
Il 17 luglio 2024, l’utente Vadimblyaa ha pubblicato un post su un noto forum di cybercriminali, dichiarando di essere in possesso di informazioni personali di 6.000 dipendenti della NATO, acquisite attraverso una violazione dei dati avvenuta il 13 luglio 2024.
Vadimblyaa ha messo in vendita queste informazioni e invita gli interessati a fare offerte per il loro acquisto.
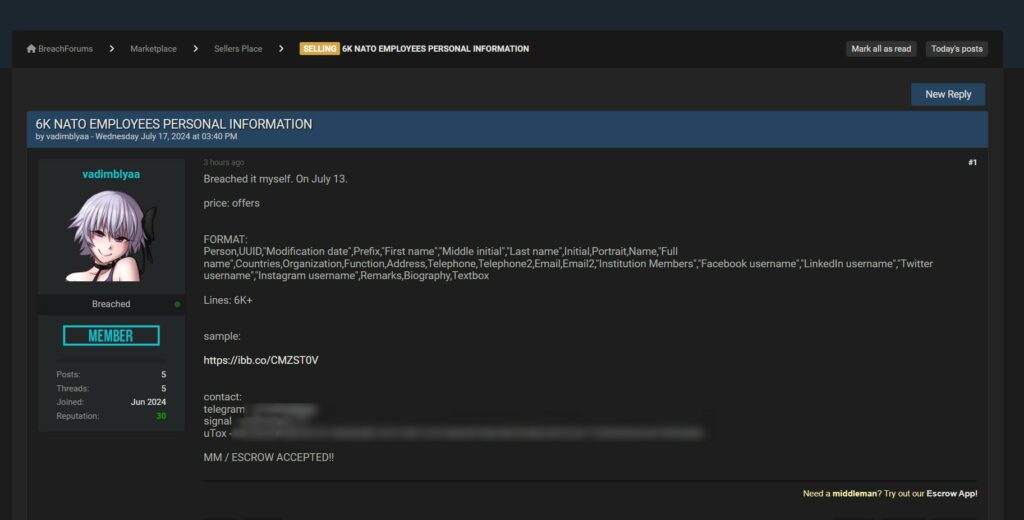
Vadimblyaa ha fornito dettagli specifici riguardo il formato e il contenuto dei dati compromessi, che includono:
Secondo quanto riportato, il file contiene oltre 6.000 linee di dati.
Al momento, non possiamo confermare con precisione la veridicità della violazione, poiché l’organizzazione NATO non ha ancora rilasciato alcun comunicato stampa ufficiale sul proprio sito web riguardo l’incidente. Pertanto, questo articolo dovrebbe essere considerato come una ‘fonte di intelligence’ piuttosto che una conferma definitiva della fuga di dati.
L’eventuale veridicità di questa violazione rappresenterebbe una seria minaccia alla sicurezza personale dei dipendenti NATO e potrebbe avere significative ripercussioni sulla sicurezza dell’organizzazione stessa. Le informazioni compromesse potrebbero essere utilizzate per vari scopi illeciti, tra cui il furto d’identità, attacchi di phishing mirati, o persino per facilitare attività di spionaggio.
Questo non è il primo caso in cui la NATO si trova ad affrontare minacce cibernetiche. Negli ultimi anni, diversi attacchi mirati hanno colpito le istituzioni militari e governative, evidenziando la necessità di potenziare continuamente le misure di sicurezza informatica.
Le istituzioni e i dipendenti devono rimanere vigili e adottare pratiche di sicurezza informatica robuste, come l’uso di autenticazione a più fattori, la sensibilizzazione sui rischi del phishing e il monitoraggio costante delle reti per individuare eventuali attività sospette.
Sebbene al momento non ci siano conferme ufficiali, la presunta violazione dei dati dei dipendenti NATO da parte di Vadimblyaa sottolinea ancora una volta l’importanza della sicurezza informatica e della protezione delle informazioni sensibili. È essenziale che le organizzazioni e gli individui siano costantemente aggiornati e preparati a fronteggiare le minacce in continua evoluzione nel panorama digitale.
Come nostra consuetudine, lasciamo sempre spazio ad una dichiarazione da parte dell’azienda qualora voglia darci degli aggiornamenti sulla vicenda. Saremo lieti di pubblicare tali informazioni con uno specifico articolo dando risalto alla questione.
RHC monitorerà l’evoluzione della vicenda in modo da pubblicare ulteriori news sul blog, qualora ci fossero novità sostanziali. Qualora ci siano persone informate sui fatti che volessero fornire informazioni in modo anonimo possono utilizzare la mail crittografata del whistleblower.
Nota: Questo articolo è basato su informazioni non confermate e dovrebbe essere considerato come una potenziale fonte di intelligence piuttosto che una verifica definitiva dell’accaduto.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…