On July 3, 2024, the Australian research institute Harry Perkins was the victim of a ransomware attack claimed by MEDUSA on their official DLS. More than 4.6 Terabytes of CCTV recordings inside the main building are the data being held hostage. A payment of $500,000 is demanded for the deletion of the data and the same amount to be able to download it. Additionally, for $10,000 the victim can add 24 hours to the countdown that started 9 days ago.
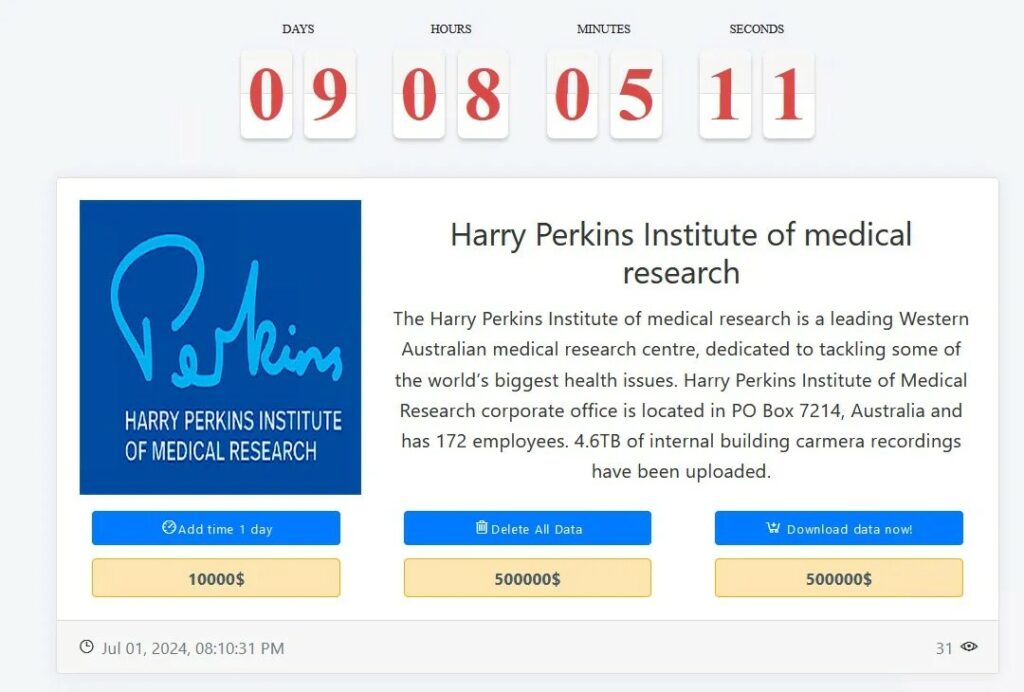
The nature of the data attacked (video recordings) is unusual compared to other ransomware attacks, the privacy of the 172 employees and collaborators is at risk, along with internal movements within the company.
As of the writing of this article, there has been no statement from the company, but confirmation is expected directly from the victim, as it is unclear whether the institute itself or a third-party entity responsible for video surveillance was attacked.
Discovered in 2019, MEDUSA is a RaaS (Ransomware-as-a-Service) that has targeted organizations in the education, healthcare, and industrial sectors, primarily in the US, since the beginning of its operation. Their DLS called Medusa Blog was introduced only in 2023, showcasing a multiple extortion scheme with the three classic “post-pentest services” – additional time, data deletion or complete download of encrypted data.
According to a note from the CISA’s #StopRansomware project, the group heavily exploits vulnerable RDP configurations and phishing emails with the malware attached, which is executed directly by the victim through social engineering. In the past year, the use of credential brokers to gain initial access through the reuse of user credentials is suspected.
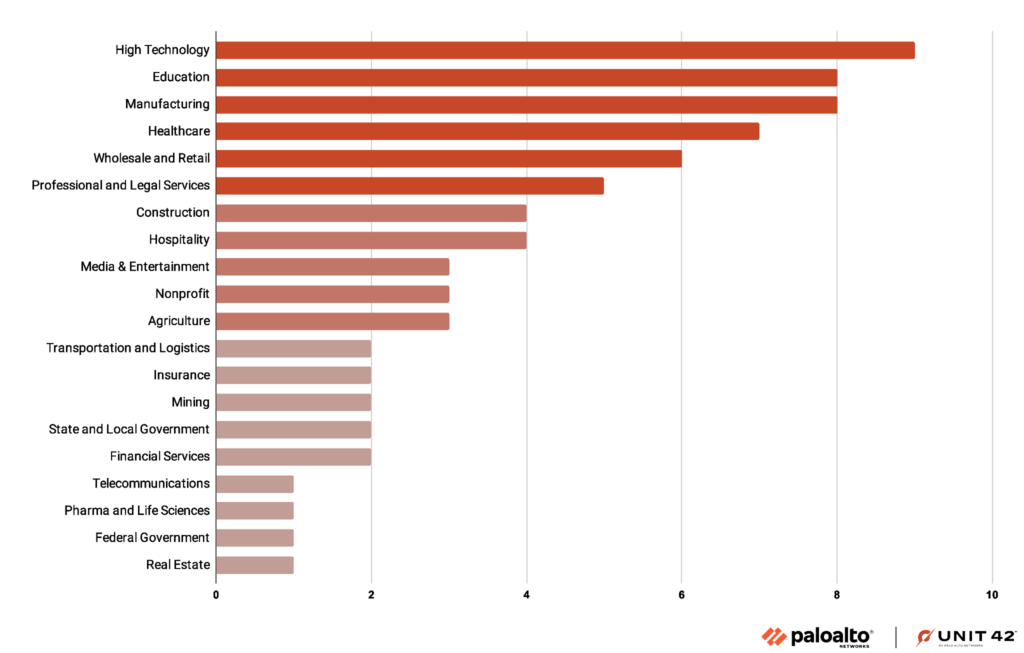
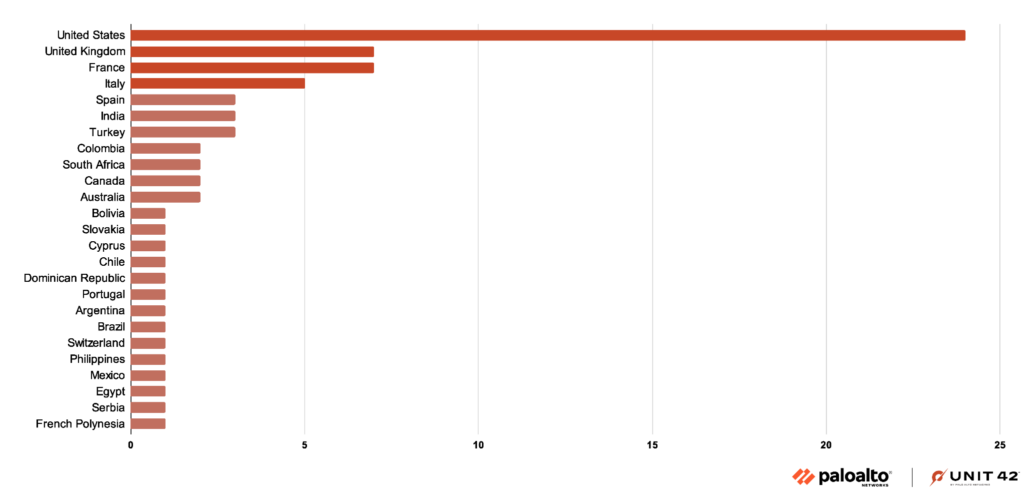
Unit42 has conducted a census of Medusa victims divided by industry and country. Healthcare is in 4th place and Italy occupies the same position in the leaderboard of nations.
The malware used by the RaaS (MedusaLocker) is complex, sophisticated, and functional due to various techniques used to evade defenses and navigate within the internal networks of victims.
Among the initial access techniques, the group utilizes previously compromised Windows IIS servers that allow, through the Windows bitsadmin utility, the download of a ZIP file containing the ConnectWise software used for remote access by the attackers. Variants of the downloaded file exist, and there are also alternatives to IIS servers such as Microsoft Exchange Server. Threat actors seem to prefer using Microsoft software to bypass monitoring processes by camouflaging malicious traffic as legitimate.
The Safeengine Shielden software appears to be the standard within malware variants, used to release kernel-level drivers for various security products. Through the software, it is possible to obfuscate and protect the entry point of the drivers that are loaded by their loader.
