
Recently, alarming news has emerged on a well-known underground forum regarding alleged data breaches of the United States Department of Defense and the National Security Agency (NSA). The announcements, posted by the user “Gostingr,” have raised concerns among users and cybersecurity experts, particularly due to the sensitive nature of the information involved.
According to the post published by the user, the compromised data includes 325,498 lines containing names, emails, phone numbers, and addresses. The file, in CSV format, was compressed into a ZIP archive with a size of 6.3 MB, while the uncompressed size reaches 14.6 MB.
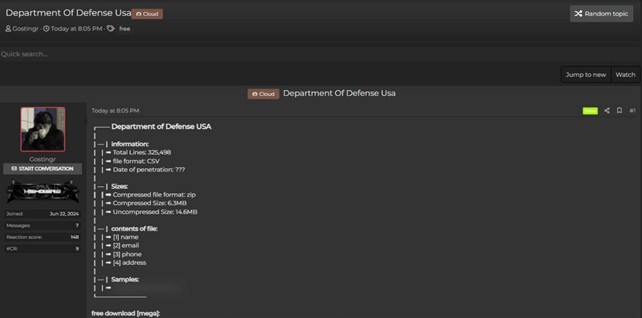
The malicious actor did not provide a precise date of the breach, leaving an uncertainty about the exact moment the Department of Defense system was compromised.
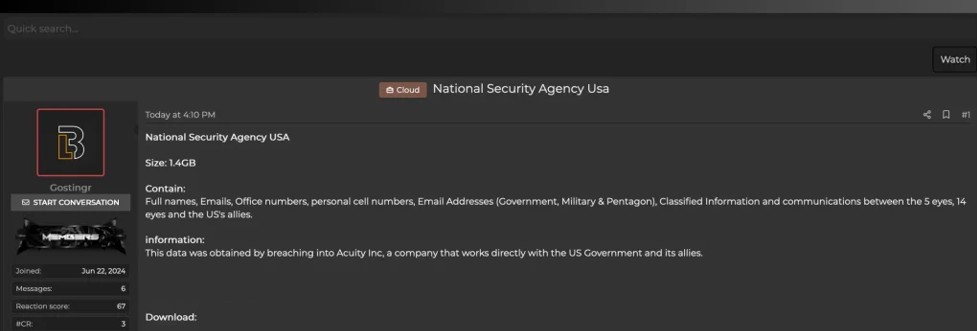
In a further post, the same actor claimed to have breached the data of the National Security Agency (NSA) of the United States. According to the report, the size of the compromised file is 1.4 GB and contains full names, emails, office phone numbers, personal cell phone numbers, government, military, and Pentagon email addresses. Additionally, the data is said to include classified information and communications between the “5 Eyes,” “14 Eyes,” and the US allies. This breach allegedly occurred by infiltrating the systems of Acuity Inc., a company that works directly with the US government and its allies.
The implications of such breaches are extremely serious. The personal information of hundreds of thousands of individuals could be used for various malicious purposes, including identity theft, phishing, and other forms of cyber-attacks. Moreover, the fact that these data belong to organizations of national importance such as the Department of Defense and the NSA makes the situation even more critical, as they might involve data of military personnel and government employees.
At the moment, it is not possible to confirm the accuracy of the breaches. Neither the Department of Defense nor the NSA of the United States has yet released any official press statements regarding the incidents. Without an official declaration, it is difficult to determine the actual extent of the damage and whether the information disseminated on the forum is authentic.
These episodes once again highlight the importance of cybersecurity and the protection of sensitive data. Organizations, especially those handling information of national importance, must adopt stringent security measures to prevent such incidents.
Until further details and official confirmations are available, these reports should be treated as intelligence sources and closely monitored for any updates. In the meantime, it is advisable for potentially involved individuals to take precautions to protect their personal information and remain vigilant against possible phishing attempts or other fraudulent activities.
As is our custom, we always leave room for a statement from the company should they wish to provide updates on the matter. We would be happy to publish such information with a specific article highlighting the issue.
RHC will monitor the evolution of the situation in order to publish further news on the blog should there be substantial updates. If there are individuals informed about the facts who wish to provide information anonymously, they can use the encrypted whistleblower email.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
