
In teh last months Mac users have been targeted by a new wave of cyberattack trough malvertising campaigns. The last threat, called “Poseidon” by their creators, has been revealed this 24th June and exploits Google ADV to spread the infostealer. A recent MalwareBytes Lab’s report described this campaign as teh second attempt to use Arc browser as bait thanks to its growing popularity.
Poseidon is a MacOS malware in active development, designed to compete with Atomic Stealer (AMOS). This specific infostealer shares a good number of AMOS’s functionality like exfiltration methods, crypto wallet and password stealing from softwares like Bitwarden and KeePassXC. Initialilly identified as OSX.RodStealer by MalwareBytes has been renamed by its author Rodrigo4 and improvd with new capabilities like VPN configurations exfiltration.
Rodrigo4 creates a malware’s service which include a control panel with statistics and costum builder that permits to costumize icons, malware name and AppleScript. Poseidon offers a good range of advanced functionality that makes it a significative threat. In cybercrime forums Poseidon is described as a direct competitor of Atomic Stealer.
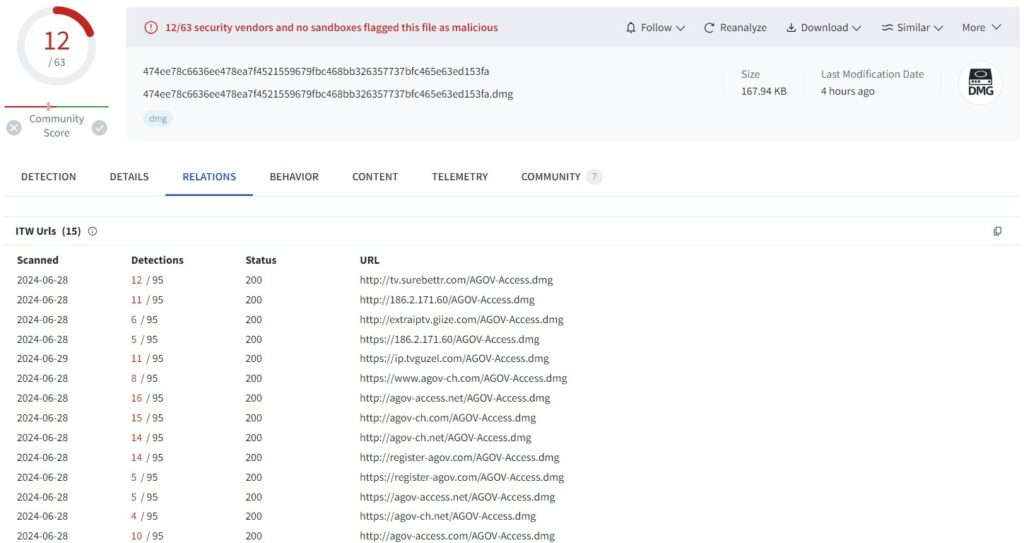
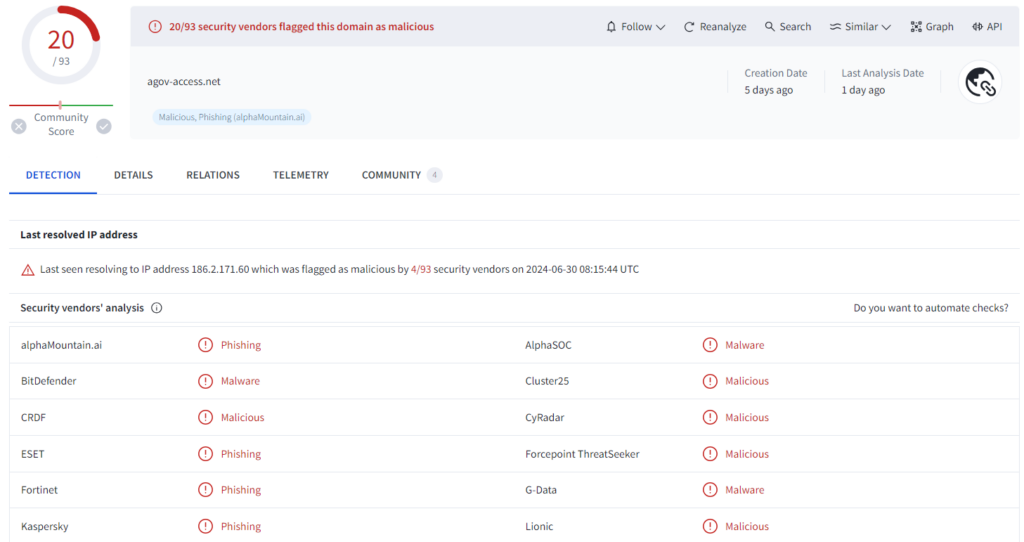
The malvertising campaign that spread the infostealer is made through Google ADV in order to redirect users to fake download sites (like arc-download[.]com). This websites mimic official Arc website.