The role of the drivers is to terminate processes from an hardcoded list thorugh the use of IOCTL codes 0x222094 and 0x222184.
Additionally, before executing the attack code, the binary restarts the machine in Safe Mode, preventing the execution of security tools that do not run in this startup mode.
To obtain privileges as NT AUTHORITY\SYSTEM, a CMSTP UAC bypass is performed, a common method used by other malware, not just ransomware.
To infect other hosts on the network, the malware employs various methods depending on the variant used, ranging from simple PowerShell scripts to the injection of web shells. In some samples, a portable version of NetScan and PsExec has been identified. This combination allows for the expansion of NetScan’s features, enabling customized configurations that can be executed directly by the ransomware operator.
Apart from these network propagation techniques, MedusaLocker shares many similarities with other ransomware variants. It employs common ransomware functionalities such as string decryption, file encryption, shadow copy deletion, and the creation of ransom notes. The extensive list of file extensions suggests a significant number of variants, enabling high adaptability to the environment in which the malware is executed.
MEDUSA appears to be actively establishing a strong reputation and expanding its reach. In addition to the Data Leak Site (DLS), they have established a Telegram channel within the past year. This channel is used to release samples or entire sections of stolen files. MEDUSA is increasingly targeting the healthcare sector, posing a significant threat to these critical services. The sensitivity of patient data and the potential disruption of operations make healthcare organizations prime targets for ransomware attacks. MEDUSA’s core malware is highly sophisticated, enabling its affiliates to cause widespread damage using custom tools provided to them. This combination of a sophisticated core and custom tools makes MEDUSA a particularly dangerous threat. The existence of multiple MEDUSA variants increases the malware’s threat even in networks monitored by security teams (blue teams). The diversity of these variants makes it difficult for defenders to develop universal detection and mitigation strategies.
While MEDUSA’s attacks are currently concentrated in the US, organizations in other countries, particularly Italy, should not underestimate the group’s potential interest in their assets.
We recommend visiting CISA’s MEDUSA related page [1] which provides updated IOCs including IP addresses and email addresses used for phishing and initial access. Also, a high number of hashes files were published in a Cisco Talos research.
We also call for monitoring the movements of the group that besides becoming more aggressive has no code of ethics, any company or institution can be a victim of MEDUSA. Monitoring should also be done on data leaks being that RaaS is increasingly using credential brokers to infiltrate targeted networks.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.