
In recent years, the cybersecurity landscape has been marked by ongoing ransomware attacks , with criminal groups constantly evolving to evade defenses. One such group, known as BlackByte, recently returned to action after months of inactivity, reviving its double extortion strategy and introducing a new Data Leak Site (DLS).
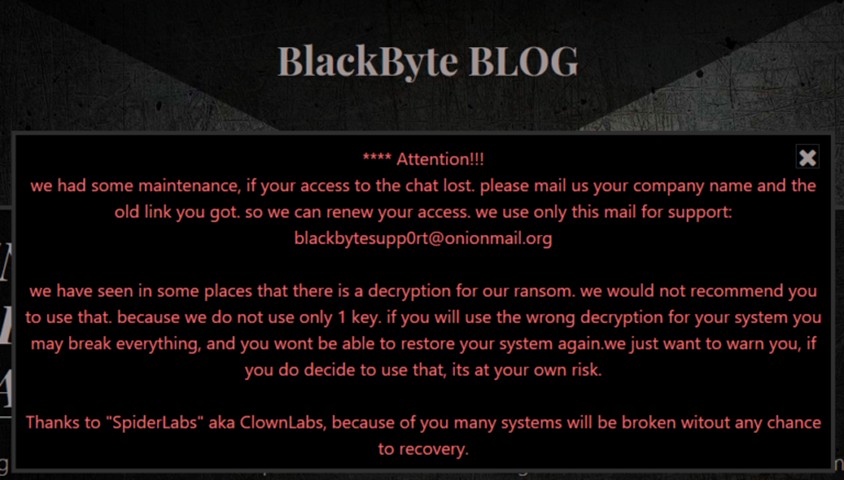
Blackbyte DLS
BlackByte emerged as a significant threat in July 2021, quickly attracting the attention of authorities such as the FBI and the US Secret Service. This group is known to exploit vulnerabilities in computer systems to gain unauthorized access and distribute their ransomware. One of the most common techniques used by BlackByte is the use of known vulnerabilities in Microsoft Exchange servers, a method that has also been exploited by other ransomware groups.
Support Red Hot Cyber through
BlackByte operates under a Ransomware-as-a-Service (RaaS) model, which allows affiliates to use ransomware in exchange for a percentage of profits. This business model allows for a wider spread of ransomware and greater difficulty in tracing and stopping the group’s operations. BlackByte affiliates can customize attacks and leverage ransomware to target specific targets.
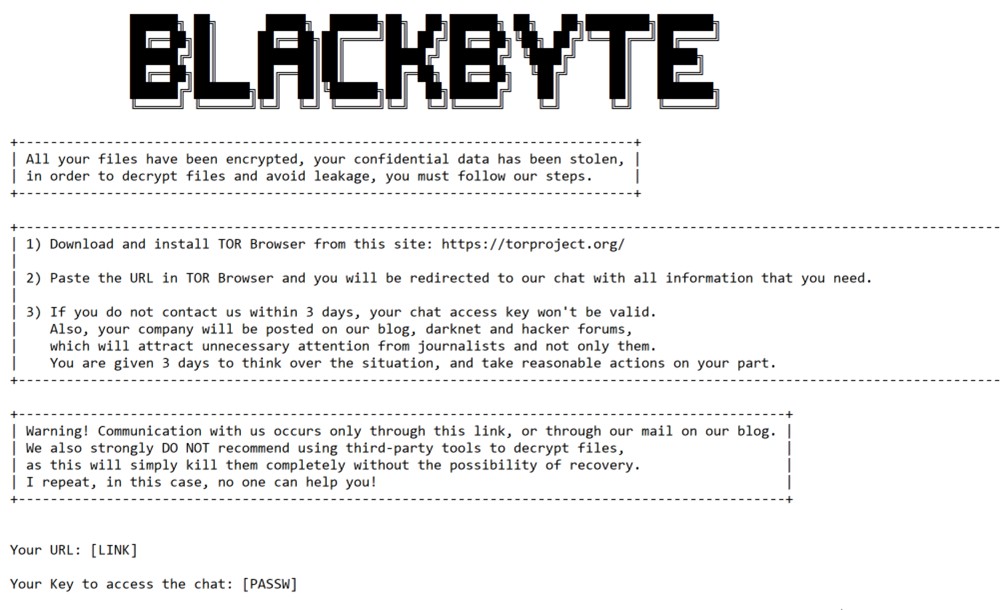
Ransomnote by the Blackbyte group
BlackByte uses a variety of techniques to infiltrate victims’ systems. These include:
After an initial period of activity, the gang made significant changes to their ransomware. For example, an initial version of the ransomware had a vulnerability that allowed victims to decrypt their files without paying the ransom. This vulnerability was quickly patched in subsequent releases, which introduced more complex encryption methods and the use of multiple encryption keys for each attack.
A distinctive feature of BlackByte attacks is double extortion. In addition to encrypting victims’ data, the gang threatens to publish the stolen data on a Data Leak Site (DLS) accessible via Tor. This approach puts double pressure on victims, forcing them to pay to avoid both data loss and reputational damage.
After the last known attack in March 2024, BlackByte disappeared from the radar, leading many to think the group had been dismantled or had ceased operations.
