
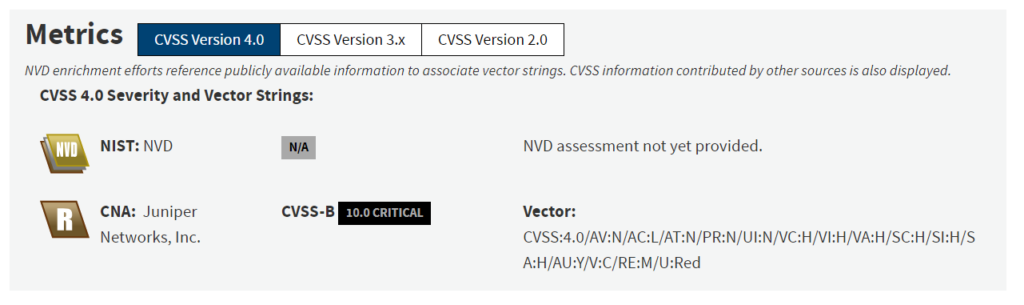
Juniper Networks has recently announced the release of out-of-band security updates to address a severe vulnerability that could lead to an authentication bypass in some of its routers. This vulnerability, identified as CVE-2024-2973, has received a CVSS score of 10.0, indicating the highest possible severity.
According to Juniper Networks, the vulnerability involves an authentication bypass using an alternate path or channel in Session Smart routers or conductors that operate with a redundant peer. This issue allows a network-based attacker to bypass authentication and take full control of the device. In an advisory issued last week, the company explained that the vulnerability affects only routers or conductors configured in high-availability redundant mode.
The security updates are intended for the following devices:
Juniper Networks, acquired by Hewlett Packard Enterprise (HPE) for approximately $14 billion earlier this year, stated that they have found no evidence of active exploitation of the vulnerability in the wild. The vulnerability was discovered during internal product testing, and there are no workarounds that can resolve the issue definitively.
In a further statement, Juniper Networks reassured users that the vulnerability has been automatically patched on affected devices for MIST-managed WAN Assurance routers connected to the Mist Cloud. The company emphasized that the fix, applied automatically on routers managed by a Conductor or on WAN Assurance routers, has no impact on the router’s data-plane functions, ensuring that network operations remain unaffected and secure.
Juniper Networks’ commitment to the security of its products and its swift response to the discovery of this vulnerability highlight the importance of keeping network devices updated. Users are encouraged to check the versions of their devices and ensure that security updates are applied promptly to protect their networks from potential threats.
For further details and to access security updates, please visit the official Juniper Networks website.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
