
Threat intelligence has many fields of application, starting from control of infrastructures using automation processes to security increasing the perimeter of applications and solutions in general. One of the most common applications of this concept is antimalware tools, which enterprise antivirus solutions are preferable rather than open sources due to two main aspects: enterprise solutions are covered by official support in case of any type of problem (even if this is not always true due to different type of subscriptions) and signatures in the enterprise tools are more precise and updated than open sources. What can we do to perform a significant growth in open source technologies?

I have analyzed one of the most common open source antivirus solutions, ClamAV. This antimalware is deployable on Linux, Windows and Mac and it uses its own signatures and definitions. Only these? No, even the signature upload process is open source and antimalware definition databases can be created from custom sources. In this flow, threat intelligence can help us to receive IOC from open source feeds, centralize them in a orchestrator solution like MISP, an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threats about cyber security incidents analysis and malware analysis.
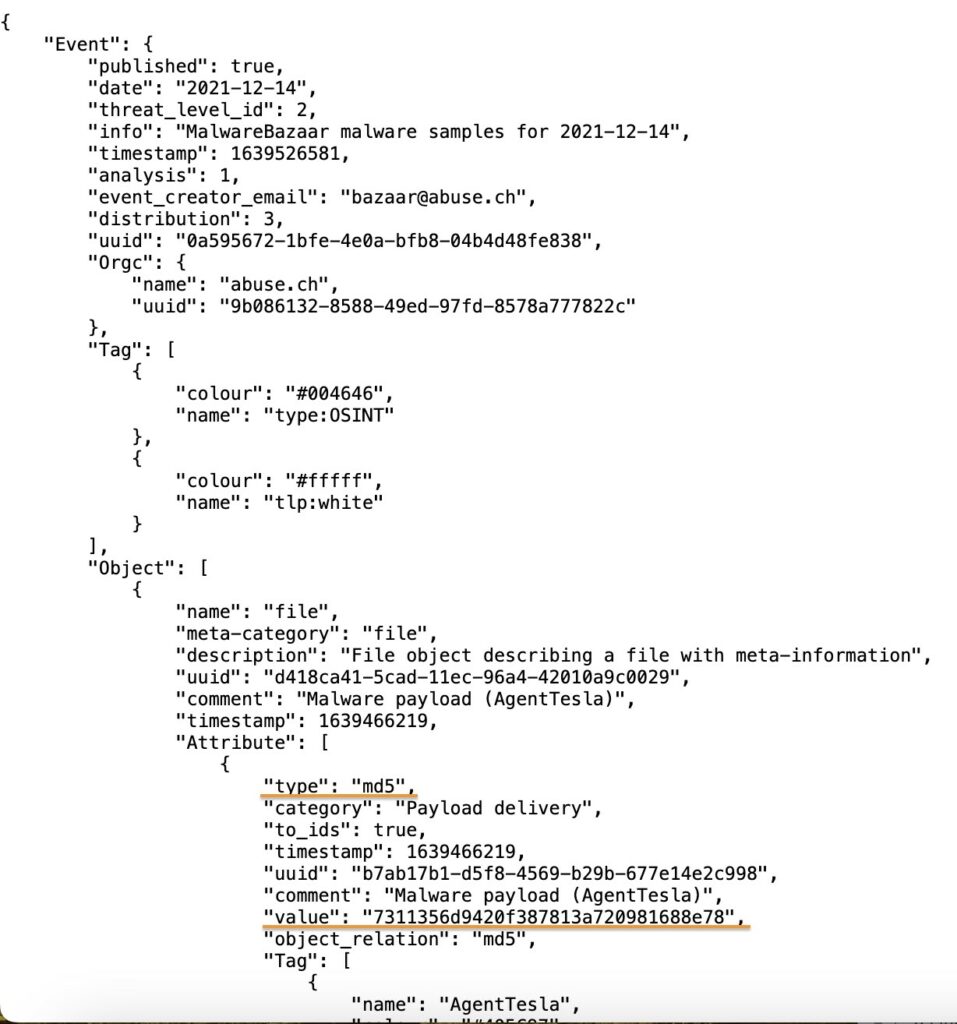
Using its query API system, we can extract from MISP the IOC events that include attributes with SHA256 or MD5 type, considering the value field. Following official documentation, we can create ClamAV HSB file (hash-based signatures) with the list of SHA256/MD5 values extracted, for example:
7311356d9420f387813a720981688e78:*:AgentTesla:73
This line has the following fields:
Once every HSB file is created, we can packetize them with the ClamAV sigtool command suite to build a CUD file (ClamAV Unsigned Database), importable in the main ClamAV signatures directory and usable next to scanning desired elements. Tuning will be the next process step because a database created can warn us about false positives, but with little work we will have a very useful and powerful open source antimalware solution.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
