
Recently, the landscape of cyber threats has been enriched by the emergence of a new ransomware group named “Ransomcortex”. This group is distinguished by its specialization in attacking healthcare facilities, having already collected four victims within a few days of its first appearance. Among these, three are Brazilian healthcare facilities and one is Canadian.
The preference for attacks on the healthcare sector is not new, but Ransomcortex represents a significant evolution of this trend.
The interest of cybercriminals in healthcare organizations dates back several years, but recently there has been a significant increase in these attacks. One of the first notable cases was in 2016, when the Hollywood Presbyterian Medical Center in Los Angeles was hit by a ransomware attack that blocked the hospital’s IT system, demanding a ransom of $17,000 in bitcoin to restore access to critical patient files.
This incident raised alarms about the vulnerability of healthcare organizations to cyber attacks and highlighted the need to strengthen cybersecurity measures in the healthcare sector.
In the following years, cyber attacks against healthcare organizations became increasingly sophisticated and widespread, with a wide variety of threats including ransomware, phishing, data breaches, and targeted attacks.
In 2020, during the COVID-19 pandemic, cyber attacks against healthcare facilities further increased. We recall the attack on Vastaamo, a private Finnish psychotherapy clinic founded in 2008. On October 21, 2020, Vastaamo announced that its patient database had been stolen. The cybercriminals demanded 40 bitcoins, about 450,000 euros at the time, threatening to publish the stolen data. The company eventually went bankrupt.
Also in 2020, we remember the attack on the Düsseldorf hospital, which led to the death of a 78-year-old woman suffering from an aortic aneurysm. What began as a routine call took a turn for the worse when they contacted the local university hospital to inform the staff of their imminent arrival, discovering it was paralyzed by a ransomware attack.
Subsequently, criminal cyber gangs split into two factions: those who explicitly declared they would not target hospitals and healthcare companies and pediatric clinics, and those who had no intention of setting rules, such as the Black Basta cyber gang.
Another famous case involves the ransomware group LockBit, which after an attack on a healthcare facility, formally apologized for the attack on the SickKids hospital, stating that one of its members violated the rules by attacking the healthcare organization and, therefore, released a free decryptor for the hospital.
Unlike other ransomware groups, Ransomcortex has chosen to focus its attacks exclusively on healthcare facilities. This targeted focus raises questions about what criminals gain if companies do not pay ransoms. The answer lies in the nature of healthcare data, which can be used for a wide range of fraudulent activities:
Ransomcortex’s data leak site provides further details about their operations and intentions.
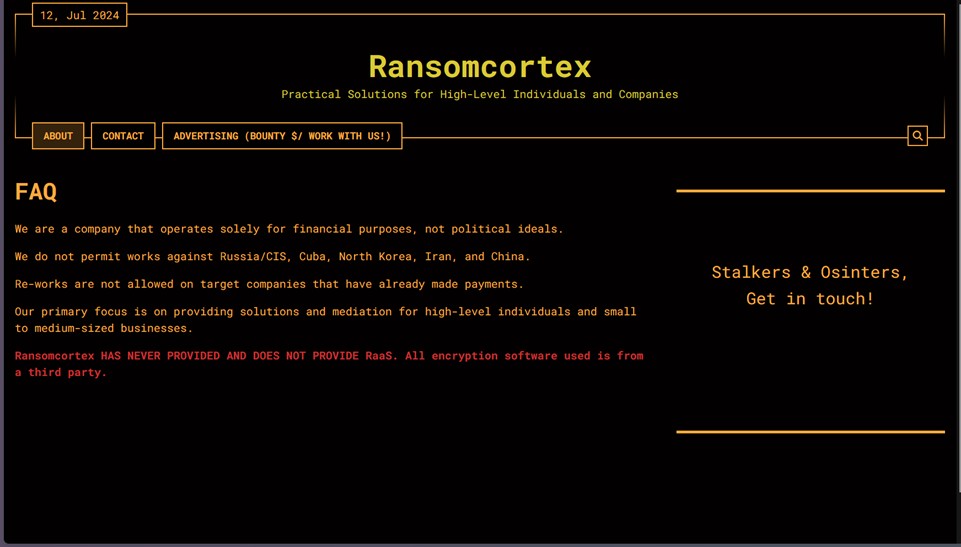
Ransomcortex represents a new and dangerous threat to the healthcare sector. Their specialization and exclusive focus on healthcare facilities, combined with the sophistication of their operations, require an urgent response from healthcare organizations and competent authorities. It is essential to implement advanced security measures and remain vigilant to protect sensitive data and ensure the continuity of healthcare operations.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
