weapons” capable of attacking the US?
Many analysts and terrorism experts perhaps underestimating the strength of cyber damage, have provided non-detailed information on this sector, or have deliberately not considered it, and here today and for a long time ahead, we will have the cyber guerrilla that will involve.
What can we mere mortals do then?
First of all, having an awareness of the tools available is essential, thinking that you are part of a community that will have to face these attacks is also essential in order not to be deprived of resources, both natural and technological. Cyber technicians and experts will have to, if they have not yet done so, consider how the intelligence cycle helps them every time they find themselves having to make decisions, hire staff, frame a problem.
Having an awareness of the risk will certainly help to know the possible attacks, to know the cyberguerrilla groups present knowing that Kimsuki, Reaper and Lazarus, are not exotic names but North Korean groups. Understanding the socio-economic aspects of countries that produce more cyber gangs, for example, helps to develop against targeted attacks on specific issues, such as economic, corporate or territorial issues. In short, you do not have to become 007 secret agents, but have a broader view of the battle front, because it will be possible – it has already happened for some years – to engage in a cyber battle from any room equipped with a computer and the battleground is everywhere. Around us.
We often hear about cyber crime, indeed the topic is very hot and current in recent months, never before has the cyber sector been under the lens of the media mainstream because crime linked to the cyber sector has hit mercilessly in every sector or work and economic activity.

Of course there are no victims like a mafia attack, or a robbery attack, but it is always a crime, cybercrime, but crime. And if in the standard criminal world that we know from the news and which often saddened entire generations – I grew up in the era of Italian terrorism of bombs and political killings – the law used force to counter it, and this force allowed the safeguarding of institutions, the economic system and society, cybercrime is not yet “closed” by rules or laws that allow an effective fight. But who are the cyber criminals or cyber criminals?
Often in the media, on TV, or in speeches among cyber experts, the word “hacker” is used in its negative sense, and personally I don’t agree with this very reduced way of identifying the cybercriminal. Of course, the translated definition refers to “pirate” and whoever takes possession of something without the consent of others can be defined as a “pirate” especially for those who grew up with Salgari’s readings or adoring the stories of the adventurers of the 1700s who sailed the seas and attacked the various ships of European powers – the similarity with the web, the sea, and the ships, the databases available on the web, can increase this verbal parallelism, but I repeat, having seen many episodes of Captain Harlock I like to think that there are also good hackers and that everyone else is cyber criminals, not hackers.
Just as there are “categories” in the criminal world, cyber criminals also belong to categories in the cyber world.
There are the political activist groups, the lone wolves and the cybergangs. The latter then more dangerous, because operating without ideals, without identity, they act for money, or by proxy. Here the cyber world opens up into another dimension, and like the classic but no less dangerous criminal world, this dimension offers an infinite number of opportunities.
If the group of political activist cybercriminals carries out its criminal action on the web by claiming political, civil rights, forms of revolution against a system that for them is corrupt or to be demolished, the signature of the attack can be read well. A cyber-security expert who has a minimum of knowledge of intelligence or sociology, can easily identify the gesture already towards whom it is addressed – a bank office, a multinational, an opposing political party, or an opposing or opposing political exponent, but however with links to political-social activity and today also environmental, because the topic of the environment is very hot

In the same way, a web investigation can be made towards the “lone wolf”, an expression widely used in real terrorism, where the subject without structural ties to terrorist organizations, actually carries out a massacre or an attack. This action, devoid of references to any of his previous moves, makes investigations more difficult, but not prohibitive. And as in terrorism, even in the cyber sector the “lone wolf” acts without reference. It can be a guy locked up in a cellar, with his beautiful PC who enjoys entering the servers of some educational institution, as well as the expert employee of the antivirus company who challenges himself and his colleagues in a dangerous computer game, creating a serious problem with a chain reaction (reminds you of something similar to bacteriological viruses?) or the nerdy freak friend we all had and we asked to pass his math homework in high school because he knew how to do them, and today we understand why … he knew how to do !!
In short, different types of people, who must be faced in a different way in the relative contrast. If for the cyber political activists, it is possible to act on several levels of contrast – from dialogue, to the prospects of claiming, to ending agreements, also passing through the use of legal force, even the lone wolf can be led on different investigation tracks and outline its profile in order to activate an effective contrast action. And the cyber-gangs?
Here the discourse is more complex, the gang acts in concert, so there are more people who gather together – like political activists – an association can already be a reason for fighting crime, at least for Italian laws, the purpose of their action. is?

Here we have to “unpack” the gang well, we have to understand above all the target they hit, what relevance the target has in the social world, whether a small entrepreneur who produces water heaters or a large industry that produces centrifuges for nuclear plants. If the target has international ties with other companies in diversified sectors, if the target has a property attributable to a country where civil rights are absent, or a multinational property that acts across the globe in blatantly violating local regulations. If the target has a secret project that they do not want to disclose, if it is an industry in a strategic sector for the economy of the country where it is physically located.
Multiple evaluation factors that need to be measured, before simply defining the Hacker group! Correct information about it helps a lot to understand the type of threat, helps prevent it, helps identify latent threats. In the interconnected world we live in, there are no longer alliances between countries, only competing countries, which have different interests and different needs.
And just as “games without borders” used to take place – sorry for the legacy of my 80s – even today these very dangerous cyber games have no borders. This lack of limits, of lines of respect, of rules, of conventions, is not only still not regulated at an international level and even less at an internal level, but it favors the increase of cyber-gangs that are controlled remotely by the “state nations” Who have those different interests and different needs for their business, use these cyber gangs to bring attacks to the cyber world.
In modern geopolitics, physical territory has become important because the resources of the territory are not available everywhere, and whoever seizes or holds these resources has an advantage over others. Even more, those with cutting-edge critical infrastructures can impose economic activities on others who are less equipped – think for example of gas pipelines and their path in various countries.
And so, countries with demographic, social, distance or geographic problems recruit cyber-gangs to attack the most “fortunate” or most dangerous countries.

How much does a cyber gang of ten people and their computers cost, compared to an army to arm, dress, pay, with relative internal social clash between interventionists and pacifists, to be able to send into enemy territory? How much does it cost to develop software that produces damage once installed on some PCs? Does this cost the same as an army?
Quoting James Madison who said “no country can keep its freedom in the midst of continuous warfare”, one can think that cyberwarfare does not exist, but cyberwarfare does exist.
And here then is that the cyber gangs become cybernetic guerrillas, as they had already told here on these pages, guerrilla is one thing, and war is another.
Just as soldiers who make war are not guerrillas, hackers are not all criminals. Let’s explain it before identifying a community of people, passionate and with years of studies behind them that can really make a significant contribution to the defense of the country in every fundamental sector of the economy, wrongly.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
