
The Pro-Palestinian group BlackMeta (or DarkMeta) announced on August 1, 2024, on their official telegram channel that they conducted a destructive attack on the NSO group’s infrastructure, including the central domain. Along with the site of the Israeli intelligence group, the Europol site also suffered the same treatment by undergoing a strong DDoS attack.
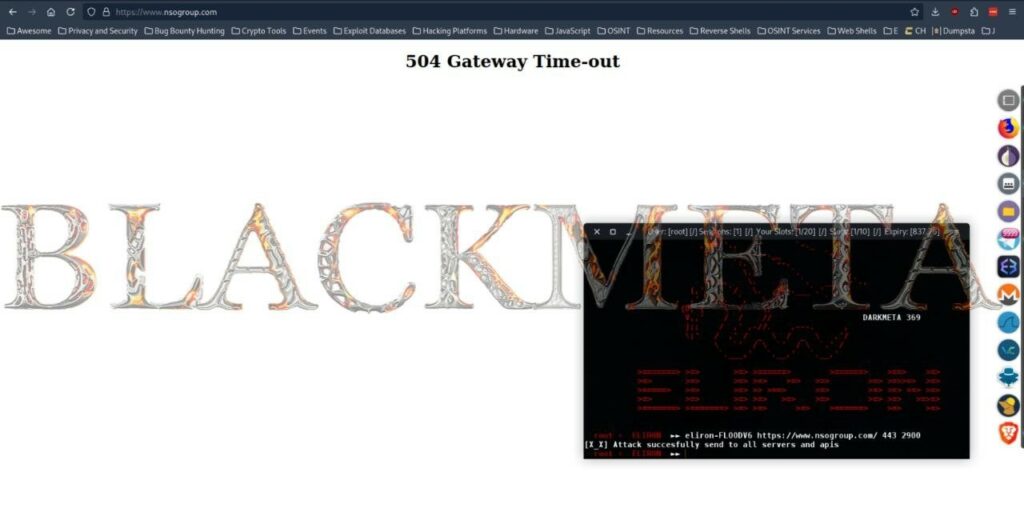
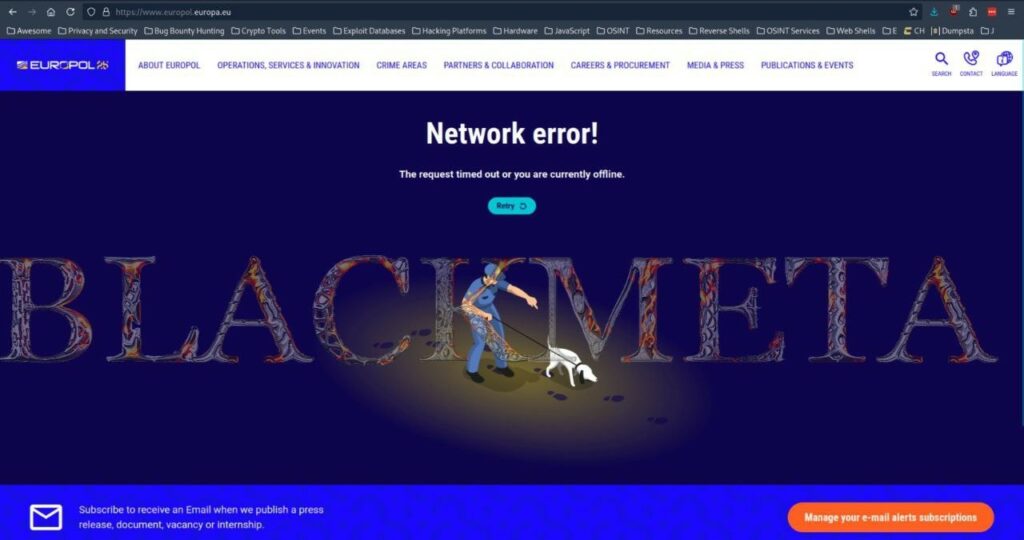
On August 3, BlackMeta wanted to update the status of the attack by stating that both sites remained unreachable for at least 24 hours. The group also wanted to clarify the emergency mitigation methods initiated by Europol by bragging about their failures in the face of their attacks.
