
In the last month of 2024, LockBit has been exodusively talked about. The prominent news is the long-awaited release of the 4.0 program of the most famous RaaS in the scene. After the entire Operation Cronos series, which does not seem to be over yet, LockBit has been put to the test with an unprecedented digital crime-fighting experience executed by an international task force.
In this article we will expand on the very latest updates trying to take stock and comment on these early (partial) conclusions of a real attrition that will impact the future of digital security and crime.
For those who would like to get the full context and delve into the timeline in question find listed, in chronological order the major phases of Lockbit vs. Operation Cronos:
November 29, 2024, Kaliningrad, Russia. Local law enforcement announced the arrest of “Wazawaka” described as a central figure in the development of as many as 3 ransomware groups : Conti, Babuk and, of course, LockBit. Behind the nickname was Mikhail Pavlovich Matveev, 32-year-old Russian to whom a $10 MLN bounty had already been issued through the FBI’s Reward For Justice program.

According to the charges thanks to Mikhail‘s contribution they would have made (in total) $200 MLN for the 3 groups, the investigation allegedly began in January 2024 and at the time of his arrest he was still active within LockBit.
The fact that Russian authorities arrested a ransomware developer who had stated in his posts, on underground forums, not to attack ex-CIS nations goes against the typical unwritten rule about not receiving interest from local authorities as long as they are harmless to the latter. It is still unclear why this arrest was made, and opaque Russian legal procedures do not help in obtaining further information, among the various speculations is the interest on obtaining Wazawaka’s earnings.
The administrator of the Telegram channel Club 1337 made direct contact with Mikhail, who confirmed that he is charged under Russian Article 273 (Computer Information as a Crime), to be released pending sentencing and the confiscation of a “significant” portion of his cryptocurrencies estimated to amount to a few million dollars.
Other members of LockBit had been arrested before but they were either affiliates or responsible for money laundering. Mikhail is the first central component of the group to be arrested, the list of wanted persons (by the US) related to LockBit are as follows:
If with Mikhail we cannot get information regarding his arrest and serious interrogation with Rostislav Panev things get decidedly more interesting. 51-year-old Haifa (Israel) resident arrested on August 18, 2024 under U.S. request with extradition confirmation in December 12, 2024 is believed to be another central developer for LockBit and to be in direct contact with LockBitSupp.

News of his arrest was only recently made public with initial statements on the charges. Investigators traced Panev‘s early activities in the group’s early days in 2019 to his arrest in 2024; his role was the development of builders used by affiliates to generate executable versions of the ransomware. One of his contributions was the feature that allowed the malware to print out hardcopy versions of the group’s ransom note.
Forensic investigations on the devices following the arrest revealed a direct connection between Panev and Dmitry Khoroshev using the moniker LockBitSupp in which they discussed the advancement of malwares and affiliate control panel. His work was paid for with regular payment that would amount to about $230,000 over these 5 years of activity.
Finally, credentials were found for access to the code repository of several LockBit builders, the exfiltration tool called StealBit, and also access to the group’s administrative panel.
A legal battle is currently underway between Panev’s lawyer, Sharon Nahari, and the Israeli government, who, according to the lawyer, have made untrue allegations regarding money laundering, malware use and extortion, stressing that his client has limited himself to only developing tools for the group.
It is clear to all that Operation Cronos, after gaining access to the backend, tested the OPSEC of all members and affiliates proving that with the right approach it is possible to trace the identity of anonymous actors. Now that Panev will be extradited to the U.S. combined with all the information collected from his devices will play a crucial role in future operations.
Extradition is scheduled for January 15, 2025.
LockBitSupp has always been marked by a strong dose of arrogance accompanied by provocations to law enforcement agencies (specifically the FBI and NCA) showing itself immune to attacks by the latter. After the election of Donald Trump (to which LBSupp has never hidden its appreciation) the status of the TOX profile was changed to this:
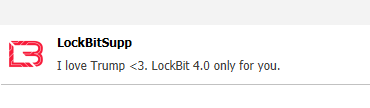
Leaving aside political preference, this is not the first time LB has explicitly mentioned a new version of their operations. Until now there were only discussions about it, but as of November 6, 2024, it seems to be official without any further information about it, however.