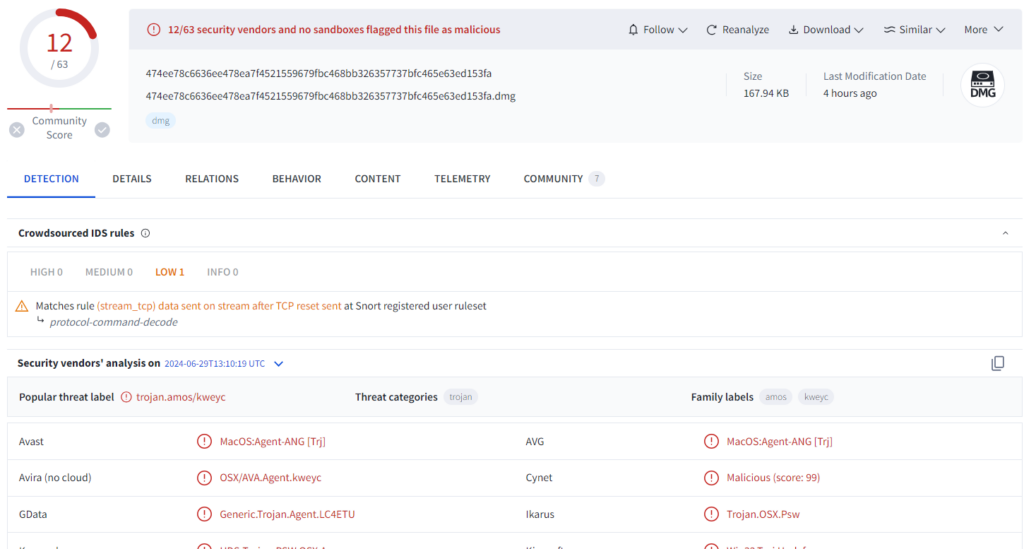
The users, fooled by legitimate appearance, download a malicious DMG that circumnavigate MacOS security measure requesting a single right-click to install rather than the traditional double-left click. Once installed, Poseidon start to capture and send sensitive data to a remote server, a known IP address is 79.137.192.4. This address host the control panel where exfiltrated data can be managed and used by criminals.

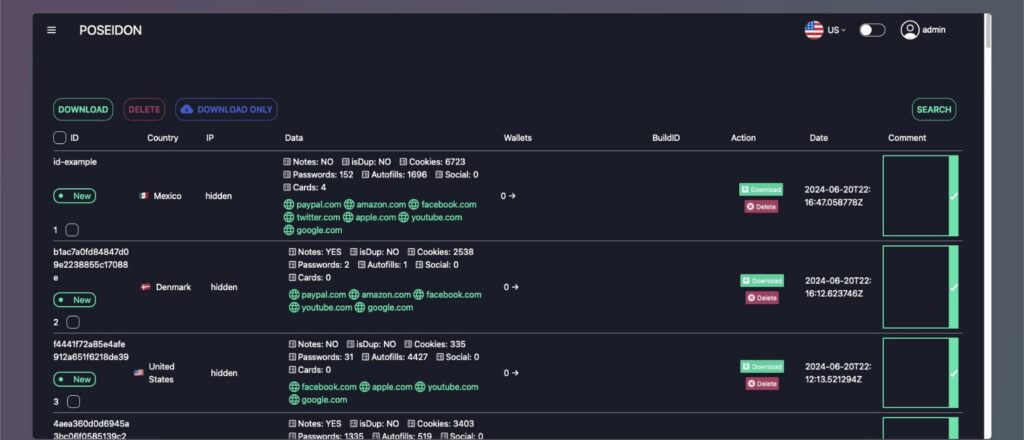
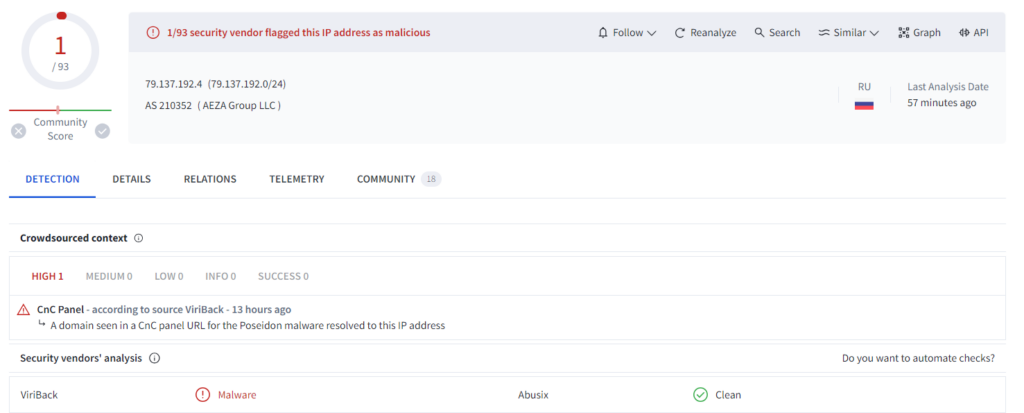
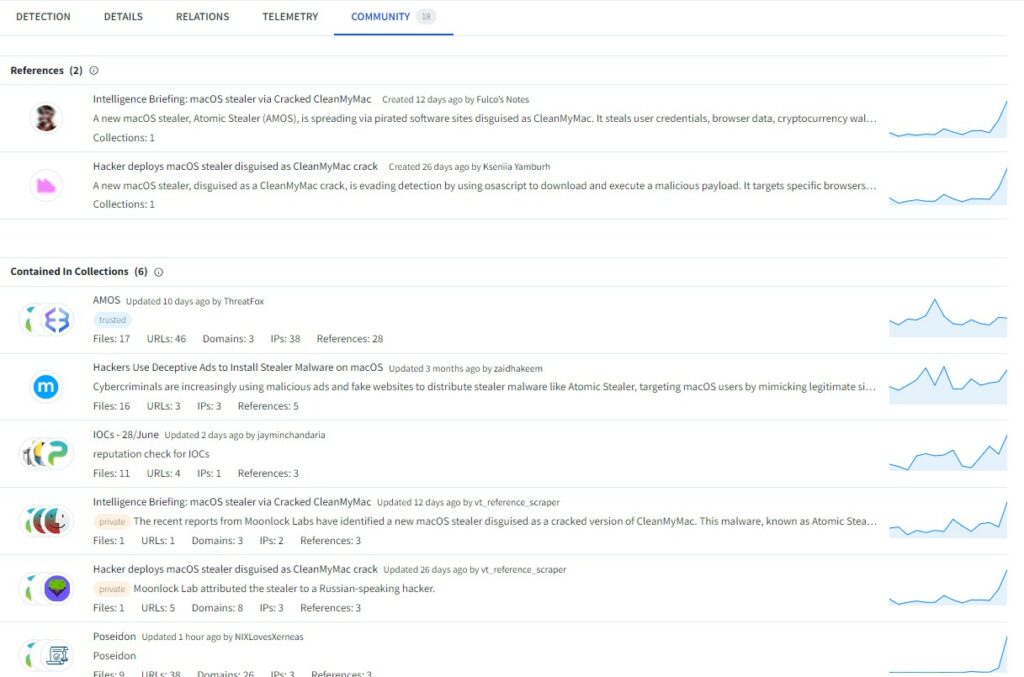
Poseidon breakthrough, subsequent to a similar campaign affecting a fake version of Arc for Windows OS, highlights a growing expertise by digital threats. This malware is well designed to steal as much data as possible and every Mac user should consider this as serious threat.
Recent developments showed that Poseidon is not the last threat for Apple ecosystem, a growing interest has been made by LockBit RaaS on Apple architectures, like M1 and M2. Professionals are worried about MacOS endpoints safety even if analyzed samples proved that threat are in development phase. MacOS malware are still incomplete (eg:/ Apple signing missing, basilar strings encryption) but this variants would permit to APT like LockBit to maintain their criminal market share highly competitive.
The current scenario shows how threats are diversifying their objectives, emphasizing crucial attention to adopt appropiate safety measures and be aware on every OS or device we are using.
This malware and its campaign demonstrates how cyber-criminals are exploiting new software’s popularity to spread their attacks on a wider range of users. Despite Google efforts on protect their ADV platform from malicious use, lawbreakers keep orchestrating fake websites successfully. MalwareBytes strongly suggests to use adblockers, advanced web protections and continously cautiousness when downloading new applications.