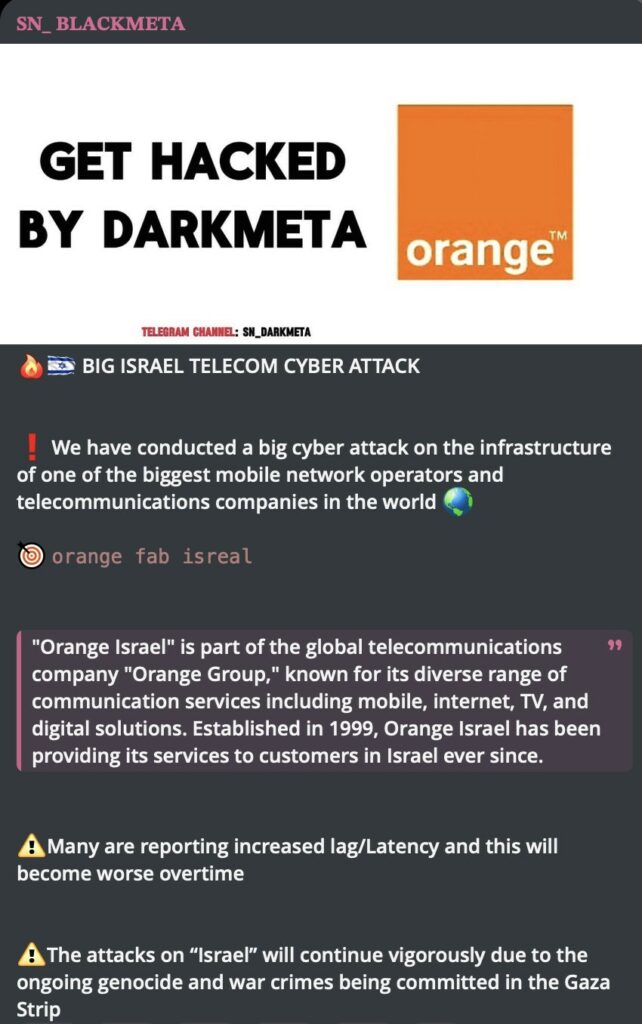
DarkMeta is no stranger to attacks on Israeli digital assrt, the whole thing started in April 2024 with the attack on Orange Israel telecom leading to heavy lag and disruption. In the claim they promised to continue their attacks on Israel because of “the current genocide and war crimes committed in the Gaza Strip.” More than 150 domains suffered disruptions and the company’s API was not usable in 6 different states for the duration of the attack.
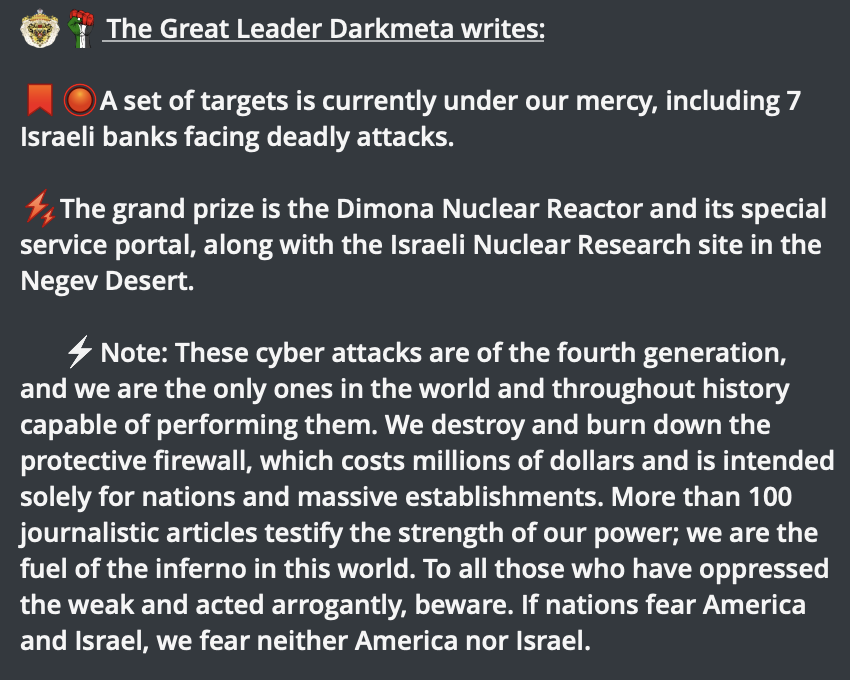
Their promises were kept well before the recent attack on the NSO infrastructure, such as at Israeli Bank and the Jerusalem Post newspaper. The group is highly influenced by the Israeli-Palestinian war and claim to have a list of at least 7 targets as future victims, including the Dimona Nuclear Reactor.
NSO (an acronym for the 3 founders Niv, Shalev and Omri) is a private Israeli company specializing in cyber-intelligence solutions, the group accepts as clients only and exclusively governments with the premise of creating tools for countering crime and terrorism. The company’s most famous product is Pegasus spyware, a sophisticated malware that exploits a 0-click vulnerability present in specific versions of iOS and Android. Once the exploit is launched, Pegasus is installed in the victim’s device allowing it to extract data from the most common messaging apps, calls, SMS, real-time location, and more with high reliability. For those who want to learn more can view the report by CitizenLab who were among the first watchdogs to discover and analyze the malware. Israel defines Pegasus as a weapon needing direct approval from the government for the use and development of variants, among the controversies regarding NSO many relate to the use of this malware.
Pegasus has been used against journalists, politicians and human rights defenders creating problems for geopolitical balances leading the U.S. to blacklist not only the spyware but the NSO group in its entirety by prohibiting American companies from selling their technologies to the company [1].
In December 2023, NSO released a transparency report stating (on the introduction, written directly by the CEO) how the Palestinian terrorist attack that took place October 7 highlighted the need for a tool like Pegasus and specifying what Pegasus does not and is not.

Such statements seem to presage a possible (silent) return of spyware utlization both outside and inside the borders of conflict countries. This may be the motivation of the DarkMeta group to add NSO to their target list.
The GeoPolitical landscape is increasingly influencing the motivations of different (seemingly) independent groups by leading them not to fear large and coveted targets. These kinds of attacks stand in the gray line between right and wrong leaving room for questions about how to judge the different actors involved. One of the dilemmas to be faced, when the war situation in Europe and the Middle East stabilizes, will be to judge whether the Ethical Hacking and White Hat definitions should be updated or even considered unnecessary and extremely limiting.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.