
In the realm of cybersecurity, vulnerabilities constantly represent a significant risk for businesses and institutions. Many system administrators may recall CVE-2023-34362 from last year, a catastrophic vulnerability in Progress MOVEit Transfer that shook the industry, affecting high-profile victims like the BBC and the FBI.
Sensitive data was leaked and destroyed as the cl0p ransomware gang exploited zero-day vulnerabilities to steal data, leaving a trail of chaos. Today, a new threat emerges on the horizon: the CVE-2024-5806 vulnerability.
CVE-2023-34362 (https://nvd.nist.gov/vuln/detail/CVE-2023-34362) represents one of the most critical vulnerabilities that hit Progress MOVEit Transfer, a widely used software for secure file transfer. Discovered and disclosed in 2023, this vulnerability had a significant impact on several high-profile organizations, including the BBC and the FBI.
CVE-2023-34362 is classified as a “Remote Code Execution” (RCE) vulnerability. This type of vulnerability allows a remote attacker to execute arbitrary code on the target system without the need for authentication. Specifically, in the case of CVE-2023-34362, the flaw resided in inadequate handling of HTTP requests by the MOVEit Transfer software.
The vulnerability could be exploited by sending specially crafted HTTP requests to the MOVEit Transfer server. These malicious requests were able to bypass security controls and execute arbitrary commands with the privileges of the server execution process. This type of attack could be used to install malware, steal data, or further compromise the internal network of the organization.
The impact of CVE-2023-34362 was devastating. The vulnerability was exploited by the cl0p ransomware gang, which used this flaw to conduct large-scale attacks. The consequences of these attacks included:
Recently, a new vulnerability in Progress MOVEit Transfer has been identified, classified as CVE-2024-5806. This vulnerability has been labeled as an ‘Improper Authentication’ weakness, a problem that allows attackers to bypass authentication mechanisms and gain unauthorized access to sensitive data. This type of vulnerability is particularly concerning as it can be exploited to severely compromise data security. More details: https://nvd.nist.gov/vuln/detail/CVE-2024-5806
To further aggravate the situation, a Proof of Concept (POC) for exploiting CVE-2024-5806 has emerged. The availability of a POC means that attackers have a working example of how to exploit the vulnerability, increasing the risk of real attacks.
The POC can be used as a basis to develop more sophisticated and targeted attack tools, making the vulnerability an imminent threat.
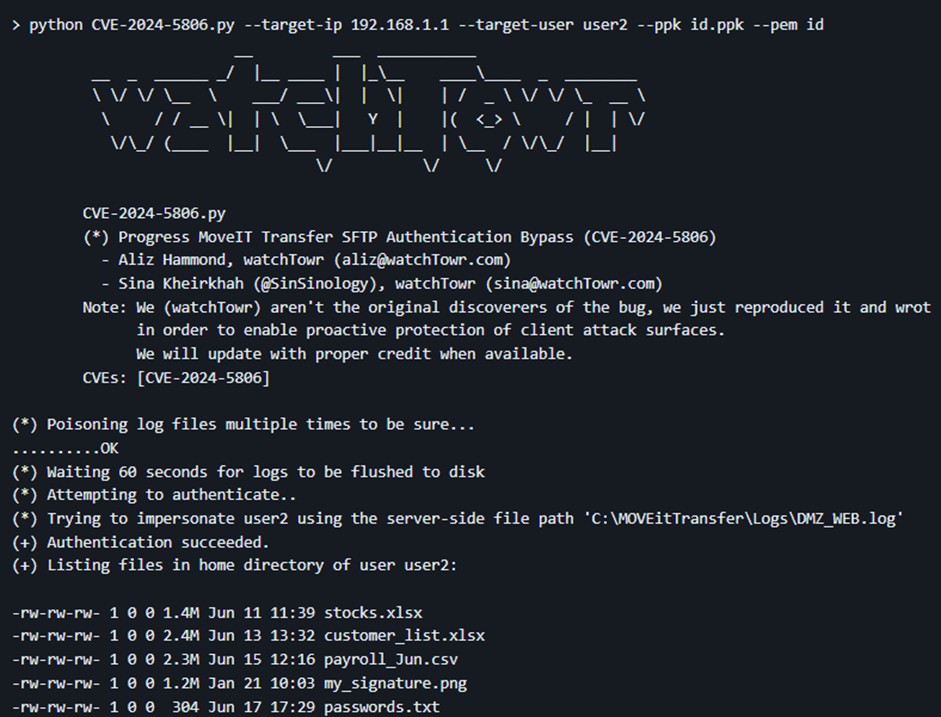
Considering the recent history, a spontaneous question arises: will the cl0p ransomware actor exploit this vulnerability again? The cl0p gang, known for using the CVE-2023-34362 vulnerability for devastating attacks, might see CVE-2024-5806 as a new opportunity.
With their proven experience and the availability of a POC, there is a high risk that cl0p or similar groups might attempt to exploit this new security flaw.
Cl0p is one of the most feared and sophisticated ransomware gangs in the cybersecurity landscape. This criminal group is known for conducting devastating attacks against numerous high-profile organizations using advanced techniques and critical vulnerabilities like CVE-2023-34362 in Progress MOVEit Transfer. Cl0p ransomware is widely believed to have origins in Russia or former Soviet Union countries. Evidence indicates that the group members speak Russian and operate in time zones compatible with this region. However, like many cybercriminal activities, the exact geographic location of the group’s members can be challenging to determine with certainty.
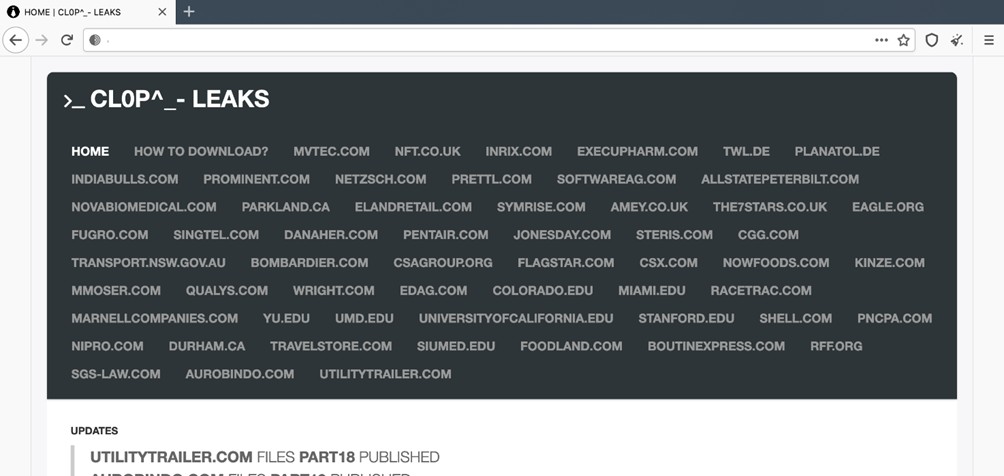
The cl0p ransomware gang uses a set of highly sophisticated techniques, tactics, and procedures to conduct their attacks. Below are the main TTPs associated with the group:
The discovery of the CVE-2024-5806 vulnerability in Progress MOVEit Transfer represents a serious risk to the security of business information. The presence of a POC for the exploit further increases the threat, making it crucial for organizations to take immediate preventive measures. The possibility that the cl0p ransomware group might exploit this new vulnerability cannot be excluded, making vigilance and preparation even more important. Cybersecurity is an ongoing battle, and only through prevention and rapid response can companies protect their most valuable assets: data.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
