
After the European elections unfolded, geopolitical attentions shifted to the U.S. election campaign, one of the most dynamic in recent years recently with the Democrats’ recent changeover with Harris as the new nominee. There has been no shortage of controversy : Elon Musk has taken a sharp stance by releasing AI videos against candidate Harris, record fundraising for the Democrats’ campaign, and Trump injured by a gunshot during a rally.
The latter has also been a major player within digital crime circles, some of the readers will recall the (alleged) attack in Fulton County by LockBit. LockBitSupp claimed to be in possession of documents that would “jeopardize” this November’s election. Again according to the evil CEO this would have been the casus belli of Operation Cronos, after the countdown ended the DLS post disappeared without any leaked documents leaving strong doubts about LB’s public statements.
Once again the Republican candidate finds himself in the eye of the storm for another cyber attack revealed by POLITICO that allegedly led to the exfiltration of some internal communications.
The news was published by POLITICO, which allegedly received anonymous emails containing files regarding Trump’s internal administration since July 22, 2024 signed by “Robert”. The administration, on Saturday, August 10, 2024, officially stated that it was the victim of the attack with a direct statement from Republican campaign spokesman Cheung :
“These documents were illegally obtained from foreign sources hostile to the United States, intended to interfere with the 2024 election and sow chaos throughout our Democratic process. On Friday, a new report from Microsoft found that Iranian hackers broke into the account of a ‘high ranking official’ on the U.S. presidential campaign in June 2024, which coincides with the close timing of President Trump’s selection of a vice presidential nominee.”
“The Iranians know that President Trump will stop their reign of terror just like he did in his first four years in the White House.”
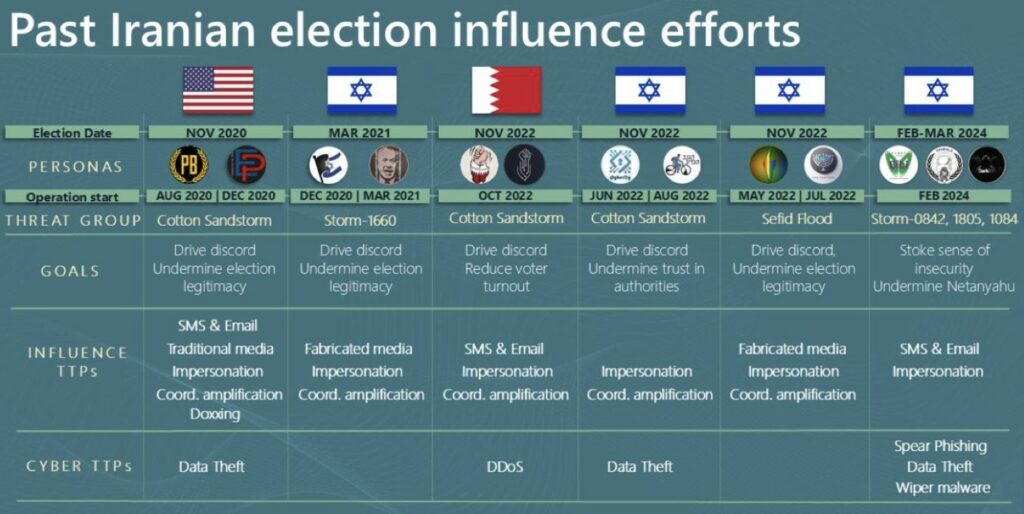
The aforementioned report was published on Friday, August 9, 2024 in which Microsoft decided to share information gathered (“sharing intelligence”) regarding Iranian actions aimed at compromising the November election within the cyber world. The said operations were divided into two distinct classes :
The full report contains not only information on Iranian groups but also Russian and Chinese groups assuming cooperation between these states. Focus is brought to Iran because of a peculiarity of theirs : while the other two nations tend to influence election results, the Middle Eastern state focuses on long-term projects, with different methodologies and greater aggressiveness.
POLITICO was careful to point out that the threat was not independently identified but relies on statements made by the Republican spokesman. Cheung declined to make explicit whether internal staff contacted law enforcement or Microsoft out of a desire not to “discuss these kinds of conversations”. POLITICO invited Microsoft to comment on the report and the (plausible) connection to the announcement of the attack that occurred a day later, the big tech declined but confirmed that it could not identify the political party victimized by the Iranian groups.
Clearly POLITICO did not publish the files it received, in case they were real their publication would fall under a federal crime since it is data obtained illegally without the administration’s consent. It has been said, however, that among the contents received are internal communications of a senior official and a file of Senator JD Vance, Donald J. Trump’s running mate. “Robert” labels past statements by Vance as “POTENTIAL VULNERABILITIES” and claims to be in possession of a similar document concerning Senator Marco Rubio along with a variety of legal and judicial documents concerning Trump and internal discussions within the campaign administration.
As for Microsoft’s report, it seems well structured and its contents are in line with other similar work concerning APT reports, digital espionage, and influences of political processes. It differs greatly from what was decided to publish : no IOC, no technical evidence and no clues that could reconstruct more clearly the spear phishing email sent. It sounds somewhat strange that the victim party of the Middle Eastern group is not known but the attack flow can be reconstructed and the compromised sender address belongs to another senior political official. Probably for the sake of integrity of intelligence operations, they limited themselves to the mere exposure of the results obtained but did not give the clues. The publication date of just one day before the POLITICO announcement is peculiar even though it may be a grotesque coincidence.
Cheung’s statements are strong, coincidental, and forceful. The certainty of the Iranians’ guilt expressed by the spokesperson assumes an unfolding of investigation since they learned of the breach, one may, however, consider it inappropriate not to state whether law enforcement has been in contact with Trump’s staff particularly when the democratic process of an entire nation is at stake.
All that remains is to wait for the facts to unfold and to expect a potential data leak totally different from the one promised by LB at the beginning of the year.
Cyber feuds between Iran and the U.S. are not something new, and no one should be surprised by the news disseminated by POLITICO, whatever the real facts of the events that are difficult to interpret for now. From stuxnet onward governments, states and politicians have understood how the use of the network can be the battleground of excellence on which to wage their battles. It is enigmatic territory but at the same time engaging for society as a whole. Through information technology we are witnessing historical movements such as wars, political polarizations, violence, protests, and geopolitical disagreements, but it is now clear that it is also the way in which these events are influenced and not just viewed.
The war in Ukraine and the situation in the Gaza Strip are no longer strictly kinetic operations but are the pivot to target the people who experience these events from the outside. There is an attempt to use them as a pretext to confuse and collide the indirectly involved nations about themselves. It is the biggest hack in history and we are all both the exploit, the vulnerability and the mitigation.
We have made a technology created to get rid of biases, unfortunately, into the key to creating new ones. America (Cambridge Analytica scandal), Russia (use of disinformation in foreign countries as a concept of information warfare), China (use of social media and bots for propaganda), Israel (Pallywood) and even Iran (fake Proud Boys emails) are just exploiting the lack of attention and easy susceptibility of different populations in states.
The direction of policies (both domestic and foreign) and communication methods are simply adapting to end users who do not want to change along with the world. The use of simple bots or AI-created content just mirror a simple but effective method for the way some individuals think, people who vote based on what they want to hear and not from what they actually see.
As mentioned above for the CrowdStrike case, now cybersecurity is no longer just about technical measures but is about the right interfacing with society, exploring the real risks and miancces that no longer just aim to trigger malware in a machine remotely but slowly advance to the Denial of Service of what we call freedom of information.
Exciting times in the world right now…Exciting times
Mr. Robot
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.