Ultime news
Ukrainian Hacker Charged in Major Ransomware Attacks
The Rise of Digital Walls: How National Sovereignty Threatens Global Internet
Critical MongoDB Vulnerability Exposed: CVE-2025-14847
Smart TV Spying: Major Brands Accused of Collecting User Data
Phishing Campaigns Exploit File Sharing Services
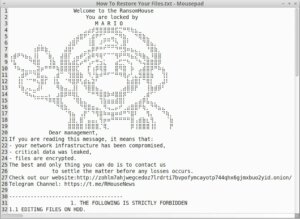
RansomHouse Ransomware Upgraded: Enhanced Encryption Threat
FreeBSD 15.0: Discover the Power of This Unix-like Operating System
Redazione RHC - December 6th, 2025
Cloudflare Blocks AI Bots: The Future of Internet Economy at Stake
Redazione RHC - December 5th, 2025
React2Shell Vulnerability: 8.7M Servers at Risk – CVE-2025-55182
Agostino Pellegrino - December 5th, 2025
Cloudflare Just Broke the Internet… Again. Centralization Risks Exposed
Redazione RHC - December 5th, 2025
Chinese Cyber Spies Use Brickstorm Malware to Infiltrate Critical Networks
Redazione RHC - December 5th, 2025
Splunk Enterprise Vulnerability: CVE-2025-20386 and CVE-2025-20387
Agostino Pellegrino - December 5th, 2025
Apache HTTP Server Update Fixes Critical Security Vulnerabilities
Redazione RHC - December 5th, 2025
Cyber Insurance: Why Basic Hygiene Matters
Agostino Pellegrino - December 5th, 2025
Meta AI WhatsApp Investigation
Redazione RHC - December 5th, 2025
Gulf States’ Digital Transformation: A New Era of Innovation and Security
Matteo Giada - December 5th, 2025
Discover the latest critical CVEs issued and stay updated on the most recent vulnerabilities. Or search for a specific CVE
Featured Articles
 Cybercrime
CybercrimeA recent leak revealed 149 million logins and passwords exposed online , including accounts for financial services, social media, gaming, and dating sites. The discovery was made by researcher Jeremiah Fowler and shared with ExpressVPN.…
 Cybercrime
CybercrimePixelCode began as a research project exploring a hidden technique for storing binary data within images or videos . Instead of leaving a plaintext executable, the file is converted into pixel data, transforming each byte…
 Cyber News
Cyber NewsSecurity researchers have recently observed a worrying evolution in the offensive tactics attributed to North Korean-linked actors as part of the campaign known as Contagious Interview : no longer simple fake job interview scams, but…
 Cyber News
Cyber NewsKhaby Lame, the world’s most followed Italian creator and now a global social media icon, has taken a step that could mark a turning point in the history of the digital economy. According to several…
 Cyber News
Cyber NewsThe critical vulnerability recently added to the Cybersecurity and Infrastructure Security Agency (CISA) catalog of known exploited vulnerabilities (KEVs) affects the Broadcom VMware vCenter Server and is being actively exploited by malicious hackers to breach…