| 186.2.171.60 |
| agov-ch[.]com |
| agov-access[.]net |
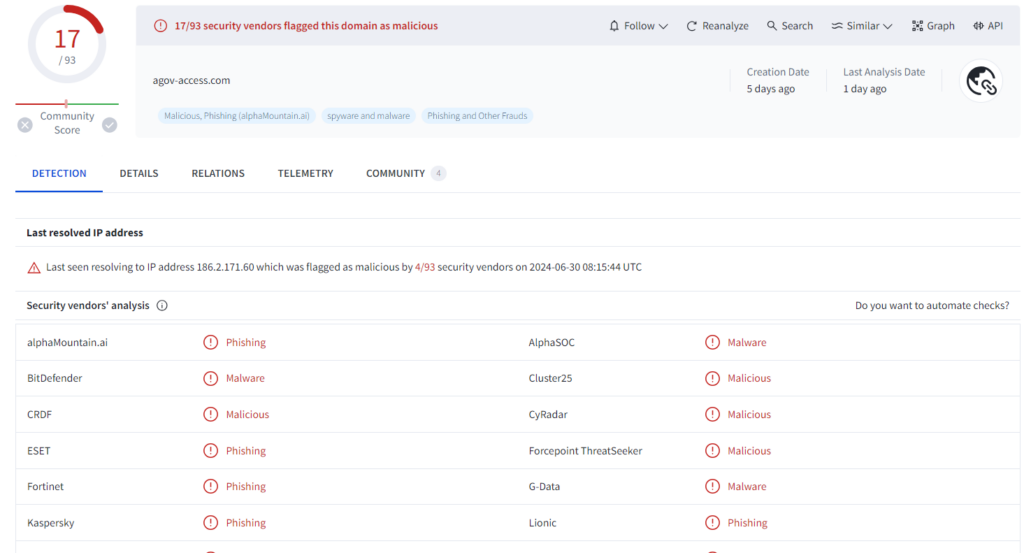
| agov-access[.]com |
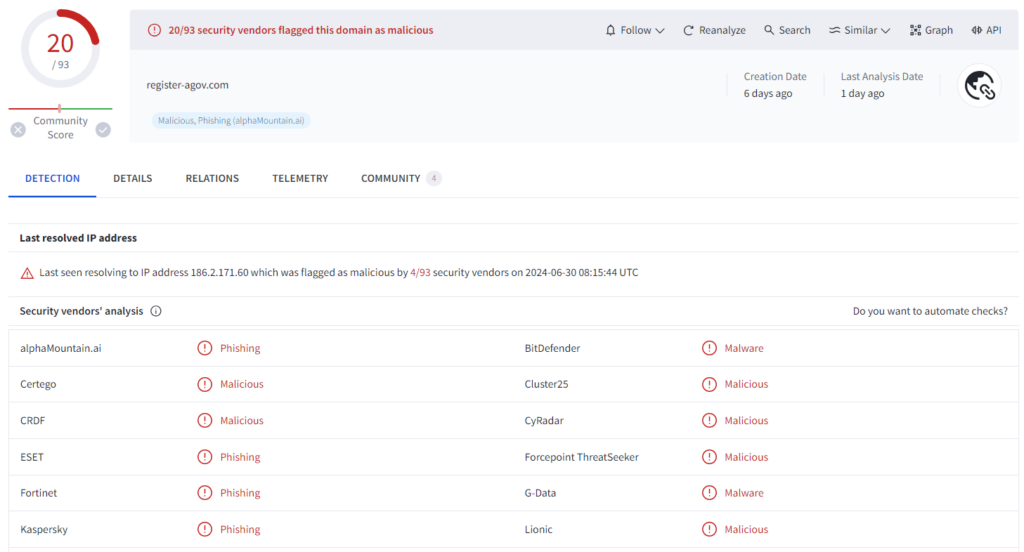
| register-agov[.]com |
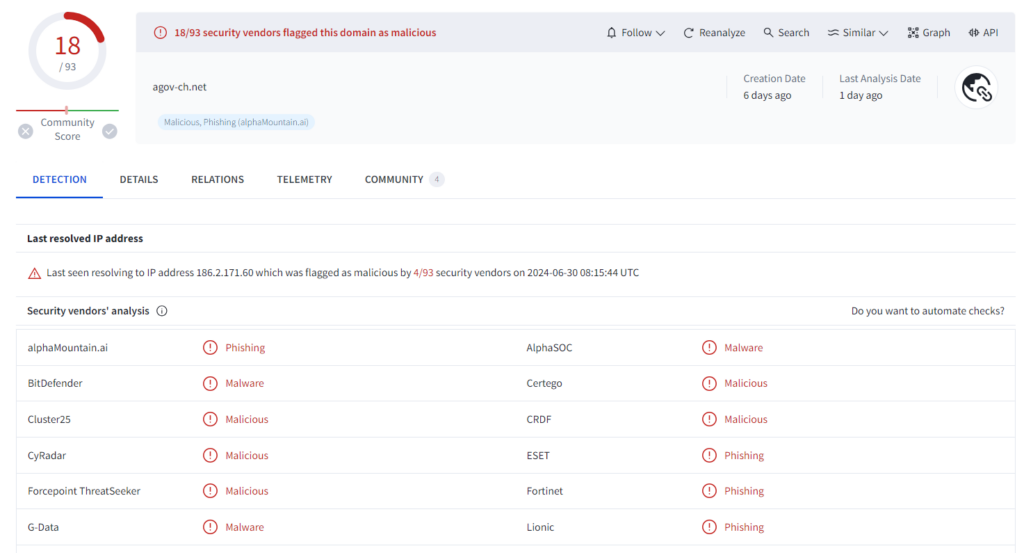
| agov-ch[.]net |
| bb8911f632a4547802a8dbb40268e1bd |
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
