
In the current modern context where a cyber war is in progress, the concept of cybersecurity awareness and perimeter fortification is increasingly necessary. In this situation, target objectives are spread through all people who can access the network using a simple computer.
User activity control and monitoring have to be strong but they have to leave more comfortable the user experience and the work activity in general. So, a good question: how do I reach it?
There are many tools usable to check, monitor and control user activities, enterprise or open source: the first ones are the most stable, maintained and supported in case of issues, the second ones are totally free in their implementation and modification. I have tried to think a tool that can group the three focal points for user security:
Previous question before starting to write code was simply: what should I want for my security? A tool that should be simple and accessible by everyone, fast and light, deployable through systems and dynamic; furthermore, it should have a set of rules updated and customizable.
Anubi (https://github.com/kavat/anubi) is my implementation as EDR solution; it is developed using Python and it is available for Linux and MacOS (Windows will be soon); installation flow for deployment is described in my repository and basically it can be summarized as:
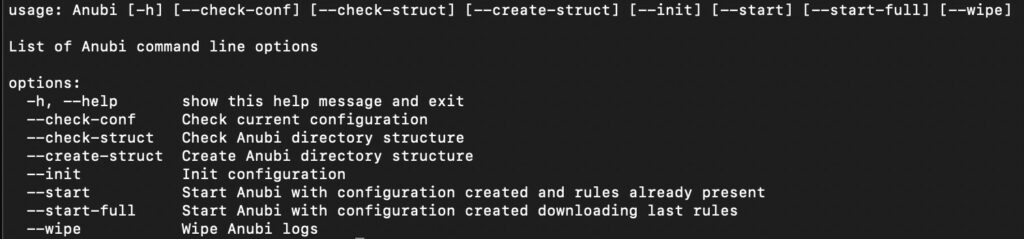
During its first start, Anubi will ask for internal set up, as:
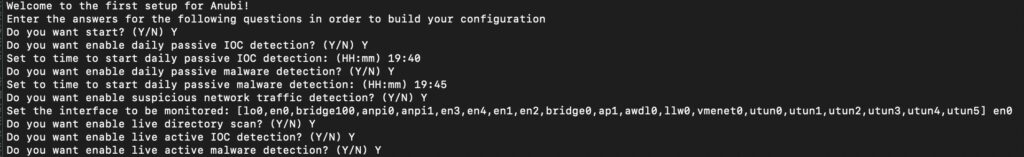
Anubi runs itself as a loop, spawning threads dedicated to the actions described previously, allowing the parallel execution of the controls.
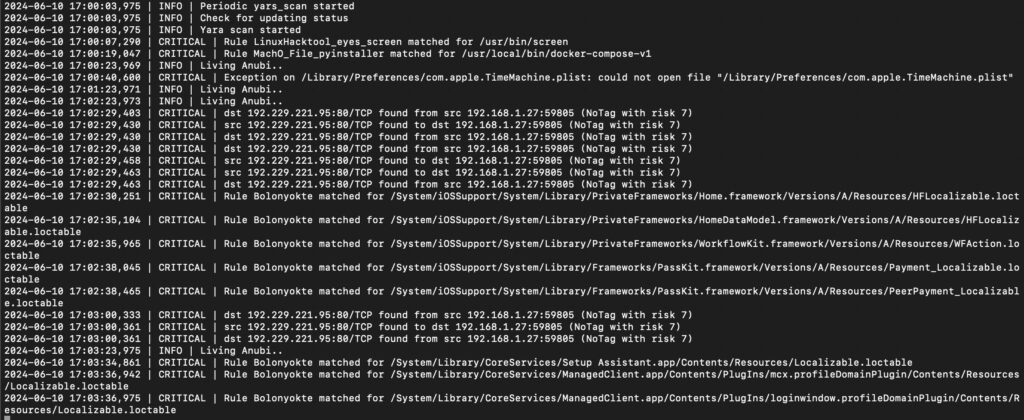
Anubi saves its results in log files directly and for IOC/Malware scans in reports directory; the API system is used to interact with Anubi and the WebUI helps to simplify operations on-demand and allows a stable tool with restart needed.
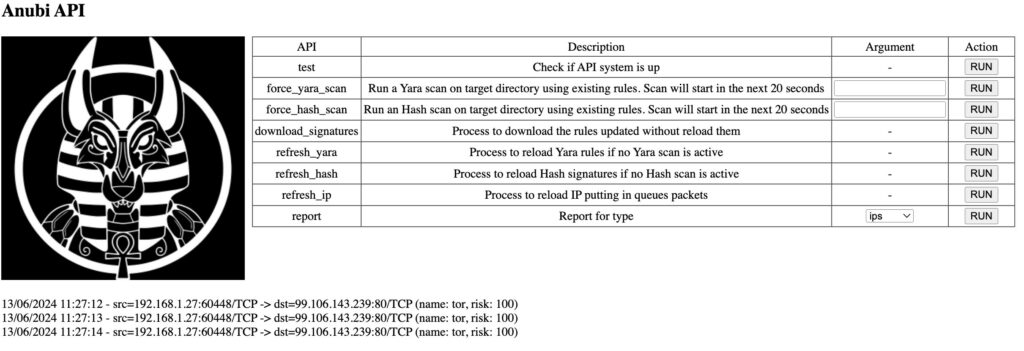
Anubi aims to be helpful and oriented to be used by a large set of people, more or less skilled, for its dynamism and simplicity; it is very light, runnable by different systems and fully made in Italy.
Happy Hack!
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
