
Modern Intel processors, including Raptor Lake and Alder Lake CPUs (i.e., 12th and 13th generation Intel “Core” processors), are vulnerable to a new high-precision Branch Target Injection (BTI) attack called “Indirector.” Discovered by security researchers Luyi Li, Hosein Yavarzadeh, and Dean Tullsen of the University of California, San Diego (UCSD), Indirector exploits vulnerabilities within the Indirect Branch Predictor (IBP) and Branch Target Buffer (BTB).
These two critical components in Intel CPUs could be abused to hijack execution and leak sensitive data. This attack represents a significant security threat, bypassing existing protection mechanisms. Full details will be disclosed at the upcoming USENIX Security Symposium in August 2024.
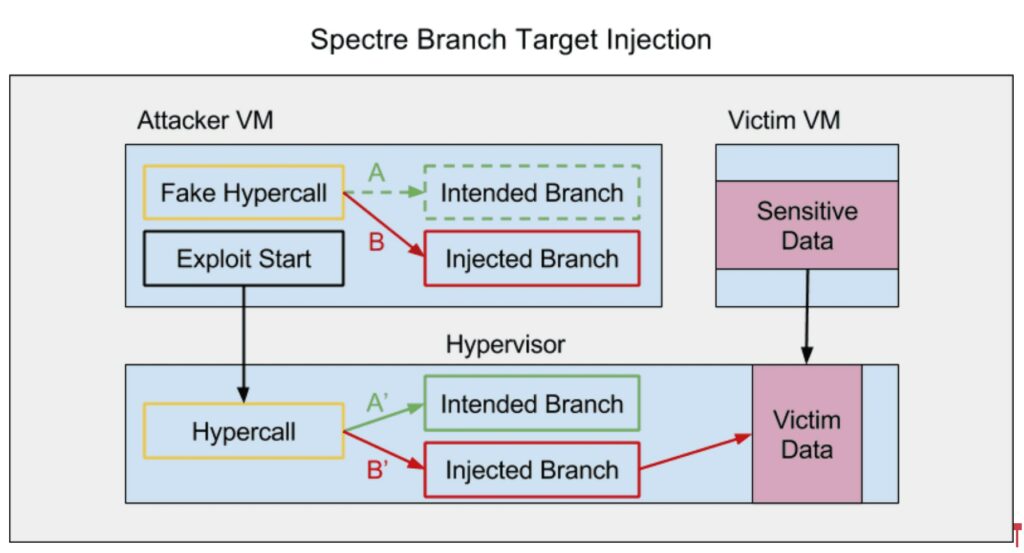
BTI (Branch Target Injection) attacks exploit characteristics of modern CPUs to manipulate the program’s control flow by relying solely on branch prediction functionalities. Branch prediction is a technique used by CPUs to anticipate the direction a program’s execution flow will take, thereby improving efficiency.
When the CPU encounters a branching instruction (like an IF statement), it needs to predict which path to follow before knowing the final outcome of the condition. To avoid wasting cycles while waiting for the actual outcome, the CPU predicts the results of branching instructions and speculatively executes instructions along the predicted path.
Components of Branch Prediction:
BTI attacks exploit branch prediction, an optimization technique where the CPU predicts the most likely path a program will take, to execute speculative code. Similar attacks like Spectre and Meltdown exploited this type of speculative code execution to gain unauthorized access to sensitive data. BTI vulnerabilities highlight the critical role of secure branch prediction in modern CPU design. By manipulating these interactions, attackers can bypass existing security measures.
Even defenses like Indirect Branch Predictor Barriers (IBPBs) and other mitigations cannot completely stop new attack vectors that exploit CPU vulnerabilities.
The new Indirector attack exploits weaknesses in the IBP’s design to launch targeted attacks, bypassing existing protections. The key mechanisms it utilizes include:
Modern CPU, like Raptor and Alder Lake, have been proved to be vulnerable on this BTI attack. This suggests that the discovered exploit could be leveraged to leak protected information from processors even after the mitigations for Spectre and Meltdown.
To mitigate these attacks, it is possible to employ barriers like the Indirect Branch Predictor Barrier (IBPB) and strengthen the Branch Prediction Unit (BPU) design with more complex tags, encryption, and randomization.
The Indirect Branch Predictor Barrier (IBPB) is a security measure that invalidates indirect branch predictions during context switches, such as transitions between users. In Linux, IBPB is automatically activated during transitions to SECCOMP mode (a sandboxing mechanism) or during kernel activities with limited indirect branches. However, frequent use of IBPB can cause a performance drop of up to 50%, making it challenging to implement aggressively in performance-critical environments like browsers or sandboxes.
To further mitigate attacks, the design of the BPU should be improved. Intel has already introduced fields such as Core-ID and Privilege Level into the design of their Indirect Branch Predictor (IBP) to prevent aliasing between indirect branches executed on different cores or at different privilege levels. Nevertheless, researchers propose integrating more complex tags, encryption, and randomization into future BPU designs to provide finer-grained isolation between different security domains, thus reducing the attack surface.
BTI attacks like Indirector demonstrate the continuous evolution of attack techniques against modern CPUs. Despite the implemented security measures, the complexity and sophistication of modern CPUs still offer attack vectors that require further research and improvements in hardware and software defenses. Side-channel vulnerabilities can become persistent threats if not properly patched and studied, leaving room for a high number of targets vulnerable to attackers.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