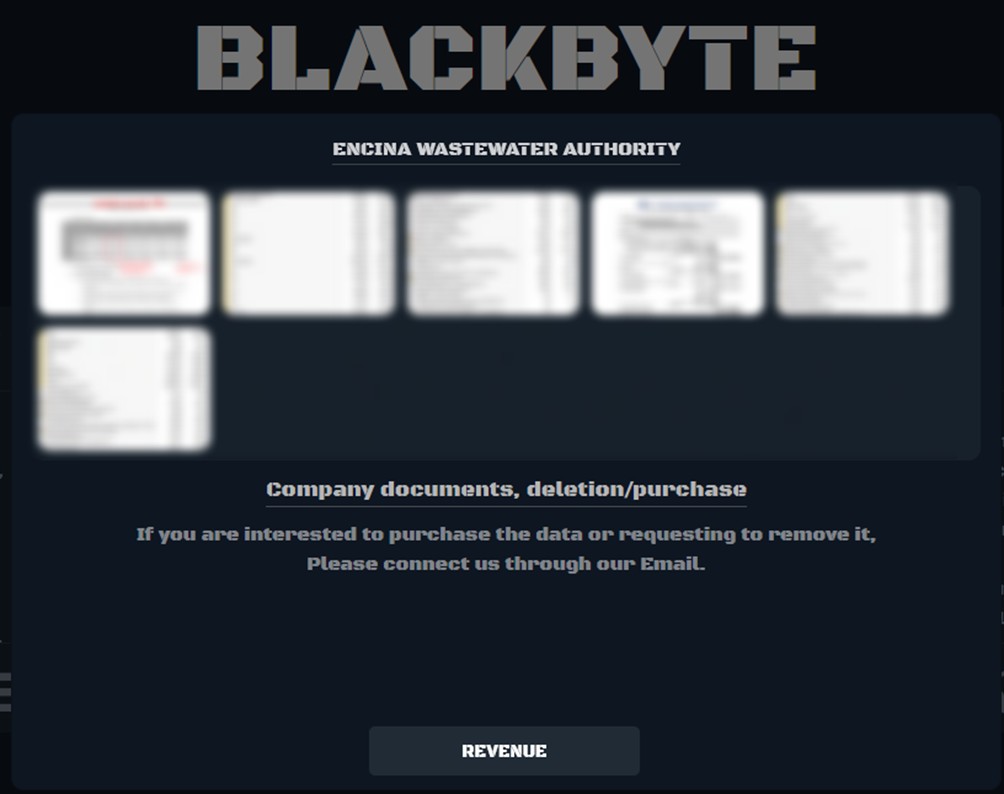
Post appeared on the blackbyte DLS of the last victim of March 2024
However, a recent announcement about their new DLS suggests otherwise. The message (see image) informs that it is now possible to download company files via Tor addresses, with a revamped system that promises to make it easier to view and download stolen data.
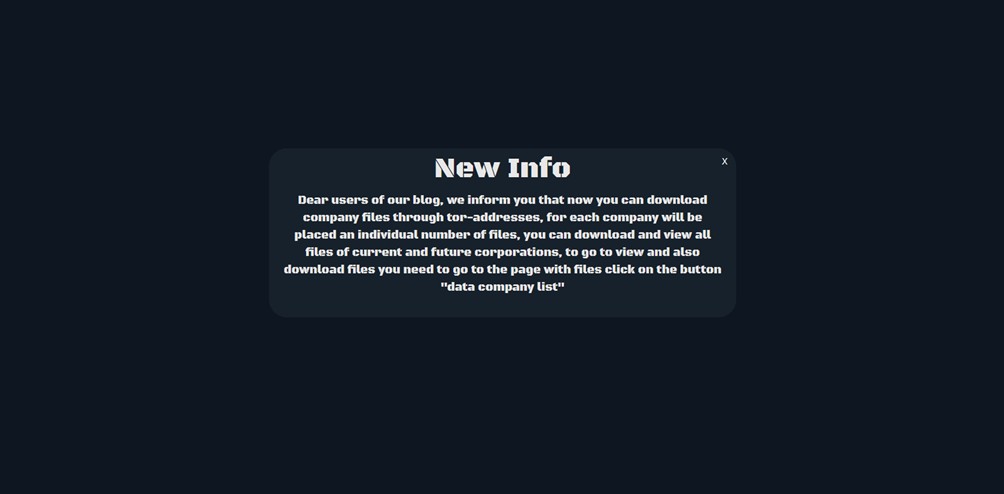
Banner “new info”
BlackByte’s new DLS represents a significant evolution from their previous attempts. The updated platform allows for more intuitive navigation and access to a list of companies with their compromised files. This system, which uses the Tor network to ensure anonymity, allows criminals to operate with greater security and reach a wider audience of potential buyers of sensitive data.
Over the course of its activity, BlackByte has targeted several notable organizations, including:
BlackByte’s return with a revamped strategy highlights the importance of a proactive approach to cybersecurity. Organizations must invest in advanced security solutions, such as network segmentation, continuous anomaly monitoring, and employee training on cybersecurity practices . Furthermore, it is essential to have well-defined and regularly tested incident response plans to minimize damage in the event of an attack.
BlackByte represents one of many threats in the ever-evolving world of cybersecurity. Their return and adoption of a new DLS demonstrates how ransomware groups continue to innovate to maximize their profits. For organizations, threat awareness and taking appropriate security measures are crucial to defend against these increasingly sophisticated attacks.
It remains to be seen how the situation will evolve and what other surprises BlackByte will reserve in the near future. In the meantime, the global cybersecurity community must remain vigilant and collaborate to counter these persistent threats.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
