
During our reconnaissance into the underground world and criminal groups conducted by Red Hot Cyber’s threat intelligence laboratory DarkLab, we stumbled upon a Data Leak Site of a cyber gang never monitored before: NightSpire.
NightSpire is a new ransomware group that has recently emerged on the cybercrime scene. Although no previous information is available about this actor, an analysis of their data leak site (DLS) and their communication provides some key insights into their strategy and operational methods.
The group portrays itself as an unstoppable threat to businesses and promises to exploit every vulnerability to their advantage. Below, we analyze the details of their portal and the potential implications of their activities.
The “About” section of NightSpire’s website contains an intimidating message, typical of ransomware groups aiming to instill fear among businesses. The language used is reminiscent of well-known actors like BlackCat, LockBit, and Conti, emphasizing their intent to target vulnerable organizations and threaten them for ransom.

Text from the “About” section:
“NightSpire, the shadowy architects of digital chaos, thrive on shattering the sanctity of corporate fortresses. With ruthless precision, we infiltrate the deepest vaults of data, leaving no byte untouched. Fear us, for NightSpire is the harbinger of your downfall, the unseen hand that will exploit your every vulnerability until you kneel before our demands.”
This rhetoric is a clear example of cyber-intimidation, aimed at reinforcing the group’s image as an unstoppable threat and destabilizing their victims.
NightSpire operates a data leak site, where they publish information about compromised companies—a common practice among ransomware groups. The portal has a “Databases” section, listing victims along with details such as:
Based on the analyzed images, some of the affected companies include:
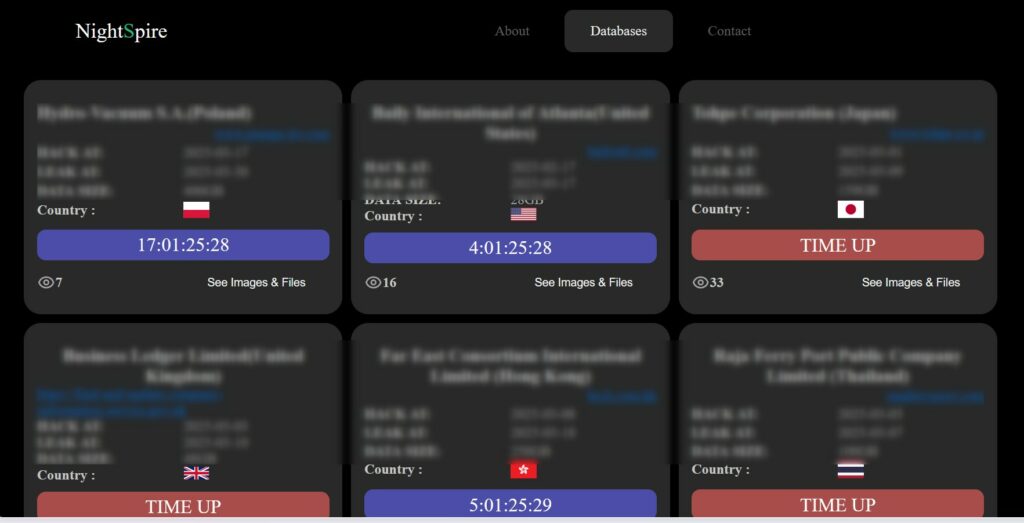
Some of these leaks are still on a countdown, suggesting that the group follows the double extortion strategy: threatening to publish stolen data if the ransom is not paid. When the timer reaches zero, the data is made public.
This technique is used to exert additional pressure on victims, forcing them to pay to avoid reputational damage and loss of sensitive data.
NightSpire offers multiple contact methods on their dedicated page. In addition to classic email services such as ProtonMail and OnionMail, they also have a Telegram channel, which ransomware groups often use to communicate leak updates, negotiate ransoms, and provide instructions to victims.
Identified contact methods:
The Telegram channel is likely used to announce new attacks, interact with victims, and manage communications with potential affiliates or data buyers.
Although detailed information about their origin or attack techniques is not yet available, some elements suggest that NightSpire could be an emerging group with strong influences from existing RaaS (Ransomware-as-a-Service) models.
Possible operational characteristics:
It remains to be seen whether this is an entirely new group or a rebrand of an existing actor.
NightSpire presents itself as a new ransomware threat. The lack of references to previously known groups makes it difficult to draw a direct line to existing actors, but their modus operandi is clearly inspired by well-established techniques.
Organizations must adopt cyber resilience strategies, strengthening endpoint protection, implementing incident response plans, and improving staff training to mitigate the risk of compromise.
We will continue monitoring NightSpire to identify their tactics and operational procedures, assessing their impact on the global cybercrime landscape.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
