2149 BREAK THE SPHERE! The RHC & Hack The Box CTF at the RHC Conference 2026
In 2149, the world is no longer divided into nations, but into mega Autonomous City-States, hyper-technological urban giants competing for resources, data, and geopolitical power while the entire worl...
RHC Interviews Anubis Ransomware: Their View on RAMP, LockBit and the RaaS “Market”
Author: Luca Stivali, Raffaela Crisci, Lorenzo Nardi During the preliminary exchange leading up to the interview, Anubis expressed a very clear position regarding the collapse of several historical pl...
The Most Dangerous Sentence in IT: “Don’t Worry, They’re on Different VLANs”
In the world of IT, there is one expression that lowers defenses more effectively than any zero-day exploit: “Don’t worry, they’re on different VLANs.” It is a reassuring phrase, usually spoken in goo...
Cloud logs under threat? The method that exposes attackers early
You know that feeling when cloud alerts keep piling up and you’re left wondering whether it’s just background noise or something genuinely bad unfolding? Yeah, it happens all the time. Monitoring syst...
Supply Chain Attack: How Notepad++ Was Compromised via CVE-2025-15556
In cybersecurity, we often focus on finding complex bugs in source code, ignoring the fact that end-user trust is built on a much simpler foundation: a download link. The Notepad++ incident, now class...
Microsoft Office under attack: the bug needs to be patched to prevent Russian espionage.
In recent days, APT28 , a well-known Russian-linked hacker group, has intensified its attacks by exploiting a vulnerability in Microsoft Office. The flaw, classified as CVE-2026-21509, was disclosed b...
Goodbye to NTLM! Microsoft is moving towards a new era of authentication with Kerberos
For over three decades, it has been a silent pillar of the Windows ecosystem. Now, however, NTLM ‘s time seems definitively over. Microsoft has decided to initiate a profound transition that marks the...
The world’s first humanoid robot store has opened in China. Will we be ready?
At ten o’clock in the morning, in Wuhan, two 1.3-meter-tall humanoid robots begin moving with precision. They turn, jump, and follow a rhythm. It’s the opening signal for the country’s first 7S humano...
Douglas Engelbart was born today: the man who saw and invented the digital future.
Sometimes, when you think about it, you wonder how we take the world around us for granted. Like, we click, scroll, type, and it all seems so natural, as if it’s always been there. But no, there was s...
WhatsApp gets a makeover: “Paranoia” mode arrives (and no, it’s not for everyone).
WhatsApp has decided to toughen up. Not for everyone, not always, but when needed. The decision comes against a backdrop of a now-familiar climate: increasing cyber attacks, espionage that no longer m...
Latest news
Jupiter, the exascale supercomputer that aims to revolutionize AI in Europe
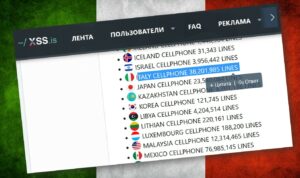
38 million Italian phone numbers for sale on the dark web. It’s smishing!
Apitor, the first robot that helps children do their homework and the whistleblower for China
Hackable restaurant robots could serve sushi… at the attacker’s home.
LECS powered by Cyber Evolution: la prima black box NDR completamente Made in Italy
Figure 02, the robot that loads the dishwasher with precision
If Flash is dead, here’s the SVG Assassin! Phishing 2.0 is in high definition.
The Dark Side of Windows Drivers: How to Steal Data While Ignoring EDR
GhostRedirector: The Black SEO Redirect Campaign That Manipulates Search Engines
Attackers are using Velociraptor for cyberattacks. Rapid7 is aware
Underwater warfare is upon us! Will Chinese cable cutters pose a global threat?
The European Union General Court “upholds” the transfer of personal data to the United States. For now
Nvidia invests $1 billion in Nokia to develop 6G networks with AI
Silvia Felici - October 31st, 2025
Linux and gaming: an increasingly reliable combination
Redazione RHC - October 31st, 2025
Russian Interior Ministry officials arrested the creators of the Medusa malware
Sandro Sana - October 31st, 2025
Atroposia: The MaaS platform that provides a Trojan with a vulnerability scanner
Massimiliano Brolli - October 30th, 2025
0day as weapons: sold 8 US defense 0day exploits to Moscow
Agostino Pellegrino - October 30th, 2025
Critical vulnerability in Blink: a website can block all Chromium-based browsers
Massimiliano Brolli - October 30th, 2025
Trump-Xi Summit: A Truce That Doesn’t Benefit Europe
Redazione RHC - October 30th, 2025
Cloud yes or Cloud no: When the Digital Sky Darkens
Redazione RHC - October 30th, 2025
Taiwan: Up to 7 years in prison for those who damage undersea cables
Sandro Sana - October 30th, 2025
95% of companies believe they’re ready for ransomware. But only 15% actually are!
Redazione RHC - October 30th, 2025
Discover the latest critical CVEs issued and stay updated on the most recent vulnerabilities. Or search for a specific CVE