
Recentemente, un attore di minacce cibernetiche, conosciuto come EagleStrike, ha pubblicato un annuncio su un forum nel dark web, dichiarando di essere in possesso di dati riservati riguardanti l’Aeronautica Israeliana (IAF). Secondo il post, questa raccolta di informazioni comprende dettagli critici sia per i piloti attivi che per quelli inattivi, oltre che per vari dipendenti dell’aeronautica.
Al momento, non possiamo confermare la veridicità della notizia, poiché l’organizzazione non ha ancora rilasciato alcun comunicato stampa ufficiale sul proprio sito web riguardo l’incidente. Pertanto, questo articolo deve essere considerato come ‘fonte di intelligence’.
L’attore di minaccia afferma che i dati raccolti contengono una varietà di informazioni personali e professionali, tra cui:
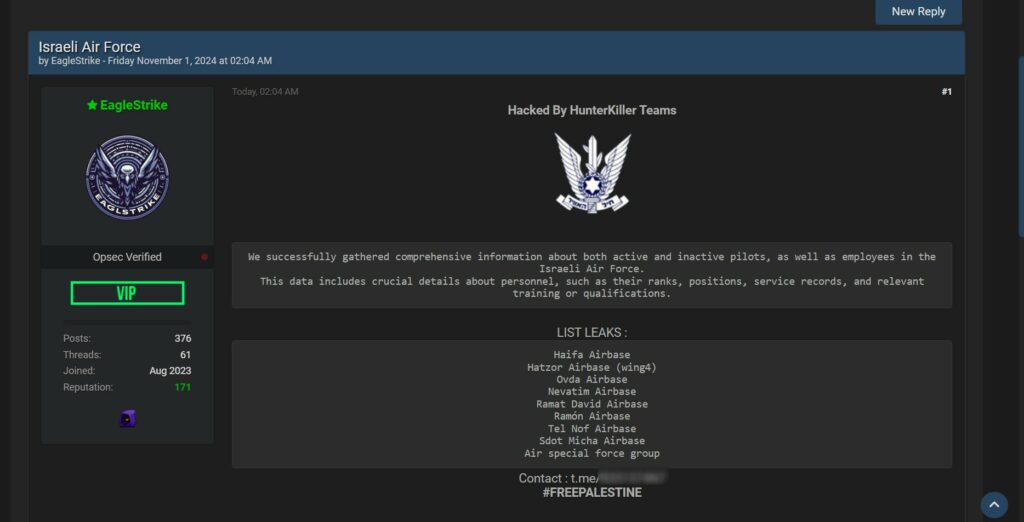
Questa informazione dettagliata potrebbe rappresentare un rischio significativo per la sicurezza del personale coinvolto e per l’integrità operativa dell’aeronautica.
Attualmente, non siamo in grado di confermare con precisione l’accuratezza delle informazioni riportate, poiché non è stato rilasciato alcun comunicato stampa ufficiale sul sito web riguardante l’incidente.
Il presunto leak riguarderebbe dati provenienti da diverse basi aeree israeliane, tra cui:
La menzione delle basi sopra indicate suggerisce che i dati possano includere dettagli operativi significativi, dato che molte di queste basi ospitano personale specializzato e risorse militari avanzate.
La vendita di tali informazioni può rappresentare una minaccia non solo per l’Aeronautica Israeliana ma anche per la sicurezza nazionale di Israele. Qualora i dati fossero effettivamente autentici, potrebbero essere utilizzati per operazioni di spionaggio, sorveglianza mirata o persino per coordinare attacchi informatici. Le informazioni sui gradi, le posizioni e i dettagli di addestramento possono fornire agli avversari un quadro completo delle capacità e della struttura dell’IAF.
L’attore di minacce, sotto il nome di HunterKiller Teams, ha accompagnato il post con slogan a favore della causa palestinese, suggerendo un possibile movente ideologico dietro questa presunta vendita di dati. Tuttavia, in contesti di cybercrime, moventi politici e interessi economici spesso si intrecciano, rendendo difficile determinare se lo scopo primario sia la diffusione ideologica o il profitto economico.
Questa situazione mette in evidenza la crescente vulnerabilità delle infrastrutture militari e delle informazioni riservate in un’era di minacce cibernetiche avanzate. La presunta vendita dei dati dell’Aeronautica Israeliana è un altro esempio dell’importanza della cybersecurity per proteggere le informazioni sensibili delle forze armate e delle istituzioni statali.
Israele e altre nazioni devono considerare misure rafforzate di protezione e controllo delle informazioni per contrastare tali minacce, che continuano a evolversi e a diventare sempre più sofisticate.
Come nostra consuetudine, lasciamo sempre spazio ad una dichiarazione da parte dell’azienda qualora voglia darci degli aggiornamenti sulla vicenda. Saremo lieti di pubblicare tali informazioni con uno specifico articolo dando risalto alla questione.
RHC monitorerà l’evoluzione della vicenda in modo da pubblicare ulteriori news sul blog, qualora ci fossero novità sostanziali. Qualora ci siano persone informate sui fatti che volessero fornire informazioni in modo anonimo possono utilizzare la mail crittografata del whistleblower.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…