
I became aware of this technique like 9 months ago, and now I see this on a attack in the wild conducted by Qilin Ransomware Gang, so it’s time to make it public.
One of the most important security things in EDR’s is the possibility to intercept calls to the kernel. For this purpose, EDR’s vendors use MiniFilter Drivers that load on boot. But what happens when these drivers are forced disabled by attacker? The attacker can peacefully make kernel calls without being intercepted by EDR’s.
When the Windows load a MiniFilter Driver , there is a order to load them , this order is specified with a parameter that Microsoft give to MiniFilter Drivers, this is called Altitude, we can learn about that on this Microsoft page.
This technique is simple and highly effective. Now let’s see how this attack works and how to stop it.
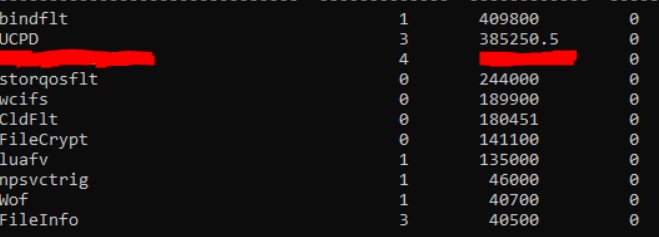
In this screenshot we can see that we have several MiniFilter drivers that are loaded in our system and one of them is the EDR’s ones. The third column are the Altitude of driver. What happens if we modify the Altitude of these drivers, like FileInfo to the EDR’s one’s? For do this we can modify a registry
REG_MULTI_SZ key.
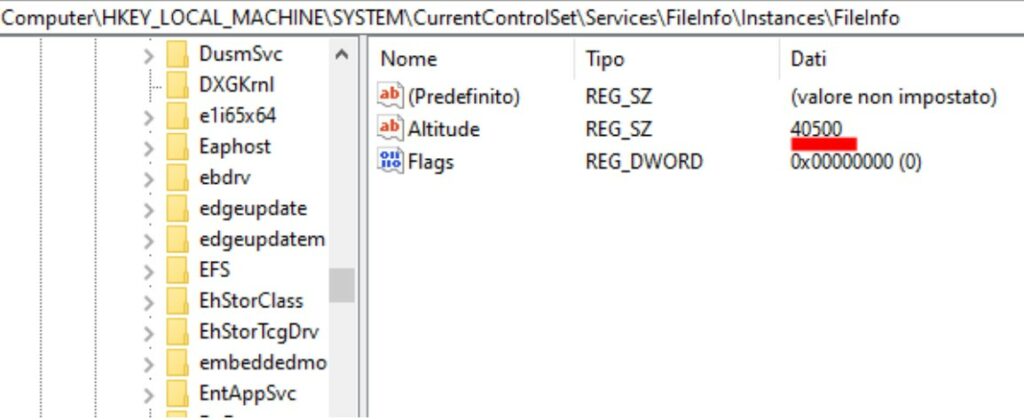
We go to modify this specific key with Altitude from EDR’s MultiFilter Driver. To make the change effective we need to reboot the endpoint. Now we can verify that our change is effective.
We can see that now the FileInfo has the Altitude of the EDR’s MiniFilter driver.
We can see also the EDR’s MiniFilter that before was loaded now is not loaded because of our change.
With this registry modification we can interact with Kernel Callbacks for example without being flagged
by EDR’s.
I have done this test with 6 EDR’s in these past months and NO ONE of them flagged the registry modification as malicious. Now, how we can monitor this? Is simple, we can monitor the modification of any MiniFilter Altitude in the registry and flag this as malicious. With this technique, the Threat Actor
(Qilin Ransomware) that I saw on a recent attack in the wild, run LaZagne without being flagged by EDR.
I hope the EDR’s vendors can add this telemetry to their products so the technique can be useless.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.