Panev’s arrest may have been one of the causes that led to the slowdown in the release of the 4.0 program and also, LockBit had experienced technical problems that led the group to publish a statement on how to contact the group going straight to the point without getting lost in too many turns of phrase. With a good deal of confidence we can conclude that Panev‘s arrest created no small amount of damage, and this would explain why they did not want to make his arrest public directly in August.
At the beginning of December 2024 the status was changed to “17 декабря” (December 17), we could expect an official announcement of the new program but surprisingly LockBit presents a new opportunity to provoke its detractors.
A statement was released with a protected zip file intended for Christopher Wray, director of the FBI. Below is the statement translated from Russian:
Friends, today is a great day: it’s the FBI director’s birthday!
Dear Christopher Asher Ray. On this beautiful day, I would like to wish you a happy birthday from the bottom of my heart and wish you all the best. May your life always be beautiful and full of good moments, like the one when you caught me or at least recognized my identity. May your memories be only bright and good, like when you were tricked by your staff and told that they had found me. May you only be surrounded by people who help you climb even higher, but where to go even higher? May your work be easy and favored, and may your salary be as high and desirable as mine. May your eyes always shine as brightly as they do now, may your money never run out, and may all your dreams come true as quickly as you wish. Accept this archive as a gift. Please do not download this archive under any circumstances, it is an archive only for the Director of the FBI. Again, happy birthday!
Ironically, Christopher Wray announced his retirement on December 16, 2024. This provocation will come in handy in the concluding section of the article.
To end the year LB has finally published the first affiliate enrollment links of the new RaaS program. As already analyzed by Sandro Sana besides the payment of $777 in XMR or BTC there are no further requirements. For now this is all that is known besides the official release date set for February 3, 2025.
RaaS despite all that is happening to them does not seem to want to stop, we would like to remind ourselves of the concept expressed in the first public statement after Operation Cronos where LBSupp stated that it is no longer about money but about getting as many victims as possible on his DLS as a challenge against the FBI.
The latest update on this conflicting loop comes from a LinkedIn post by FBI Cyber Operations Crime Director Brett Leatherman that quotes Wray’s words:
“No matter how hidden or advanced the threat, the FBI remains committed to working with our interagency partners to safeguard the cyber ecosystem and hold accountable those who are responsible for these criminal activities.”
Director Wray
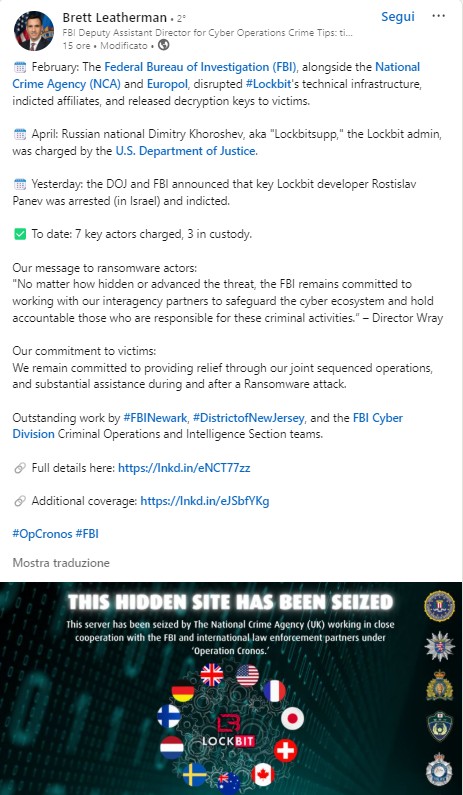
It seems clear the commitment made and the willingness in continuing Operation Cronos by the FBI combined with the entire task force set up to suppress LockBit. The humiliation brought by the seizure of part of the DLS and StealBit servers accompanied by LBSupp’s request to cooperate if law enforcement published the ALPHV/BLACKCAT deanon put the RaaS in a very bad light.
Behind all the technicalities and arrests is blatant a strong PsyOPS (Psychological Operation) showing themselves to be firm and sturdy in the face of those who (claim) to be equally so. A 3D chess game where the two sides more or less explicitly communicate their intentions. Whatever the conclusion, 2025 promises to be a pivotal year for this standoff but we can reflect on the whole Cronos event achieved in 2024.
For now, we cannot predict what the LockBit 4.0 program really is or even what the group’s goals, capabilities and endgame really are, but it is certainly setting a precedent in digital crime that will set a new standard for future threats.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.